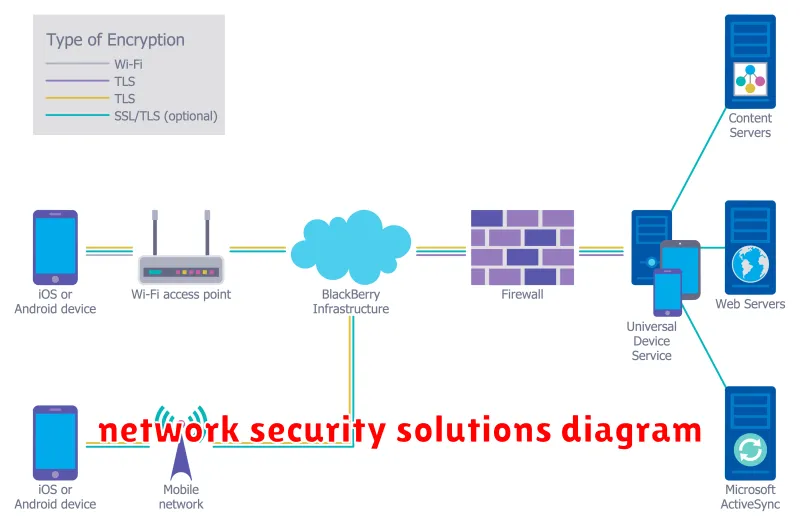
In today’s digital landscape, where data breaches and cyberattacks are becoming increasingly common, securing your network is more crucial than ever. The internet has become an indispensable tool for businesses and individuals alike, but with its convenience comes the inherent risk of vulnerabilities. Network security is the foundation of a safe and reliable online experience, protecting your sensitive information and critical systems from malicious actors.
This article will delve into the multifaceted world of network security solutions, exploring the various tools and strategies that can fortify your digital fortress. From firewalls and intrusion detection systems to endpoint security and data encryption, we’ll unpack the essential components of a comprehensive network security plan. Whether you’re a small business owner, a technology enthusiast, or simply concerned about safeguarding your personal data, this guide will empower you with the knowledge to navigate the complexities of the digital landscape and build a robust defense against cyber threats.
The Importance of Network Security in Today’s Digital Landscape
In today’s digitally-driven world, where information is the lifeblood of businesses and individuals alike, the importance of network security cannot be overstated. Our interconnected world relies heavily on networks for communication, collaboration, and data storage. However, this increased reliance also presents a greater vulnerability to cyber threats.
The consequences of a compromised network can be devastating. From data breaches and financial losses to reputational damage and operational disruptions, the impact can be far-reaching. This is why it’s crucial to prioritize network security and implement robust solutions to safeguard against these threats.
Here are some key reasons why network security is paramount in today’s digital landscape:
- Data Protection: Sensitive data, including customer information, financial records, and intellectual property, is stored and transmitted over networks. A strong security posture is essential to prevent unauthorized access and protect this valuable data from theft or misuse.
- Business Continuity: Network disruptions caused by cyberattacks can cripple operations, leading to lost revenue and productivity. Robust security measures help ensure business continuity and minimize downtime.
- Compliance: Many industries are subject to strict data privacy and security regulations. Adhering to these regulations requires implementing comprehensive network security solutions to protect sensitive data and demonstrate compliance.
- Reputation Management: Data breaches and cyberattacks can severely damage a company’s reputation, erode customer trust, and impact brand value. Proactive security measures help maintain a positive reputation and build confidence among stakeholders.
The threats to network security are constantly evolving, so it’s essential to stay informed about the latest vulnerabilities and adopt proactive measures to mitigate risks. By prioritizing network security, businesses and individuals can create a secure fortress to protect their valuable assets in today’s increasingly digital world.
Types of Network Security Threats: From Malware to DDoS Attacks
In today’s digital landscape, where data reigns supreme, securing your network is paramount. But to build a robust defense, you must first understand the threats you’re facing. This article delves into various types of network security threats, shedding light on their methods and impact.
Malware, short for malicious software, is a broad category encompassing viruses, worms, Trojans, ransomware, and spyware. These insidious programs aim to infiltrate your network, steal data, disrupt operations, or hold your systems hostage. Viruses spread through infected files, while worms self-replicate and spread across networks. Trojans disguise themselves as legitimate software, while ransomware encrypts data and demands payment for its release. Spyware secretly monitors your activities and steals sensitive information.
Phishing is a social engineering tactic that involves deceiving users into divulging confidential information. Attackers often send fraudulent emails, messages, or websites that mimic legitimate sources to trick unsuspecting victims. Social Engineering, in general, relies on manipulating people to gain unauthorized access to sensitive data or systems.
Denial-of-service (DoS) attacks overwhelm a network or server with traffic, making it unavailable to legitimate users. Distributed denial-of-service (DDoS) attacks amplify the impact by using multiple compromised devices (botnets) to flood the target. These attacks can cripple websites, online services, and critical infrastructure.
Man-in-the-middle (MitM) attacks intercept communications between two parties, allowing attackers to eavesdrop on conversations, steal data, or even manipulate information. This can occur in various contexts, such as Wi-Fi networks, online transactions, or secure communications.
SQL injection attacks exploit vulnerabilities in web applications to manipulate databases. By inserting malicious code into input fields, attackers can steal data, modify records, or even gain complete control over the database.
Understanding these diverse threats is crucial for building an effective network security strategy. By recognizing the vulnerabilities and potential attack vectors, you can implement appropriate safeguards to protect your digital assets. Stay vigilant, stay informed, and stay secure.
Firewalls: Your First Line of Defense
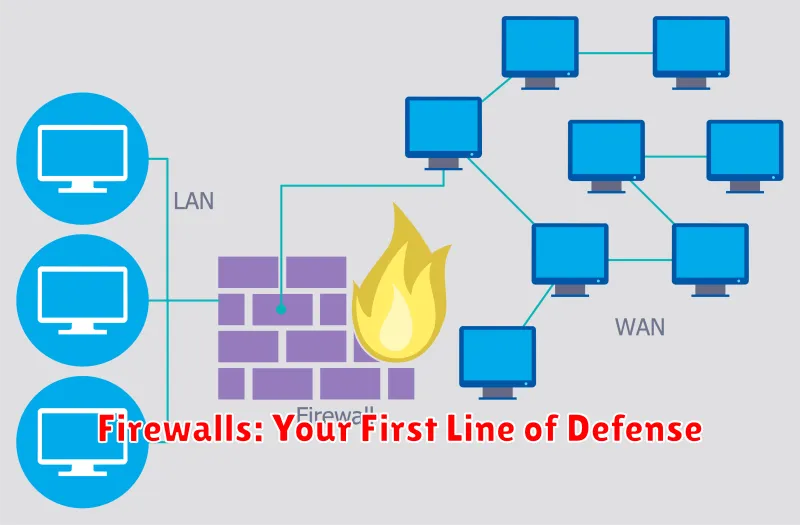
In the digital landscape, where cyber threats are constantly evolving, securing your network is paramount. A firewall acts as your first line of defense, meticulously guarding your network perimeter from unauthorized access and malicious activities. Imagine it as a vigilant gatekeeper, meticulously scrutinizing incoming and outgoing traffic, only allowing legitimate and safe communication to pass through.
Firewalls operate by meticulously analyzing network traffic, comparing it against predefined rules. Any traffic that fails to meet these criteria is promptly blocked, preventing unauthorized access and potential harm. This meticulous process helps safeguard your network from a wide range of threats, including:
- Malware and viruses: Firewalls prevent malicious software from infiltrating your network by blocking infected files or suspicious connections.
- Unauthorized access: By controlling access to your network, firewalls ensure only authorized users and devices can connect, preventing unauthorized access.
- Data breaches: Firewalls act as a barrier, preventing unauthorized individuals from stealing or altering sensitive data within your network.
- Denial of service (DoS) attacks: Firewalls can detect and block DoS attacks, which aim to overwhelm your network with excessive traffic, making it inaccessible.
Firewalls are available in various forms, catering to different needs and network sizes. Hardware firewalls are physical devices installed within your network infrastructure, while software firewalls are installed on individual computers or servers. Cloud-based firewalls provide security from the cloud, offering scalability and flexibility. Regardless of the type, firewalls play a crucial role in protecting your network from the ever-present threats of the digital world.
In the battle for network security, firewalls are your steadfast allies. By diligently guarding your network perimeter, they form a crucial first line of defense, safeguarding your valuable data and ensuring the integrity of your online operations. As you build your secure fortress, remember that a robust firewall is an indispensable component, providing the foundation for a resilient and protected network.
Intrusion Detection and Prevention Systems: Proactive Security Measures
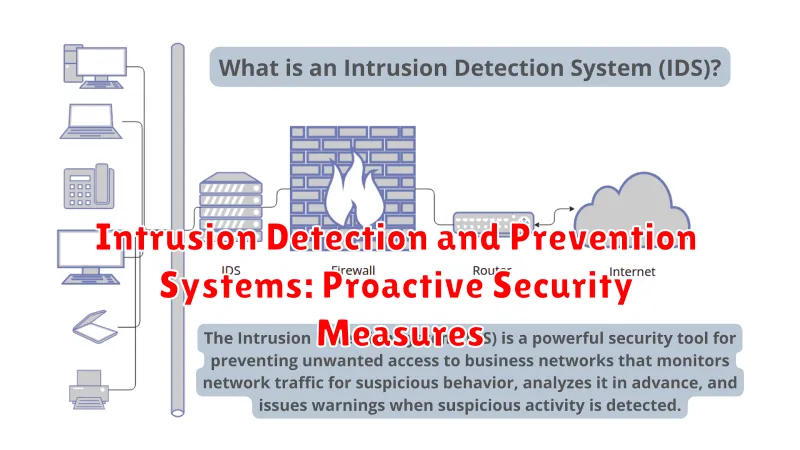
In today’s digital landscape, safeguarding networks from malicious intrusions is paramount. Intrusion detection and prevention systems (IDS/IPS) are essential tools that play a crucial role in bolstering network security and mitigating threats. These systems act as vigilant guardians, constantly monitoring network traffic for suspicious activities and taking proactive measures to prevent attacks.
Intrusion detection systems (IDS) function as security sentinels, analyzing network traffic for potential threats. They identify and report suspicious activity, alerting administrators to potential breaches. On the other hand, intrusion prevention systems (IPS) are equipped with the capability to not only detect threats but also actively block or prevent them from reaching their intended targets.
These systems leverage various techniques, including signature-based detection, anomaly detection, and behavioral analysis, to identify and respond to threats. Signature-based detection relies on known attack patterns and signatures to identify malicious activity. Anomaly detection analyzes network traffic for deviations from typical patterns, flagging suspicious behavior. Behavioral analysis tracks user and system activities, identifying deviations from expected actions.
By implementing IDS/IPS, organizations can gain a significant advantage in proactive threat management. These systems provide real-time visibility into network activities, enabling early detection and response to attacks. They enhance security posture by preventing unauthorized access, data breaches, and system compromises. Moreover, IDS/IPS offer valuable insights into attack trends, enabling security teams to adapt their defenses and stay ahead of evolving threats.
In conclusion, intrusion detection and prevention systems are essential components of a robust network security strategy. By proactively monitoring network traffic, identifying suspicious activity, and taking immediate action to prevent attacks, IDS/IPS play a vital role in safeguarding networks and protecting sensitive data from malicious actors.
Virtual Private Networks (VPNs): Secure Remote Access and Data Encryption
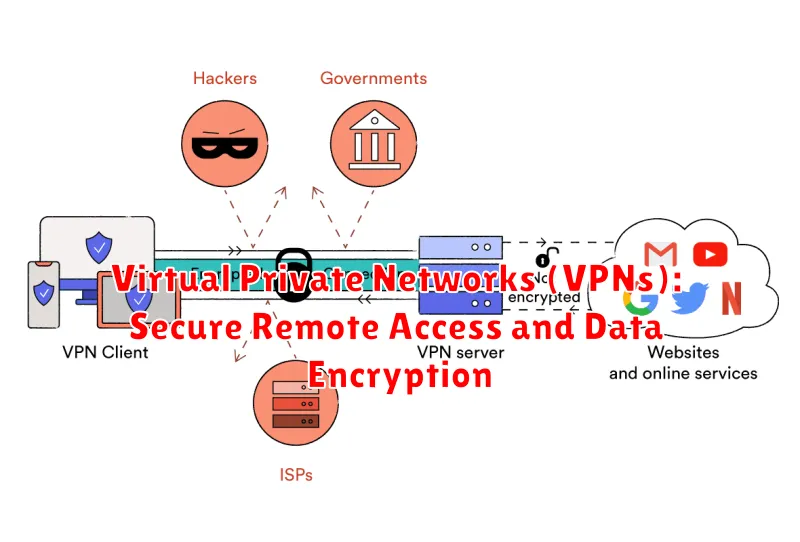
In the realm of network security, where data breaches and cyber threats loom large, Virtual Private Networks (VPNs) stand as a formidable bastion, safeguarding your digital fortress. By creating a secure, encrypted tunnel between your device and a remote server, VPNs provide a robust shield against prying eyes and unauthorized access.
Imagine a scenario where you’re working remotely, connecting to your company network from a public Wi-Fi hotspot. Without a VPN, your data travels unprotected, vulnerable to interception. A VPN acts as a virtual private tunnel, encrypting all your data before it leaves your device. This encrypted traffic travels through the VPN server, making it virtually impossible for anyone to snoop on your online activities.
Secure Remote Access
VPNs enable secure remote access, allowing employees to connect to their company’s network from anywhere in the world. This is particularly crucial for organizations with a dispersed workforce or those needing to access sensitive data from remote locations. By establishing a secure connection through the VPN, employees can work remotely with the same level of security as if they were in the office.
Data Encryption
Data encryption is the cornerstone of VPN security. All data transmitted through a VPN is encrypted using strong algorithms, rendering it unreadable to anyone without the correct decryption key. This encryption process ensures that even if someone intercepts your data, they won’t be able to access its contents.
Key Benefits of VPNs
- Enhanced Privacy: VPNs mask your IP address, preventing websites and advertisers from tracking your online activity.
- Bypass Geo-restrictions: Access geo-blocked content, such as streaming services and websites, by connecting to a server in a different country.
- Secure Public Wi-Fi: Protect your data when using public Wi-Fi networks, which are often vulnerable to security threats.
In today’s digitally connected world, safeguarding your data is paramount. VPNs offer a comprehensive solution for secure remote access, data encryption, and enhanced privacy. By investing in a reliable VPN service, you can build a robust digital fortress, protecting your data and ensuring peace of mind in the online realm.
Network Segmentation: Limiting the Impact of Breaches
In the ever-evolving landscape of cybersecurity, network segmentation has emerged as a crucial defense mechanism for mitigating the impact of breaches. This strategy involves dividing a network into smaller, isolated segments, limiting the lateral movement of attackers and preventing them from accessing sensitive data.
By segmenting your network, you create a more secure environment by:
- Reducing the attack surface: Isolating sensitive data and applications makes it harder for attackers to find and exploit vulnerabilities.
- Limiting the spread of malware: If a device is compromised, segmentation prevents the malware from spreading to other parts of the network.
- Enhancing compliance: Segmentation can help organizations meet regulatory requirements, such as PCI DSS, by isolating sensitive payment card data.
- Improving performance: By reducing network traffic, segmentation can improve overall performance and reduce latency.
Implementation of network segmentation can be tailored to individual needs and resources. Common approaches include:
- VLANs (Virtual Local Area Networks): This technique logically separates devices on a single physical network.
- Firewalls: Firewalls can be used to restrict traffic flow between segments, blocking unauthorized access.
- Software-Defined Networking (SDN): SDN enables more dynamic and flexible network segmentation, allowing administrators to easily adjust policies and rules.
Network segmentation is a powerful tool for enhancing network security. By isolating critical assets and restricting the spread of attacks, it significantly reduces the impact of breaches and strengthens your organization’s overall security posture.
Wireless Security: Protecting Your Wi-Fi Networks
In the realm of technology, where connectivity reigns supreme, the airwaves are teeming with wireless signals, creating a digital landscape that is both convenient and vulnerable. Amidst this wireless wonderland, securing your Wi-Fi network is paramount, as it acts as the digital gateway to your home or office, safeguarding sensitive data and protecting your privacy. This article delves into the realm of wireless security, exploring practical strategies to bolster your Wi-Fi defenses and create a digital fortress.
The first line of defense is choosing a robust password for your Wi-Fi router. Opt for a complex combination of uppercase and lowercase letters, numbers, and symbols, ensuring it’s unique and difficult to guess. Consider using a password manager to generate and store secure passwords.
Beyond passwords, WPA2 or WPA3 encryption protocols are indispensable for encrypting data transmitted over your Wi-Fi network. These protocols scramble data, rendering it unintelligible to unauthorized individuals. While WPA2 is still widely used, WPA3 offers enhanced security features, including stronger encryption and improved authentication mechanisms.
Maintaining your router’s firmware is crucial for patching vulnerabilities. Router manufacturers regularly release firmware updates to address security flaws. By updating your router’s firmware, you ensure that it’s protected against the latest threats. Regularly check for updates and install them promptly.
A firewall acts as a virtual shield, monitoring incoming and outgoing network traffic and blocking suspicious connections. By enabling your router’s built-in firewall or deploying a dedicated firewall, you can add an extra layer of protection to your Wi-Fi network.
Consider using a virtual private network (VPN), which encrypts your internet traffic and routes it through a secure server, effectively masking your online activities and location. VPNs are particularly valuable when using public Wi-Fi networks, as they provide an additional layer of privacy and security.
Securing your Wi-Fi network is an ongoing process. Regularly review your network settings, update your router’s firmware, and be vigilant about suspicious activity. By implementing these strategies, you can create a secure digital fortress that protects your valuable data and ensures a safe and reliable wireless experience.
Email Security: Preventing Phishing and Spam

In today’s digital landscape, email has become an indispensable tool for communication and business operations. However, it also presents a significant vulnerability to security threats such as phishing and spam. Phishing attacks aim to deceive users into revealing sensitive information, while spam floods inboxes with unwanted and often malicious content.
To combat these threats, robust email security measures are essential. Here are some key strategies:
1. Implementing Strong Spam Filters
Spam filters play a crucial role in blocking unsolicited emails. Advanced filters utilize sophisticated algorithms to identify and quarantine suspicious messages based on various factors like sender reputation, content analysis, and blacklists. Regularly updating and configuring these filters is vital to stay ahead of evolving spam tactics.
2. Training Users to Spot Phishing Attempts
Phishing attacks often rely on social engineering techniques to trick users into clicking malicious links or providing sensitive data. Educating users about common phishing indicators, such as suspicious sender addresses, grammatical errors, and urgent requests, is crucial. Conducting regular phishing simulations can help reinforce user awareness and improve detection skills.
3. Employing Email Authentication Protocols
Email authentication protocols like Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) help verify the authenticity of email senders. These protocols use digital signatures to validate the sender’s domain and prevent spoofed emails from reaching recipients. Implementing these protocols significantly reduces the risk of phishing attacks.
4. Utilizing Email Security Gateways
Email security gateways act as a first line of defense against email threats. These gateways scan incoming emails for viruses, malware, and other malicious content. They can also enforce email policies, such as blocking attachments from specific sources or implementing content filtering rules.
5. Encouraging Secure Password Practices
Strong passwords are essential for protecting email accounts from unauthorized access. Encourage users to adopt strong, unique passwords for their email accounts and avoid reusing passwords across multiple platforms. Implementing multi-factor authentication adds an extra layer of security, requiring users to provide multiple forms of identification before accessing their email accounts.
By implementing these security measures, organizations can significantly reduce their risk of falling victim to phishing and spam attacks. Proactive email security practices are crucial for protecting sensitive information, maintaining business continuity, and fostering a secure digital environment.
Network Access Control (NAC): Managing Device Access and Permissions
In the ever-evolving landscape of cybersecurity, safeguarding your network infrastructure is paramount. One powerful tool in your arsenal is Network Access Control (NAC), a technology that plays a crucial role in securing your network by meticulously controlling device access and permissions.
NAC operates by establishing a system that verifies the identity and security posture of any device attempting to connect to your network. This rigorous vetting process ensures that only authorized and compliant devices gain entry, effectively mitigating the risk of unauthorized access and malicious intrusions.
At its core, NAC leverages a multi-pronged approach to achieve its security goals:
- Device Identification: NAC solutions identify each device attempting to connect, whether it’s a laptop, smartphone, or IoT device.
- Compliance Enforcement: They verify if the device meets your pre-defined security policies. This might include checks for up-to-date antivirus software, operating system patches, and firewall configurations.
- Access Control: Based on the device’s identity and compliance status, NAC determines the level of access it grants. This could range from full network access to restricted access to specific resources.
- Network Segmentation: NAC enables network segmentation, creating isolated zones within your network to further enhance security and prevent lateral movement of potential threats.
The implementation of NAC delivers a range of tangible benefits:
- Enhanced Network Security: By limiting access to only authorized and compliant devices, NAC significantly reduces the risk of unauthorized access and malware propagation.
- Improved Compliance: NAC helps organizations meet regulatory compliance requirements by ensuring that all connected devices adhere to specific security standards.
- Reduced Risk of Data Breaches: NAC mitigates the risk of data breaches by preventing unauthorized access to sensitive data and systems.
- Streamlined Network Management: NAC simplifies network management by providing a centralized platform to control and monitor device access and compliance.
As your network becomes increasingly complex and the threat landscape evolves, NAC emerges as an essential component of a comprehensive security strategy. By implementing NAC, you can effectively manage device access and permissions, bolstering your network’s defenses against modern threats and ensuring the safety of your valuable data.
Data Loss Prevention (DLP): Safeguarding Sensitive Information
In today’s digital landscape, data is the lifeblood of organizations. From customer information to financial records, sensitive data is constantly flowing through networks, making it vulnerable to unauthorized access and breaches. This is where Data Loss Prevention (DLP) comes into play, acting as a crucial defense mechanism to protect sensitive information from falling into the wrong hands.
DLP solutions are designed to identify, monitor, and prevent the unauthorized transfer of sensitive data. They work by establishing rules and policies that define what constitutes sensitive data and how it can be used or transmitted. These rules can be based on various factors, including data content, file type, destination, and user behavior.
DLP systems employ a multifaceted approach to data protection. They can monitor various channels, including:
- Email: Detecting and blocking emails containing sensitive information sent to unauthorized recipients.
- Web browsing: Preventing the upload of sensitive data to unauthorized websites or cloud storage services.
- File transfer: Monitoring and blocking transfers of sensitive data through FTP, USB drives, and other file sharing methods.
- Network traffic: Analyzing network traffic to identify and block suspicious data transfers.
Beyond detection, DLP solutions can take proactive steps to mitigate data loss risks. These steps include:
- Data masking: Replacing sensitive data with harmless substitutes to prevent unauthorized access.
- Data encryption: Scrambling sensitive data to make it incomprehensible without the appropriate decryption key.
- Access control: Restricting user access to sensitive data based on predefined roles and permissions.
- Alerting: Generating alerts to security teams when suspicious data transfer attempts are detected.
Implementing a comprehensive DLP strategy is essential for any organization that handles sensitive information. It provides a vital layer of security, ensuring the confidentiality and integrity of data, and ultimately, protecting the organization from reputational damage, legal penalties, and financial losses.
Security Information and Event Management (SIEM): Centralized Security Monitoring
In the modern digital landscape, where cyber threats are becoming increasingly sophisticated, robust security measures are paramount. A crucial component of any effective security strategy is the implementation of a Security Information and Event Management (SIEM) system. SIEM acts as a centralized hub for security monitoring, providing comprehensive visibility into your network’s activities and enabling proactive threat detection and response.
SIEM solutions aggregate logs and events from various sources across your IT infrastructure, including firewalls, intrusion detection systems (IDS), anti-virus software, and servers. By correlating these data points, SIEM systems can identify suspicious patterns and anomalies that might indicate malicious activity. This real-time analysis empowers security teams to detect threats early, minimizing the potential for damage and data breaches.
Beyond threat detection, SIEM offers a range of valuable capabilities:
- Centralized Reporting: SIEM provides comprehensive reports on security events, facilitating compliance audits and demonstrating security posture.
- Incident Response: SIEM streamlines incident response by providing clear context and actionable intelligence, enabling swift and effective mitigation.
- Security Policy Enforcement: SIEM can enforce security policies and identify deviations, helping maintain a secure environment.
Choosing the right SIEM solution is essential, considering factors such as your organization’s size, security needs, and budget. Leading SIEM vendors offer a range of features and functionalities to cater to diverse requirements.
By leveraging the power of SIEM, organizations can gain a significant advantage in safeguarding their digital assets. This centralized security monitoring approach provides a comprehensive view of network activity, empowers proactive threat detection, and facilitates effective incident response. It’s a crucial element in building a secure fortress against the ever-evolving threat landscape.
Managed Security Services Providers (MSSPs): Outsourcing Network Security Expertise
In today’s digital landscape, cybersecurity is paramount. As threats evolve and become more sophisticated, organizations face a constant struggle to keep their networks secure. This is where Managed Security Services Providers (MSSPs) come in, offering a lifeline to businesses seeking to outsource their network security expertise.
MSSPs provide a range of security services, from threat monitoring and incident response to vulnerability assessments and security audits. By leveraging the expertise and resources of an MSSP, organizations can gain a significant edge in their security posture.
Here are some key benefits of partnering with an MSSP:
- Cost-effective solution: MSSPs offer a cost-effective alternative to building and maintaining an in-house security team, especially for small and medium-sized businesses.
- Access to specialized skills and resources: MSSPs possess a wealth of knowledge and experience in the latest security threats and technologies, enabling them to provide advanced security solutions.
- 24/7 monitoring and proactive threat detection: MSSPs offer round-the-clock monitoring of network activity, allowing them to identify and respond to security incidents promptly.
- Improved security posture: By implementing best practices and leveraging cutting-edge tools, MSSPs help organizations strengthen their overall security posture.
Choosing the right MSSP is crucial. Organizations should consider factors such as:
- Experience and expertise: Look for an MSSP with a proven track record in providing security services to organizations in your industry.
- Service portfolio: Ensure the MSSP offers the specific services you need, such as threat monitoring, incident response, or vulnerability assessments.
- Certifications and accreditations: Look for certifications such as ISO 27001 or SOC 2, which demonstrate the MSSP’s commitment to security standards.
- Customer support: Evaluate the MSSP’s responsiveness and availability to provide support when needed.
By outsourcing their network security expertise to a reputable MSSP, organizations can free up internal resources and focus on their core business operations, while enjoying peace of mind knowing their networks are protected.
Emerging Trends in Network Security: SASE, Zero Trust, and AI
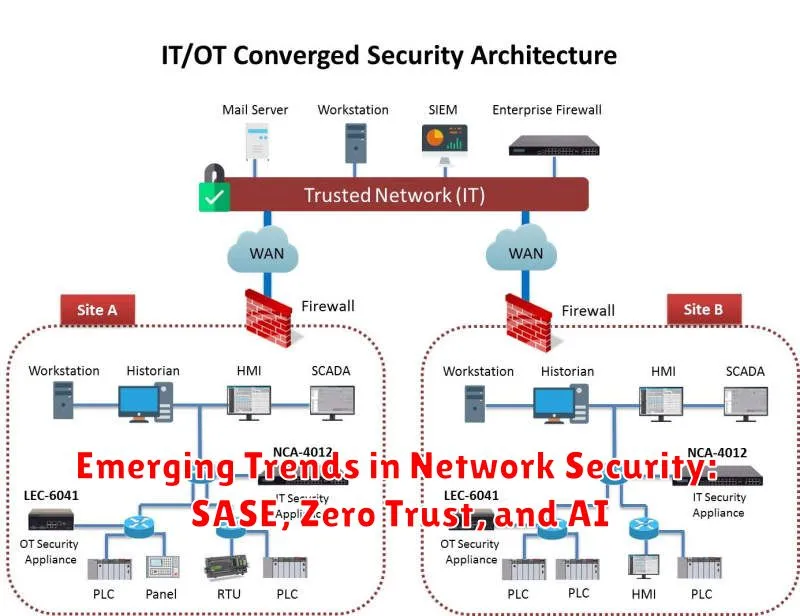
The digital landscape is evolving rapidly, with remote work and cloud adoption becoming the norm. This shift has created new challenges for network security, demanding innovative solutions to protect sensitive data and ensure business continuity. In response, three emerging trends are shaping the future of network security: SASE (Secure Access Service Edge), Zero Trust, and AI (Artificial Intelligence).
SASE provides a unified approach to network security, delivering secure access to applications and data from anywhere. By integrating network and security functions into a single platform, SASE simplifies management, improves performance, and enhances security posture. This approach enables organizations to securely connect users and devices to the cloud, regardless of location.
Zero Trust goes beyond traditional perimeter-based security by assuming that no user or device can be trusted by default. This philosophy emphasizes continuous verification and authentication, ensuring that only authorized users and devices have access to specific resources. Zero Trust architectures are designed to prevent lateral movement within a network, mitigating the impact of potential breaches.
AI is revolutionizing network security by automating threat detection and response. AI-powered security solutions can analyze vast amounts of data, identify anomalies, and detect sophisticated attacks in real time. This allows security teams to proactively address threats and reduce the time it takes to respond to incidents.
By adopting these emerging trends, organizations can build a secure fortress that effectively protects their assets and enables them to thrive in the ever-evolving digital landscape. SASE, Zero Trust, and AI represent powerful tools that can transform how organizations approach network security, ensuring a more robust and resilient future.