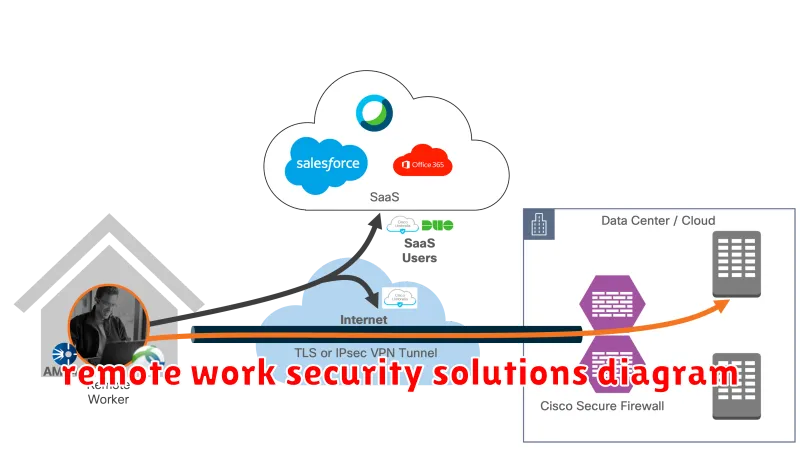
In today’s rapidly evolving business landscape, the remote workforce has become the norm. While remote work offers numerous advantages, it also presents unique security challenges. As organizations embrace distributed teams, ensuring data security and employee safety is paramount. Securing the remote workforce requires a multifaceted approach that encompasses best practices, robust solutions, and a proactive security culture.
This article delves into the essential strategies for safeguarding your remote workforce and protecting your organization’s sensitive data. From implementing strong authentication measures and data encryption to adopting zero-trust security principles and employee training, we will explore practical solutions to address the evolving threats faced by remote teams.
The Rise of Remote Work and Security Challenges
The global pandemic has irrevocably shifted the landscape of work. The rapid adoption of remote work has brought unprecedented flexibility and convenience, but it has also introduced a new set of security challenges. As more organizations embrace remote work, securing the remote workforce becomes increasingly critical. The threat of cyberattacks, data breaches, and other security risks is more prevalent than ever before.
The rise of remote work has presented several security challenges for businesses. These challenges include:
- Increased Attack Surface: Remote workers access company networks from various locations and devices, expanding the attack surface.
- Unsecured Home Networks: Many employees may not have secure home networks, creating vulnerabilities for hackers to exploit.
- Device Security: Organizations struggle to maintain control over employee devices, raising concerns about data security.
- Phishing and Social Engineering: Remote workers are more susceptible to phishing scams and social engineering attacks due to isolation and limited communication.
- Data Leakage: Employees working remotely may unintentionally leak sensitive information, especially when using personal devices or public Wi-Fi networks.
These challenges underscore the need for comprehensive security strategies that address the unique vulnerabilities of remote work environments.
Essential Security Measures for Remote Workers
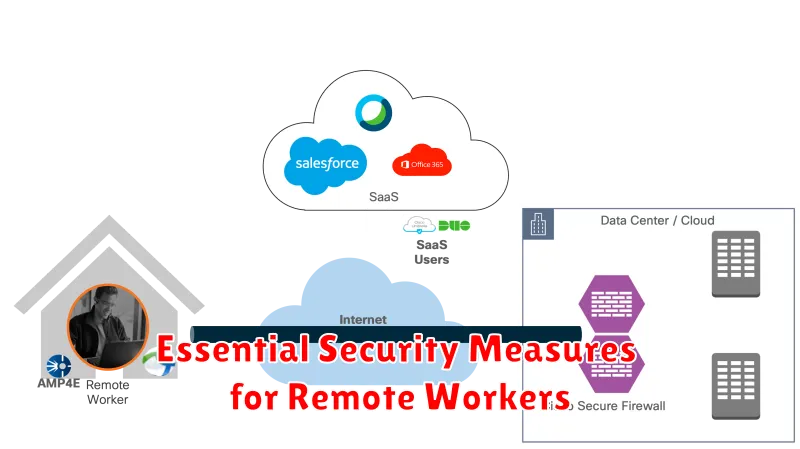
The shift to remote work has brought many benefits, but it has also introduced new security challenges. As more companies embrace remote work, it’s crucial to implement robust security measures to protect sensitive data and systems. Here are some essential security measures for remote workers:
Strong Passwords and Multi-Factor Authentication (MFA)
Strong passwords are the first line of defense. Encourage employees to use complex passwords and enable Multi-Factor Authentication (MFA) for all accounts. MFA adds an extra layer of security by requiring users to provide additional verification, such as a code sent to their phone, before granting access.
Secure Networks and VPNs
Remote workers should only connect to secure networks. Using a Virtual Private Network (VPN) encrypts data traffic, making it difficult for hackers to intercept sensitive information when using public Wi-Fi or insecure networks.
Device Security
Ensure remote workers use company-approved devices or have their personal devices properly secured. This includes installing antivirus software, keeping operating systems and applications up to date, and enabling device encryption.
Data Security and Encryption
Remote workers handle sensitive data, so it’s vital to implement strong data security practices. Use data encryption for all sensitive information, whether stored locally or in the cloud.
Security Awareness Training
Regular security awareness training is essential. Educate remote workers on phishing scams, social engineering tactics, and best practices for handling sensitive information. Encourage them to report any suspicious activities immediately.
Endpoint Security and Monitoring
Implement endpoint security solutions to protect company devices from malware and other threats. Monitor endpoint activity to detect suspicious behavior and respond quickly to security incidents.
Secure Communication
Use secure communication channels for internal communication and collaboration. This includes using encrypted email, instant messaging platforms, and video conferencing tools.
By implementing these essential security measures, companies can help ensure the safety and security of their remote workforce, protect sensitive data, and maintain business continuity in the evolving world of remote work.
Implementing a Secure Access Policy
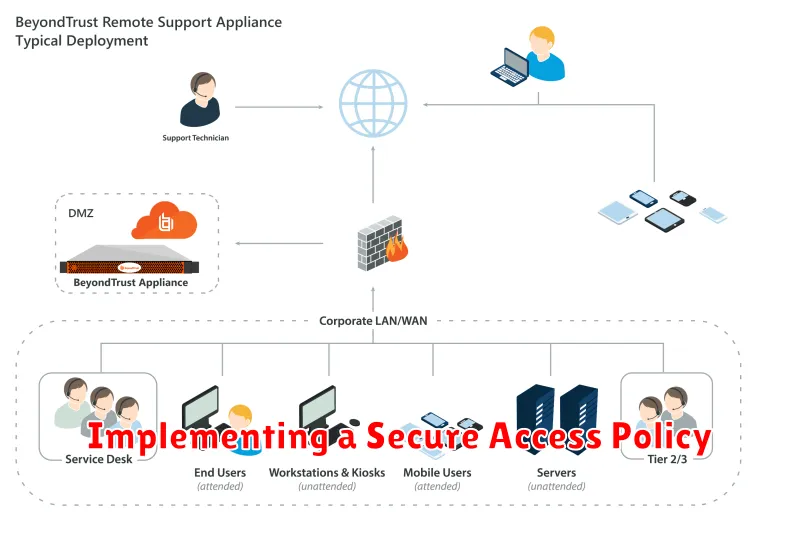
In today’s increasingly remote workforce, securing access to company resources is crucial. Implementing a comprehensive and robust access policy is essential to protect sensitive data and ensure business continuity.
A strong access policy should cover several key aspects, including:
- Authentication and Authorization: Employ multi-factor authentication (MFA) to verify user identities. Implement granular authorization controls to restrict access to specific resources based on user roles and responsibilities.
- Device Security: Enforce secure configurations on all devices accessing company resources, including laptops, smartphones, and tablets. Utilize mobile device management (MDM) solutions to enforce policies, monitor device health, and remotely wipe data if necessary.
- Network Security: Implement a virtual private network (VPN) to encrypt all data transmitted over public networks. Employ firewalls and intrusion detection systems to protect against malicious traffic.
- Data Encryption: Encrypt sensitive data both at rest and in transit. Use encryption tools to protect data stored on devices, in the cloud, and during transmission.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities. Regularly review and update access policies to reflect evolving threats and technologies.
By implementing a comprehensive and secure access policy, organizations can effectively safeguard their data, maintain business continuity, and build a robust security posture in the remote work environment.
Protecting Sensitive Data in a Remote Environment
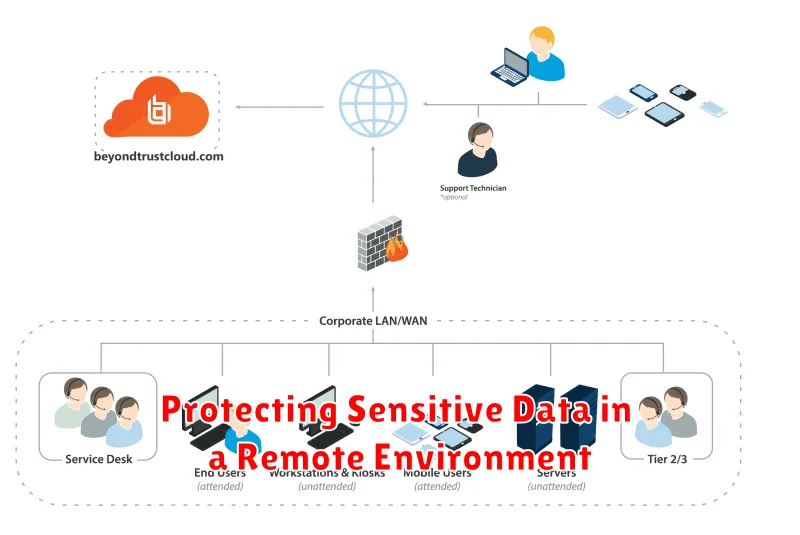
In today’s digital age, remote work has become increasingly prevalent, bringing with it new challenges in protecting sensitive data. As employees access company systems and data from various locations, it’s crucial to implement robust security measures to safeguard against potential threats.
One of the primary concerns is data breaches. With remote access, attackers can exploit vulnerabilities in personal devices, home networks, or public Wi-Fi to gain unauthorized access to sensitive information. To mitigate this risk, organizations must implement a multi-layered security approach, including:
- Strong authentication: Enforce strong passwords or multi-factor authentication (MFA) to prevent unauthorized access to company systems.
- Data encryption: Encrypt sensitive data both in transit and at rest, making it unreadable to unauthorized individuals.
- Regular security updates: Ensure all devices, operating systems, and software are up-to-date with the latest security patches and updates.
- Secure remote access solutions: Utilize VPNs (Virtual Private Networks) or other secure remote access technologies to create a secure connection between remote devices and company networks.
Employee awareness is also crucial in protecting sensitive data. Organizations should provide comprehensive training to employees on data security best practices, including safe browsing habits, strong password management, and reporting suspicious activities. Encouraging a culture of security awareness helps minimize human error, which is often a significant factor in data breaches.
Beyond technical solutions, implementing data loss prevention (DLP) measures is vital. DLP software can monitor data usage and prevent sensitive information from leaving the company network without authorization. This includes identifying and blocking attempts to send confidential data through personal email accounts or unauthorized cloud storage services.
By implementing these best practices and solutions, organizations can effectively protect sensitive data in a remote environment, ensuring the security and integrity of their information assets while empowering employees to work remotely with confidence.
The Role of VPNs in Remote Work Security
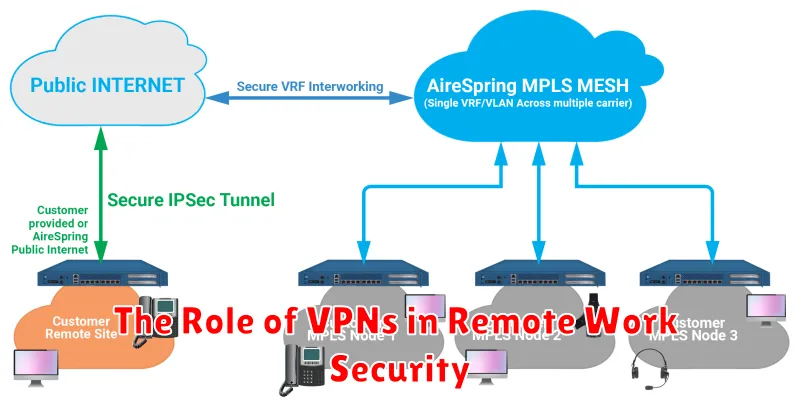
As remote work becomes increasingly common, ensuring the security of your workforce is crucial. One of the most effective tools for securing remote employees is a Virtual Private Network (VPN). A VPN creates a secure, encrypted connection between a user’s device and a server, effectively masking their IP address and location. This makes it difficult for hackers to intercept sensitive data or track online activity.
VPNs play a vital role in protecting remote work security by:
- Data Encryption: VPNs encrypt all data transmitted between the user’s device and the server, making it unreadable to unauthorized individuals.
- Secure Access to Company Networks: VPNs allow employees to access company networks securely from anywhere in the world, as if they were physically present in the office.
- Protection from Public Wi-Fi: VPNs provide a secure connection even when using public Wi-Fi hotspots, which are often vulnerable to security threats.
- Increased Privacy and Anonymity: VPNs mask a user’s IP address and location, making it harder for websites and advertisers to track their online activity.
In conclusion, VPNs are a critical component of a comprehensive remote work security strategy. By providing secure, encrypted connections and protecting sensitive data, they enable businesses to maintain a secure and productive remote workforce.
Endpoint Security for Remote Devices
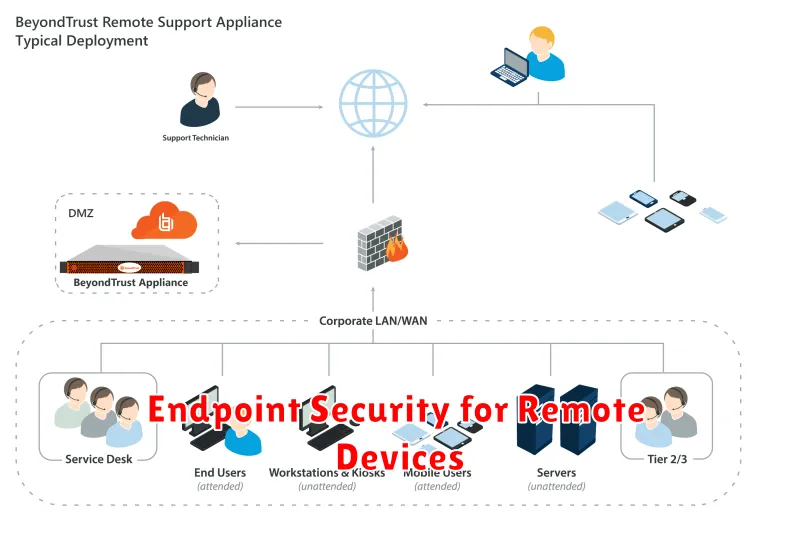
As more companies embrace remote work, the importance of securing remote devices has never been more critical. Endpoint security encompasses the measures taken to protect company data and resources on user devices like laptops, desktops, smartphones, and tablets. With a dispersed workforce, it’s essential to have a robust endpoint security strategy in place to mitigate the growing threat of cyberattacks.
Here are some key elements of endpoint security for remote devices:
1. Endpoint Detection and Response (EDR)
EDR solutions are essential for proactive threat detection and response. They continuously monitor endpoints for malicious activity and suspicious behavior. EDR allows for rapid response and containment, minimizing damage from attacks.
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before granting access to company resources. This can include a password, a one-time code sent to their phone, or a fingerprint scan, making it significantly harder for unauthorized individuals to gain access.
3. Data Loss Prevention (DLP)
DLP tools help prevent sensitive data from leaving the corporate network. They can monitor and control data transfers, block unauthorized access, and encrypt sensitive files. DLP ensures that even if a device is compromised, confidential data remains protected.
4. Vulnerability Management
Regularly scanning endpoints for vulnerabilities is crucial. Patches and updates should be applied promptly to address known weaknesses and prevent exploitation. Automated vulnerability scanning tools can streamline this process and ensure timely mitigation.
5. Endpoint Encryption
Encrypting data on endpoints ensures that even if a device is lost or stolen, the data remains inaccessible to unauthorized individuals. Full disk encryption (FDE) and file-level encryption are effective methods to protect sensitive information.
6. Strong Password Policies
Enforce strong password policies across all devices. This includes requiring complex passwords with a mix of characters, setting regular password expiration dates, and discouraging the use of common or easily guessed passwords. A password manager can help employees manage their passwords securely.
By implementing these endpoint security measures, companies can effectively protect their remote workforce and mitigate the risks associated with data breaches and cyberattacks. Investing in robust endpoint security solutions is essential for safeguarding sensitive data and maintaining business continuity in today’s increasingly distributed work environment.
Collaboration and Communication Security
As the remote workforce continues to grow, securing collaboration and communication tools becomes paramount. Organizations must implement robust security measures to protect sensitive data and prevent unauthorized access. Here are some best practices and solutions to enhance collaboration and communication security:
Strong Authentication and Access Control
Implement multi-factor authentication (MFA) for all collaboration and communication platforms. This adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a one-time code. Also, establish granular access controls to restrict user permissions based on their roles and responsibilities.
Data Encryption
Encrypt data at rest and in transit. This ensures that sensitive information remains protected even if devices are lost or stolen. Use encryption protocols like Transport Layer Security (TLS) for communication and encrypt files stored in cloud storage.
Secure Communication Channels
Utilize secure communication channels, such as encrypted messaging apps and virtual private networks (VPNs). Avoid using public Wi-Fi for sensitive data transmissions and encourage employees to use company-approved devices and applications.
Regular Security Audits and Training
Conduct regular security audits to identify vulnerabilities and implement necessary safeguards. Provide employees with ongoing security awareness training to educate them about best practices, phishing scams, and social engineering attacks.
Security Monitoring and Threat Detection
Implement security monitoring tools to detect suspicious activities and potential threats in real-time. These tools can analyze network traffic, user behavior, and system logs to identify anomalies and alert security teams to potential breaches.
Collaboration and Communication Platform Security
Choose collaboration and communication platforms that prioritize security. Look for platforms that offer features such as end-to-end encryption, secure file sharing, and compliance with industry standards, such as ISO 27001.
By implementing these best practices and solutions, organizations can effectively secure their collaboration and communication tools, mitigating risks and protecting sensitive data in a remote work environment.
Training and Awareness for Remote Employees

One of the most crucial aspects of securing a remote workforce is ensuring that employees are adequately trained and aware of potential threats. A comprehensive training program that covers essential security topics is vital for minimizing risk. Phishing awareness is paramount, as employees are often the first line of defense against malicious attacks. Training should emphasize recognizing and avoiding suspicious emails, links, and attachments. Employees should also be educated on password security, including the importance of using strong, unique passwords for all accounts and enabling multi-factor authentication whenever possible.
Data security is another critical aspect of training. Employees should understand their role in protecting sensitive information, including confidential company data and customer details. Training should cover best practices for handling data, such as encrypting sensitive files and avoiding the use of public Wi-Fi for sensitive tasks. Security policies and procedures should be clearly communicated and enforced, ensuring all employees understand their responsibilities and the consequences of non-compliance. Regular security awareness campaigns can further reinforce best practices and keep employees informed about emerging threats.
Training should be engaging and interactive, using real-world examples and simulations to illustrate potential threats. Regular updates and refresher courses are essential, especially as new threats and vulnerabilities emerge. It is also important to provide employees with a safe space to report suspicious activity or ask questions. A culture of security awareness is critical for maintaining a strong security posture in a remote work environment. By empowering employees with the knowledge and skills they need, businesses can significantly reduce their risk of cyberattacks and protect their valuable data and reputation.
Monitoring and Incident Response for Remote Work
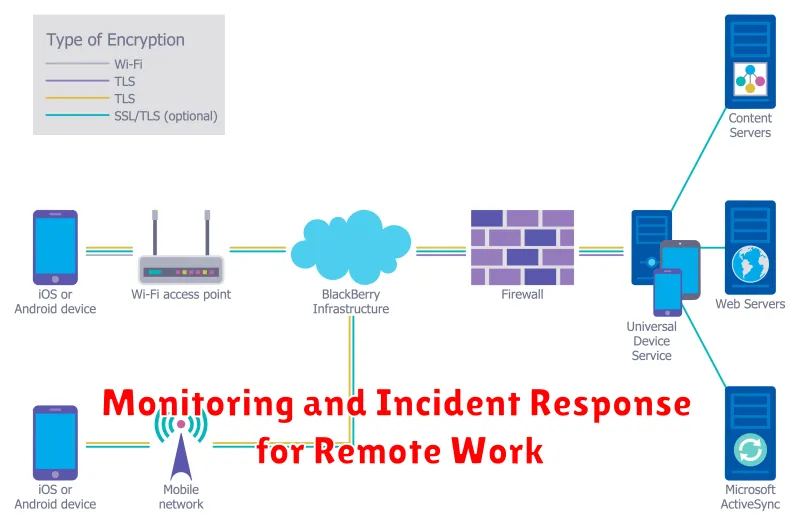
As businesses embrace remote work, the need for robust security measures becomes paramount. While remote work offers flexibility and cost savings, it also presents unique challenges for monitoring and incident response. Traditional security solutions designed for on-premises environments may not be sufficient to address the evolving threats faced by remote workforces. This article explores best practices and solutions for effective monitoring and incident response in a remote work context.
Real-time Monitoring is crucial to detect and mitigate security incidents promptly. Organizations should implement centralized logging and monitoring solutions that provide visibility across all remote endpoints, networks, and applications. This includes monitoring for suspicious activities, unauthorized access attempts, and malware infections. Advanced threat detection tools, including behavioral analytics and machine learning, can help identify anomalies and potential threats that traditional security tools might miss.
Incident Response Plans are essential for handling security incidents effectively. These plans should outline clear procedures for identifying, containing, and resolving security incidents. The plans should include designated roles and responsibilities, communication protocols, and escalation procedures. Regular incident response drills and simulations can help ensure that teams are prepared to respond effectively to real-world security incidents.
Security Awareness Training is paramount for remote workers. Employees should be educated about common security threats, best practices for secure remote work, and reporting procedures for suspicious activities. Regular training and phishing simulations can help raise awareness and reduce the likelihood of employees falling victim to social engineering attacks.
Multi-Factor Authentication (MFA) should be mandatory for all remote workers accessing sensitive systems and data. MFA adds an extra layer of security by requiring users to provide two or more forms of authentication, such as a password and a one-time code from a mobile device. This makes it significantly more difficult for unauthorized individuals to gain access to systems even if they compromise a user’s password.
Endpoint Security is essential for protecting remote devices from malware and other threats. Organizations should implement endpoint detection and response (EDR) solutions that provide real-time monitoring and protection for remote devices. EDR solutions can detect and block malicious activities, quarantine infected devices, and provide incident response capabilities. These solutions can also help enforce security policies and ensure that remote devices meet compliance requirements.
Network Segmentation can enhance security by isolating sensitive data and applications from public networks. This can help prevent lateral movement of attackers within a network and reduce the impact of a successful attack. Virtual private networks (VPNs) can provide secure connections between remote workers and company networks, encrypting data transmitted over the internet.
Regular Security Assessments are crucial for identifying vulnerabilities and weaknesses in remote work environments. These assessments should include penetration testing, vulnerability scanning, and security audits. The results of these assessments should be used to improve security controls and reduce the risk of successful attacks.
By implementing these best practices and solutions, organizations can strengthen their security posture and effectively monitor and respond to incidents in remote work environments. The key is to adopt a comprehensive approach that addresses all aspects of security, from endpoint protection to incident response.
Best Practices for Secure Remote Meetings
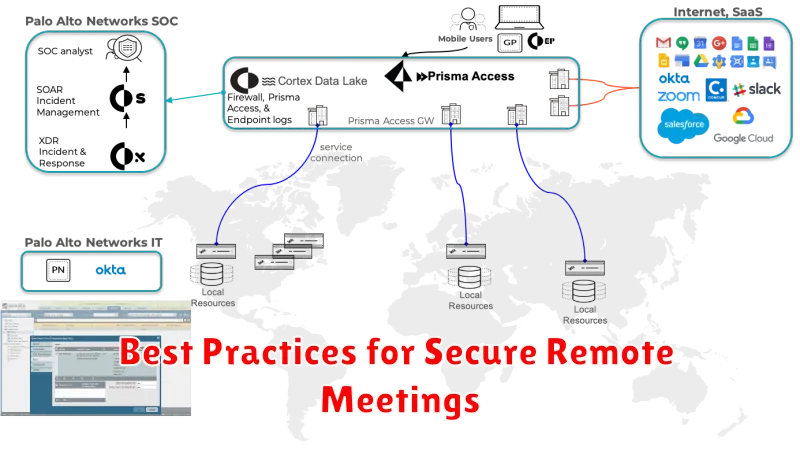
The shift towards remote work has brought about a surge in the use of video conferencing and online meetings. While these tools have enabled seamless collaboration, they also pose new security challenges. Implementing robust security practices for remote meetings is essential to safeguard sensitive information and maintain the integrity of your organization.
Here are some best practices for securing remote meetings:
- Use a reputable video conferencing platform: Opt for platforms that have strong security features, such as end-to-end encryption, two-factor authentication, and regular security updates.
- Create strong meeting passwords: Set strong and unique passwords for each meeting to prevent unauthorized access. Avoid using easily guessable passwords or default settings.
- Enable waiting rooms: This feature allows you to control who joins the meeting and prevents uninvited participants from entering. You can admit participants individually after verifying their identities.
- Restrict screen sharing: Only allow authorized individuals to share their screens during the meeting. This helps to prevent the accidental or intentional sharing of sensitive data.
- Disable recording: If recording is not necessary, disable the recording feature to prevent unauthorized recording of the meeting content.
- Educate participants on security best practices: Train your employees on how to identify and avoid phishing attacks, malicious links, and other online threats that could compromise meeting security.
- Be cautious about external participants: When inviting external participants, verify their identities and ensure that they are legitimate. Use virtual private networks (VPNs) for increased security when accessing public Wi-Fi networks.
By implementing these best practices, organizations can significantly reduce the risk of security breaches during remote meetings. These measures ensure that sensitive information remains confidential, and participants can engage in productive and secure collaborations.
Future-Proofing Your Remote Work Security Strategy
The rise of remote work has brought about a significant shift in how businesses operate, but it has also brought new security challenges. As the threat landscape evolves and new technologies emerge, it’s crucial to future-proof your remote work security strategy. This means adopting a proactive and adaptable approach that can withstand the test of time.
Here are key strategies to consider:
1. Zero Trust Security
The traditional perimeter-based security model is no longer sufficient. A zero-trust approach assumes that no user or device can be trusted by default, requiring strict authentication and authorization at every access point. This minimizes the impact of potential breaches by limiting access to sensitive data.
2. Multi-Factor Authentication (MFA)
MFA is a crucial layer of security that adds an extra level of protection to user accounts. By requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile device, MFA makes it much harder for unauthorized individuals to gain access to company systems.
3. Endpoint Security
With employees working from various locations, endpoint security is essential. This involves implementing software and tools to protect company devices and data from malware, phishing attacks, and other threats. It also includes features like data loss prevention (DLP) to prevent sensitive information from leaving the organization’s control.
4. Continuous Security Monitoring and Response
Proactive monitoring and response are critical for detecting and responding to security incidents in real-time. This requires implementing tools and processes that continuously analyze security data, identify anomalies, and trigger appropriate alerts and actions. Having a dedicated security team or leveraging managed security services can help ensure round-the-clock security monitoring.
5. Employee Security Awareness Training
A robust security strategy includes educating employees about best practices and common threats. Regular security awareness training can help employees identify phishing attempts, avoid suspicious links, and understand their role in protecting company data. This can be done through interactive online modules, simulations, and workshops.
6. Regular Security Audits and Assessments
It’s essential to conduct regular security audits and assessments to identify vulnerabilities and gaps in your security posture. These audits should cover all aspects of your remote work environment, including devices, networks, applications, and user practices. By addressing vulnerabilities promptly, you can minimize the risk of security incidents.
Future-proofing your remote work security strategy is an ongoing process that requires a commitment to continuous improvement and adaptation. By implementing these strategies and staying informed about emerging threats, you can create a more secure and resilient work environment for your employees and your business.