In today’s digital world, a reliable and secure network is essential for businesses of all sizes. A robust network infrastructure allows for seamless communication, efficient data sharing, and uninterrupted access to critical applications. However, managing a complex network can be a daunting task, especially as businesses grow and their network requirements evolve. This is where effective network infrastructure management comes into play.
Implementing best practices for network infrastructure management is crucial for ensuring a stable, secure, and scalable network. By adopting these practices, organizations can optimize their network performance, minimize downtime, and protect sensitive data from cyber threats. This article will delve into essential best practices for network infrastructure management, covering topics such as network design, security, monitoring, and maintenance. Whether you’re a seasoned IT professional or a business leader looking to improve your network, this comprehensive guide will provide valuable insights and actionable strategies for building and maintaining a robust and secure network foundation.
Understanding Network Infrastructure
Network infrastructure is the foundation of any modern business, connecting devices, users, and applications to facilitate communication and information flow. It comprises a complex web of hardware and software components that work together seamlessly. Understanding these components and their interdependencies is crucial for effective network management.
At its core, network infrastructure consists of several key elements:
- Network Devices: These include routers, switches, firewalls, and access points that manage traffic flow, security, and connectivity.
- Cabling: Physical connections, such as copper or fiber optic cables, form the backbone of the network, transmitting data between devices.
- Servers: These powerful computers store and process data, host applications, and provide essential services like email and file sharing.
- Network Operating System (NOS): Software that controls and manages network devices, enabling communication and data transmission.
- Network Management Software: Tools that monitor, analyze, and optimize network performance, security, and resource utilization.
These components work together to create a robust and secure network that enables businesses to function effectively. Each element plays a critical role in ensuring data integrity, network stability, and user productivity.
Key Components of Network Infrastructure
A robust and secure network infrastructure is the backbone of any modern organization, enabling seamless communication, data sharing, and efficient operations. Understanding the key components of this infrastructure is crucial for effective network management.
Network Devices
Network devices act as the building blocks of a network, connecting various components and facilitating data transmission. Some essential devices include:
- Routers: Direct network traffic between different networks, ensuring data reaches its intended destination.
- Switches: Facilitate communication within a single network, connecting devices on a local network segment.
- Firewalls: Act as security guardians, filtering incoming and outgoing network traffic to protect against unauthorized access and malicious threats.
- Modems: Connect your network to the internet, enabling communication with external networks.
- Wireless Access Points (WAPs): Provide wireless connectivity, allowing devices to access the network without physical cables.
Network Cabling
Network cabling is the physical medium that connects network devices, enabling data transmission. Common types include:
- Twisted-Pair Cable: The most prevalent type, offering cost-effectiveness and flexibility.
- Coaxial Cable: Used for high-frequency data transmission, often for cable television networks.
- Fiber Optic Cable: Offers high bandwidth and resistance to interference, ideal for long distances and high-speed data transfers.
Network Protocols
Network protocols define the rules and standards that govern data communication within a network. Key protocols include:
- Transmission Control Protocol/Internet Protocol (TCP/IP): The foundation of the internet, responsible for addressing and routing data packets.
- Hypertext Transfer Protocol (HTTP): Enables communication between web browsers and web servers, allowing access to websites and online resources.
- File Transfer Protocol (FTP): Used for transferring files between computers over a network.
Network Security
Network security measures are crucial for protecting data and systems from unauthorized access and threats. Key aspects include:
- Firewall: A first line of defense, blocking malicious traffic and unauthorized connections.
- Intrusion Detection and Prevention Systems (IDS/IPS): Monitor network traffic for suspicious activity and take appropriate actions to prevent attacks.
- Antivirus and Anti-Malware Software: Protects devices from viruses, malware, and other cyber threats.
- User Authentication: Requires users to verify their identity before accessing the network, ensuring only authorized individuals can access sensitive information.
Network Management Tools
Network management tools are essential for monitoring network performance, troubleshooting issues, and ensuring optimal network operation. Some common tools include:
- Network Monitoring Tools: Provide real-time insights into network health, performance, and traffic patterns.
- Network Configuration Tools: Enable efficient management of network devices, settings, and policies.
- Network Analysis Tools: Help identify performance bottlenecks, security vulnerabilities, and other network issues.
Understanding the key components of network infrastructure is essential for building a robust, secure, and efficient network. By implementing best practices and utilizing appropriate tools, organizations can ensure smooth operations and safeguard their critical data and systems.
Network Infrastructure Management Tools
Effective network infrastructure management is crucial for organizations of all sizes. It ensures optimal performance, reliability, and security, allowing for seamless business operations. To achieve this, utilizing the right tools is essential. Network infrastructure management tools provide a comprehensive suite of features to monitor, manage, and optimize network devices, applications, and services.
These tools empower network administrators to:
- Monitor network performance in real-time, identifying bottlenecks and potential issues.
- Manage network devices, including routers, switches, firewalls, and servers, from a centralized console.
- Automate tasks, such as configuration changes and software updates, to streamline operations and reduce errors.
- Analyze network traffic to identify patterns and trends, optimize bandwidth allocation, and detect security threats.
- Troubleshoot network issues quickly and efficiently, minimizing downtime and impact on business operations.
The market offers a wide range of network infrastructure management tools, each catering to specific needs and budgets. Popular options include:
- SolarWinds Network Performance Monitor (NPM): A comprehensive tool for network monitoring, performance analysis, and troubleshooting.
- Datadog: Provides a unified platform for monitoring and managing various IT infrastructure components, including networks.
- ManageEngine OpManager: A comprehensive network management solution with features for monitoring, alerting, and reporting.
- Auvik: Offers a cloud-based platform for network discovery, mapping, and monitoring, designed for simplicity and ease of use.
- PRTG Network Monitor: A flexible and scalable tool for monitoring networks, devices, and applications.
By leveraging these tools, organizations can gain valuable insights into their network performance, proactively address potential issues, and ensure a robust and secure network infrastructure. This, in turn, enables businesses to operate efficiently, maintain high levels of productivity, and safeguard sensitive data.
Network Security and Monitoring
Network security and monitoring are critical components of a robust and secure network infrastructure. By implementing best practices in these areas, organizations can effectively protect their sensitive data and systems from unauthorized access, malicious attacks, and other threats.
Firewalls are essential for blocking unauthorized access to the network. They act as a barrier between the network and the outside world, filtering incoming and outgoing traffic based on predefined rules. Firewalls can be implemented at various levels, including hardware, software, and cloud-based solutions.
Intrusion Detection and Prevention Systems (IDPS) are used to detect and prevent malicious activity within the network. They analyze network traffic for suspicious patterns and can take actions such as blocking connections, logging events, or alerting administrators.
Network Segmentation involves dividing the network into smaller, isolated segments. This helps to limit the impact of security breaches by preventing attackers from spreading laterally across the network.
Vulnerability Scanning regularly assesses the network for known security vulnerabilities. By identifying and patching vulnerabilities promptly, organizations can reduce the risk of exploitation.
Regular Monitoring is crucial for detecting and responding to security incidents. Network monitoring tools provide real-time visibility into network traffic, device health, and user activity. This data can be used to identify anomalies, investigate security incidents, and proactively address potential threats.
Security Information and Event Management (SIEM) systems aggregate security data from multiple sources and provide a centralized view of security events. This allows organizations to analyze security events, identify trends, and take appropriate actions.
By implementing these best practices, organizations can enhance their network security and monitoring capabilities, ensuring the protection of their valuable data and systems.
Performance Optimization Techniques
Network performance is critical for any organization, as it directly impacts productivity, collaboration, and customer satisfaction. Optimizing network performance ensures smooth data flow, minimizes latency, and enhances overall network responsiveness. Here are some key performance optimization techniques for a robust and secure network:
Bandwidth Management: Effective bandwidth management is crucial for preventing network congestion and ensuring optimal performance. Implementing traffic shaping and prioritization tools helps prioritize critical applications, limit bandwidth-intensive activities, and prevent bottlenecks.
Network Segmentation: Dividing your network into smaller, logical segments based on function or security requirements improves security and performance. Network segmentation isolates traffic, reduces broadcast storms, and simplifies troubleshooting.
Caching: Implementing caching mechanisms, like DNS caching and content delivery networks (CDNs), reduces latency by storing frequently accessed data closer to users. This significantly improves application responsiveness and reduces network traffic.
Quality of Service (QoS): QoS mechanisms prioritize traffic based on application requirements, ensuring that critical applications like voice and video receive the necessary bandwidth. This guarantees consistent performance for essential services.
Network Monitoring and Analysis: Continuous monitoring and analysis are essential for identifying and resolving performance issues proactively. Network performance monitoring tools provide real-time insights into network health, traffic patterns, and potential bottlenecks, enabling timely interventions.
Network Optimization Tools: Various network optimization tools can help fine-tune network performance, including network analyzers, traffic shapers, and load balancers. These tools offer advanced capabilities for identifying performance bottlenecks, optimizing bandwidth allocation, and enhancing network efficiency.
Cloud-Based Network Management
In today’s dynamic and complex IT landscape, efficient network management is paramount for businesses of all sizes. Traditional on-premises network management systems often struggle to keep pace with evolving network demands and present challenges such as high upfront costs, limited scalability, and complex maintenance.
Cloud-based network management offers a compelling alternative, providing a range of benefits that streamline operations and enhance network performance, security, and overall efficiency. This approach leverages the power of cloud computing to centralize network management tasks, enabling businesses to manage their networks remotely and access advanced capabilities that were previously out of reach.
Here are some key advantages of cloud-based network management:
- Centralized Management and Visibility: Cloud-based platforms provide a unified console for monitoring and managing all network devices and infrastructure from a single location. This eliminates the need for multiple management tools and facilitates a comprehensive overview of network health and performance.
- Scalability and Flexibility: Cloud-based solutions are highly scalable, allowing businesses to easily adjust their network capacity as needed. This eliminates the need for significant upfront investments in hardware and software, reducing capital expenditures and allowing for greater agility in response to changing business requirements.
- Cost Optimization: Cloud-based network management solutions often operate on a pay-as-you-go model, reducing the need for large capital expenditures and lowering overall operational costs. This eliminates the expense of maintaining and upgrading on-premises infrastructure, freeing up valuable resources for strategic initiatives.
- Enhanced Security: Cloud providers invest heavily in security infrastructure and expertise, offering advanced protection against cyber threats and data breaches. This includes robust access controls, data encryption, and regular security updates, safeguarding network data and ensuring compliance with industry regulations.
- Simplified Deployment and Maintenance: Cloud-based solutions are typically easier to deploy and manage compared to on-premises alternatives. Cloud providers handle infrastructure maintenance and updates, freeing up IT staff to focus on strategic projects and innovation.
By embracing cloud-based network management, businesses can unlock a world of benefits, empowering them to optimize network performance, enhance security, and drive operational efficiency. This modern approach to network management paves the way for a more agile, scalable, and cost-effective IT environment, enabling businesses to thrive in the digital age.
Network Automation and Orchestration
Network automation and orchestration are crucial components of modern network infrastructure management. They empower organizations to streamline tasks, reduce manual errors, and enhance overall network efficiency and security. Automation involves using scripts and tools to automate repetitive tasks, such as device configuration, software updates, and troubleshooting. This frees up network engineers to focus on more strategic initiatives. Orchestration takes it a step further, coordinating and automating complex workflows across multiple network devices and systems.
By leveraging automation and orchestration, organizations can achieve several benefits:
- Faster Deployment: Automated provisioning and configuration significantly reduce deployment time for new network services and infrastructure.
- Improved Efficiency: Repetitive tasks are automated, allowing network teams to focus on higher-value activities.
- Reduced Errors: Automation eliminates manual errors that can occur during configuration and maintenance.
- Enhanced Security: Automation can enforce consistent security policies across the network and detect and respond to threats more effectively.
- Increased Scalability: Automated processes can easily scale to accommodate growing network demands.
To effectively implement network automation and orchestration, organizations should consider the following best practices:
- Define Clear Goals: Identify specific tasks and processes that can be automated to achieve desired outcomes.
- Choose the Right Tools: Select automation and orchestration tools that align with your network environment and requirements.
- Start Small and Iterate: Begin with automating simple tasks and gradually increase complexity as your team gains experience.
- Embrace a DevOps Culture: Foster collaboration between network and development teams to ensure seamless integration and automation.
- Continuously Monitor and Evaluate: Regularly assess the performance and effectiveness of your automation and orchestration processes.
Network automation and orchestration are essential for building robust and secure network infrastructures. By embracing these technologies, organizations can enhance efficiency, reduce risks, and unlock new possibilities for their network operations.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity are critical aspects of network infrastructure management that ensure the continued operation of your business in the face of unforeseen events. These plans outline strategies for mitigating the impact of disasters, such as natural calamities, cyberattacks, or equipment failures, on your network and business operations.
Disaster recovery focuses on restoring your network and systems to their pre-disaster state, enabling your business to resume operations as quickly as possible. This involves having backup systems, data replication, and recovery procedures in place. Business continuity, on the other hand, focuses on maintaining essential business functions during and after a disaster. This may involve implementing alternative work arrangements, communication protocols, and critical application redundancy to ensure uninterrupted service delivery.
By implementing robust disaster recovery and business continuity plans, you can significantly minimize the impact of disruptive events on your business. These plans should be tested regularly to ensure their effectiveness and updated to reflect changes in your network infrastructure and business operations.
Here are some key best practices for incorporating disaster recovery and business continuity into your network infrastructure management:
- Data backups and replication: Regularly back up your critical data and replicate it to multiple locations, including off-site storage. This ensures data recovery even if your primary site is affected.
- Redundancy and failover mechanisms: Implement redundant network components, such as servers, routers, and switches, to ensure that if one component fails, another takes over seamlessly. This ensures continuous connectivity and service availability.
- Business impact analysis: Identify critical business functions and assess the potential impact of various disruptions on your operations. This helps prioritize recovery efforts and resource allocation.
- Regular testing and drills: Conduct regular disaster recovery and business continuity drills to simulate real-world scenarios. This helps identify gaps and refine your recovery procedures.
- Communication and coordination: Establish clear communication channels and procedures for coordinating recovery efforts among your team, vendors, and stakeholders.
By integrating these best practices into your network infrastructure management, you can significantly improve the resilience and security of your network, minimizing the impact of disruptions and ensuring business continuity in the face of unforeseen events.
Capacity Planning and Scalability
Capacity planning and scalability are crucial aspects of network infrastructure management, ensuring that your network can handle current and future demands without performance degradation. Proper capacity planning involves accurately predicting future network needs, including bandwidth, storage, and server resources. This foresight allows you to proactively allocate resources, preventing bottlenecks and service disruptions.
Scalability, on the other hand, refers to the network’s ability to grow and adapt to increasing traffic and user demands. A scalable network can seamlessly accommodate new users, devices, and applications without compromising performance. This flexibility is essential for businesses experiencing rapid growth or facing fluctuating traffic patterns.
To achieve optimal capacity planning and scalability, consider these best practices:
- Conduct thorough network assessments: Regularly analyze network usage patterns, identify bottlenecks, and anticipate future growth trends. This data forms the foundation for informed capacity planning.
- Implement a tiered approach: Design your network with different capacity tiers, allowing for gradual scaling as demand increases. This modular approach simplifies resource allocation and reduces upfront costs.
- Utilize virtualization and cloud services: Virtualization allows for flexible resource allocation and on-demand scaling. Cloud services provide additional scalability and reduce the need for significant upfront investments.
- Adopt automated monitoring and management tools: Real-time network monitoring provides valuable insights into resource utilization and potential bottlenecks. Automated tools streamline network management and enable proactive capacity adjustments.
- Prioritize network security: Security considerations should be integrated into capacity planning. Secure network infrastructure safeguards against unauthorized access and ensures business continuity.
By prioritizing capacity planning and scalability, businesses can build a robust and secure network that meets current and future needs, fostering agility and supporting continuous growth.
Emerging Trends in Network Infrastructure Management
Network infrastructure management is constantly evolving, driven by the increasing complexity of modern networks and the growing demand for secure and reliable connectivity. This article will explore some of the emerging trends shaping the future of network infrastructure management.
Automation and Orchestration
Automation and orchestration are becoming increasingly essential for managing complex networks efficiently. Network automation tools streamline tasks such as provisioning, configuration, and troubleshooting, reducing manual effort and errors. Orchestration tools enable the coordination of multiple network devices and services, providing a centralized platform for managing network resources.
Cloud-Native Networking
The rise of cloud computing has led to a significant shift in network infrastructure management. Cloud-native networking solutions, such as software-defined networking (SDN) and network function virtualization (NFV), allow businesses to deploy and manage network services in a flexible and scalable manner. This approach provides greater agility, cost efficiency, and rapid deployment capabilities.
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are transforming network infrastructure management by enabling predictive analytics and proactive problem resolution. AI-powered tools can analyze network data to identify patterns and anomalies, predict potential issues, and optimize network performance. This approach helps IT teams to be more proactive in maintaining network stability and security.
Zero Trust Security
In a world of increasing cyber threats, zero trust security is becoming a fundamental principle for network infrastructure management. This approach assumes that no user or device should be trusted by default, requiring strict authentication and authorization for access to network resources. Zero trust security helps to mitigate risks and improve overall network security posture.
Edge Computing
The growth of edge computing is expanding the reach of network infrastructure management. Edge devices are increasingly used to process data and provide services closer to users, reducing latency and enhancing responsiveness. This trend requires new approaches to managing distributed network infrastructure and ensuring data security at the edge.
In conclusion, the emerging trends in network infrastructure management are driving significant changes in how organizations manage their networks. By embracing automation, cloud-native solutions, AI, zero trust security, and edge computing, businesses can achieve greater agility, security, and efficiency in their network operations.
Software-Defined Networking (SDN)
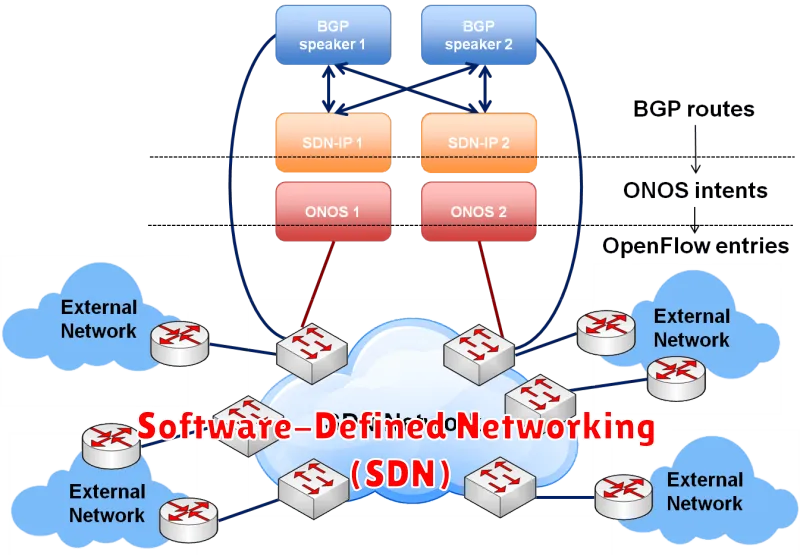
Software-Defined Networking (SDN) is a revolutionary approach to network management that separates the control plane from the data plane. In traditional networks, these two planes are tightly coupled, making it difficult to manage and configure. SDN, on the other hand, allows network administrators to centrally control and orchestrate network devices through a software-based controller.
SDN offers several benefits for network infrastructure management, including:
- Enhanced Agility and Flexibility: SDN enables quick and easy network configuration changes, allowing for rapid deployment of new services and applications. Network administrators can easily adjust network policies and traffic flows without requiring hardware modifications.
- Centralized Control and Visibility: SDN provides a unified platform for managing and monitoring the entire network infrastructure. Network administrators gain comprehensive insights into network performance, traffic patterns, and security threats.
- Automation and Orchestration: SDN automates network tasks, such as provisioning, configuration, and troubleshooting, simplifying network operations and reducing human error.
- Improved Security: SDN facilitates enhanced security measures by allowing network administrators to implement granular access control policies and isolate sensitive traffic.
By leveraging SDN, organizations can achieve a more robust and secure network infrastructure, while also optimizing network performance and efficiency. SDN empowers network administrators with the tools and flexibility needed to adapt to the ever-changing demands of modern businesses.
Network Virtualization and Cloud Integration
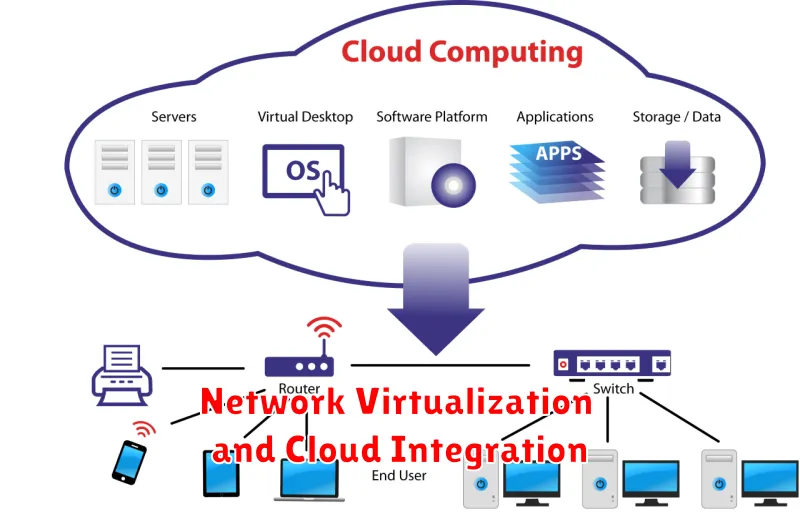
In today’s dynamic IT landscape, organizations are increasingly adopting cloud computing to enhance agility, scalability, and cost-effectiveness. However, seamlessly integrating on-premise networks with cloud environments poses significant challenges. This is where network virtualization plays a pivotal role.
Network virtualization allows organizations to abstract physical network infrastructure into software-defined entities. This enables flexible and efficient network resource allocation, independent of underlying hardware limitations. Through virtualized networks, organizations can create virtualized networks, security zones, and network services on demand.
Cloud integration further amplifies the benefits of network virtualization by facilitating seamless connectivity between on-premise and cloud environments. This integration enables organizations to extend their existing networks to the cloud, enabling access to cloud services and applications with minimal latency and enhanced security.
By embracing network virtualization and cloud integration, organizations can leverage the following advantages:
- Enhanced Agility and Scalability: Virtualized networks can be provisioned and scaled rapidly to meet changing business requirements, eliminating the need for costly hardware upgrades.
- Improved Security: Network segmentation and isolation offered by virtualization enhance security by limiting the impact of breaches and attacks.
- Cost Optimization: Virtualization and cloud integration reduce infrastructure costs by optimizing resource utilization and eliminating the need for dedicated hardware.
- Increased Efficiency: Network automation and orchestration capabilities simplify network management and reduce operational overhead.
By adopting a well-defined strategy for network virtualization and cloud integration, organizations can unlock the full potential of cloud computing and achieve a more robust, secure, and efficient IT infrastructure.
Network Security Best Practices
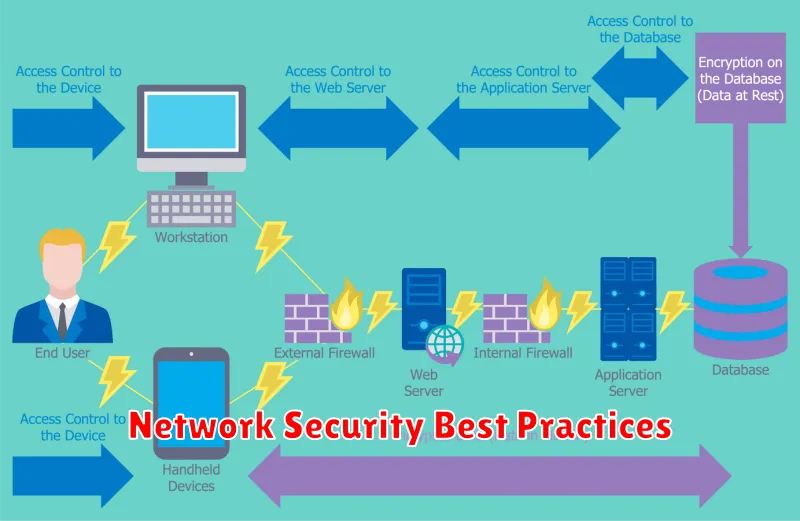
Network security is paramount in today’s digital landscape, where cyber threats are constantly evolving. A robust and secure network infrastructure is essential for protecting sensitive data, ensuring business continuity, and maintaining user trust. This article will delve into key network security best practices to fortify your network against malicious actors.
1. Implement Strong Passwords and Multi-Factor Authentication (MFA): Weak passwords are a common entry point for attackers. Encourage users to create strong, unique passwords for each account and implement MFA, which adds an extra layer of security by requiring users to provide multiple forms of authentication.
2. Keep Software and Firmware Up to Date: Regularly updating software and firmware patches vulnerabilities that attackers can exploit. Automated updates can help streamline this process.
3. Employ a Robust Firewall: A firewall acts as a barrier between your network and the outside world, blocking unauthorized access. Utilize a comprehensive firewall solution that incorporates intrusion detection and prevention systems.
4. Segment Your Network: Network segmentation divides your network into smaller, isolated segments. This limits the impact of a security breach by preventing attackers from accessing sensitive data in other segments.
5. Secure Wireless Networks: Wireless networks are particularly vulnerable to attacks. Use strong encryption protocols like WPA3 and enable network access control to restrict unauthorized device access.
6. Implement Network Monitoring and Intrusion Detection Systems (IDS): Continuous monitoring of network activity is crucial for identifying potential threats and anomalies. Intrusion detection systems can alert you to suspicious activity and allow for prompt action.
7. Train Users on Security Awareness: User education is vital for preventing phishing attacks, malware infections, and other social engineering threats. Regularly train users on best practices for online security.
8. Conduct Regular Security Audits: Conduct periodic security audits to assess your network’s vulnerability and identify areas for improvement. This proactive approach helps ensure your security measures remain effective.
9. Implement Data Loss Prevention (DLP): DLP solutions help prevent sensitive data from leaving your network unauthorized. This is crucial for protecting confidential information like customer data, financial records, and intellectual property.
10. Stay Informed and Adapt: The cybersecurity landscape is constantly evolving. Stay informed about emerging threats and vulnerabilities, and adapt your security measures accordingly to maintain a robust and secure network.
By implementing these network security best practices, you can significantly reduce the risk of cyberattacks and protect your valuable assets. Remember, a layered approach to security is crucial, and a continuous cycle of evaluation, adaptation, and improvement is key to maintaining a secure network infrastructure.
Network Monitoring and Performance Analysis
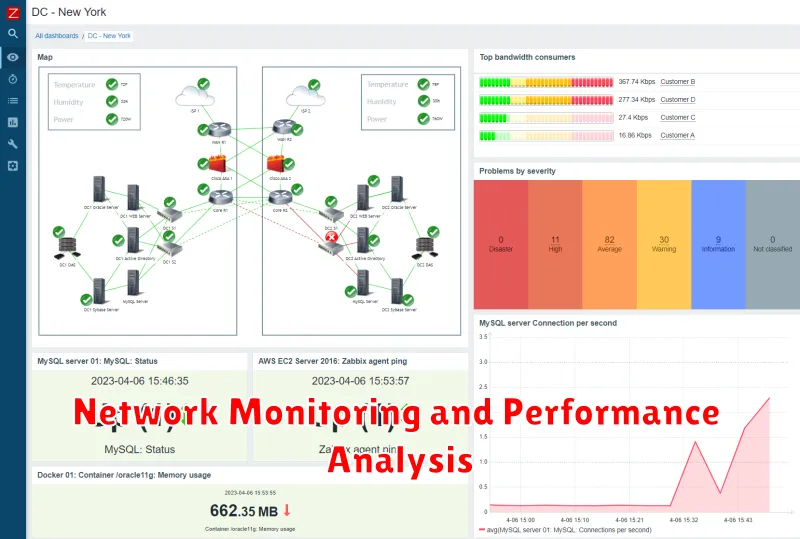
Network monitoring and performance analysis are essential aspects of effective network infrastructure management. By continuously observing and analyzing network health, you can identify potential issues, optimize performance, and ensure the security and reliability of your network.
Network monitoring involves collecting and analyzing data about network devices, traffic, and performance metrics. This data can be used to identify potential problems such as slow connections, high latency, or network outages. Tools and techniques used for network monitoring include:
- Network Performance Monitoring (NPM) tools: These tools provide comprehensive insights into network performance, including bandwidth utilization, latency, and packet loss.
- Simple Network Management Protocol (SNMP): A widely used protocol for collecting data from network devices.
- Flow analysis: Analyzing network traffic patterns to identify trends and anomalies.
Performance analysis goes beyond simply monitoring network data. It involves analyzing the collected data to understand the underlying causes of performance issues and identify areas for improvement. Key aspects of performance analysis include:
- Identifying bottlenecks: Identifying network components or processes that are limiting overall network performance.
- Analyzing traffic patterns: Understanding how network traffic is flowing and identifying any unusual patterns.
- Performance tuning: Adjusting network settings and configurations to optimize performance.
By implementing effective network monitoring and performance analysis practices, organizations can proactively address issues, optimize network resources, and ensure a reliable and secure network environment. Continuous monitoring and analysis enable organizations to stay ahead of potential problems, identify areas for improvement, and maintain a robust network infrastructure.
The Future of Network Infrastructure
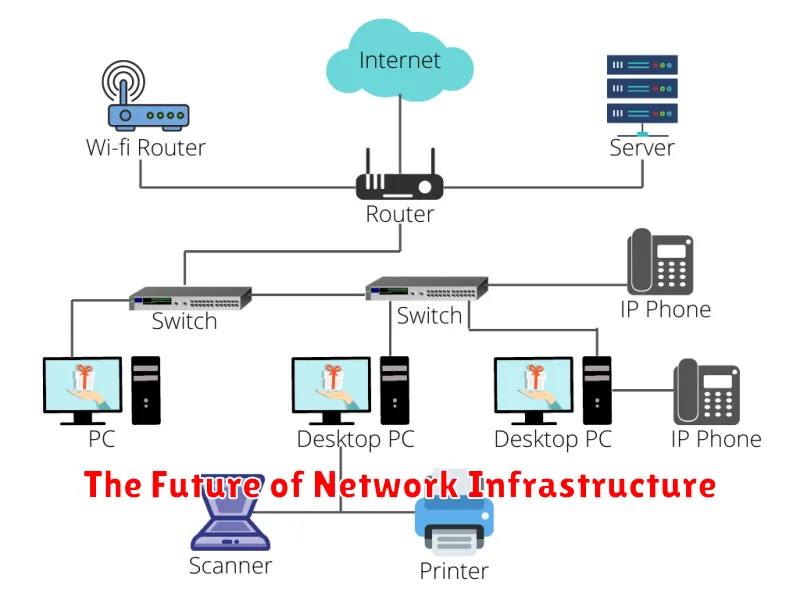
The network infrastructure landscape is constantly evolving, driven by advancements in technology, increasing demands for bandwidth, and the growing adoption of cloud computing and mobile devices. As we look to the future, several key trends are shaping the future of network infrastructure.
One major trend is the rise of software-defined networking (SDN) and network function virtualization (NFV). SDN allows network administrators to control and manage network devices through software, while NFV enables network functions to be virtualized and run on commodity hardware. This approach offers greater flexibility, agility, and scalability, enabling organizations to adapt quickly to changing business needs.
Another key trend is the growing importance of edge computing. As more devices and applications are deployed at the edge of the network, the need for processing and storage closer to users is becoming increasingly critical. Edge computing allows for faster response times, reduced latency, and improved user experience.
The emergence of 5G technology is also transforming network infrastructure. 5G offers significantly higher speeds, lower latency, and greater capacity, enabling new applications and services such as autonomous vehicles, virtual reality, and the Internet of Things (IoT).
As organizations move towards a more interconnected and intelligent future, network infrastructure will need to be highly secure and resilient. Artificial intelligence (AI) and machine learning (ML) will play a crucial role in ensuring network security, detecting and preventing threats, and optimizing network performance.
The future of network infrastructure is dynamic and exciting. By embracing these emerging trends, organizations can build robust and secure networks that support their business goals and unlock the potential of new technologies.