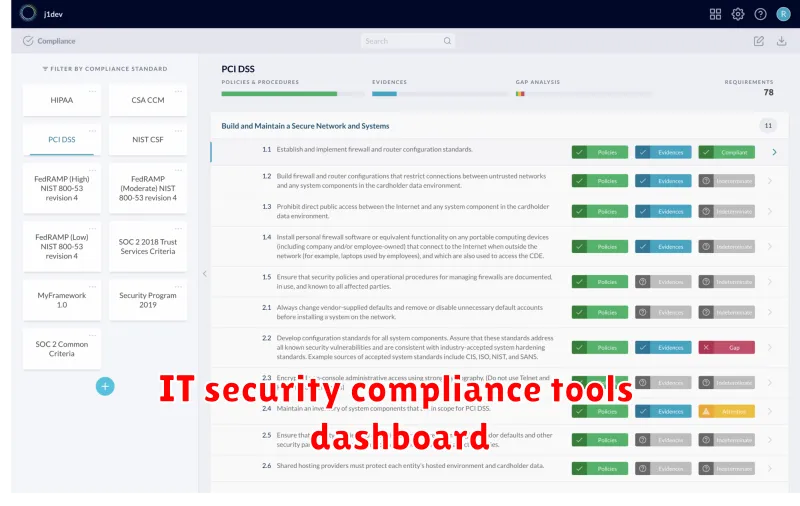
In today’s digital world, data breaches and cyberattacks are becoming increasingly common, making IT security compliance more crucial than ever. Businesses of all sizes are under immense pressure to protect sensitive information and ensure they meet regulatory requirements. Navigating the complex compliance landscape can be a daunting task, but it is essential for protecting your organization and its reputation. This article will explore essential IT security compliance tools that can help you streamline your compliance efforts and build a robust security posture.
From GDPR and HIPAA to PCI DSS and ISO 27001, organizations face a multitude of regulations and standards that dictate how they manage and protect sensitive data. Compliance failures can result in significant financial penalties, legal repercussions, and damage to brand reputation. However, with the right tools and strategies, you can navigate the compliance maze effectively and achieve your security objectives.
Understanding IT Security Compliance
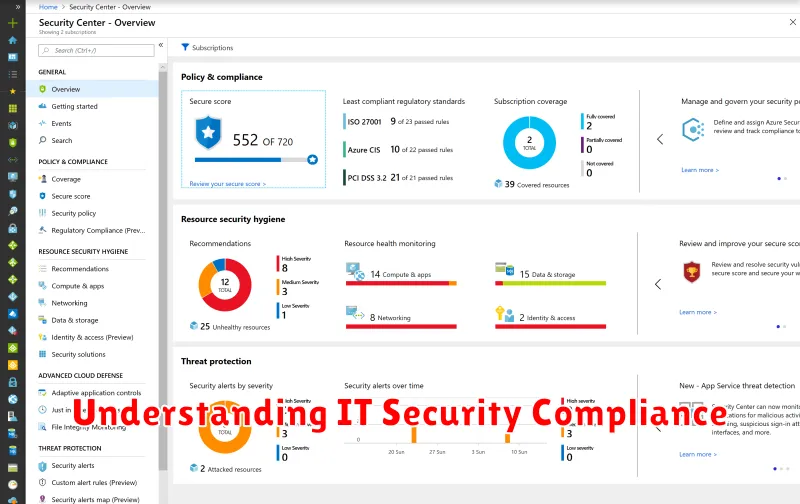
In today’s digitally driven world, where data is the lifeblood of businesses, ensuring robust IT security is paramount. But security is not just about protecting your data; it’s about adhering to legal and regulatory requirements that dictate how you manage and safeguard sensitive information. This is where IT security compliance comes into play.
Essentially, IT security compliance refers to the process of meeting the standards and guidelines set by various organizations and governments. These standards are designed to protect sensitive data, ensuring its confidentiality, integrity, and availability. By complying with these regulations, businesses can mitigate risks, build trust with customers, and avoid hefty fines and penalties.
Think of IT security compliance as a roadmap that outlines the necessary steps to safeguard your data. It encompasses a wide range of activities, including:
- Risk assessments: Identifying potential threats and vulnerabilities.
- Policy development: Establishing clear guidelines for data handling and access.
- Security controls implementation: Deploying measures like firewalls, encryption, and access controls.
- Regular audits and monitoring: Ensuring compliance is maintained and policies are effective.
Understanding IT security compliance is crucial for businesses of all sizes. By embracing its principles and implementing the necessary measures, you can create a secure environment that protects your data, your customers, and your reputation.
Key Compliance Frameworks and Regulations
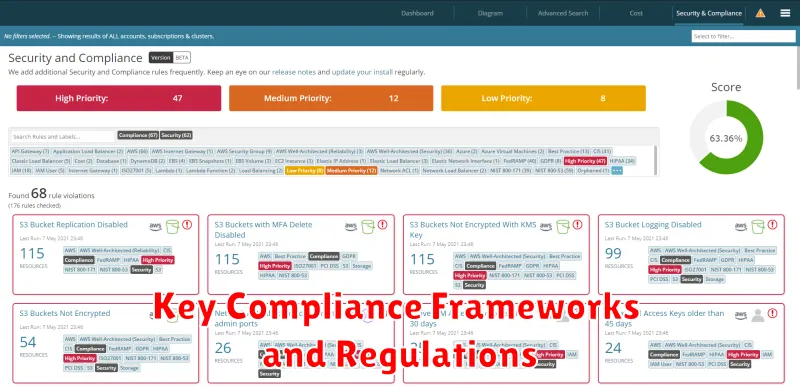
Navigating the complex world of IT security can be daunting, but understanding key compliance frameworks and regulations is crucial. These frameworks provide a roadmap for organizations to build robust security programs, protect sensitive data, and mitigate risks. Let’s delve into some of the most prevalent and impactful frameworks:
General Data Protection Regulation (GDPR)
The GDPR, a landmark regulation from the European Union, governs the processing of personal data of individuals within the EU. It emphasizes data privacy and control, requiring organizations to obtain explicit consent for data use, implement robust security measures, and provide individuals with data access and deletion rights.
California Consumer Privacy Act (CCPA)
California’s CCPA, similar to GDPR, grants consumers extensive rights regarding their personal information. It requires businesses to disclose how they collect, use, and sell personal data, and allows individuals to request deletion or access to their data.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA, a US federal law, focuses on protecting the privacy and security of sensitive health information (PHI). It mandates strict security protocols for healthcare organizations, covering electronic health records, patient data, and medical information.
Payment Card Industry Data Security Standard (PCI DSS)
The PCI DSS is a set of security standards designed to protect credit card data. It mandates strict controls for handling, processing, and storing cardholder information, ensuring its security and preventing fraudulent activities.
ISO 27001
ISO 27001, an internationally recognized standard, outlines an Information Security Management System (ISMS). It helps organizations establish, implement, and maintain a comprehensive framework for managing information security risks, including confidentiality, integrity, and availability.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology, provides a voluntary framework for organizations to manage cybersecurity risks. It offers guidance on identifying, assessing, and mitigating risks across five core functions: identify, protect, detect, respond, and recover.
The Importance of IT Compliance Tools
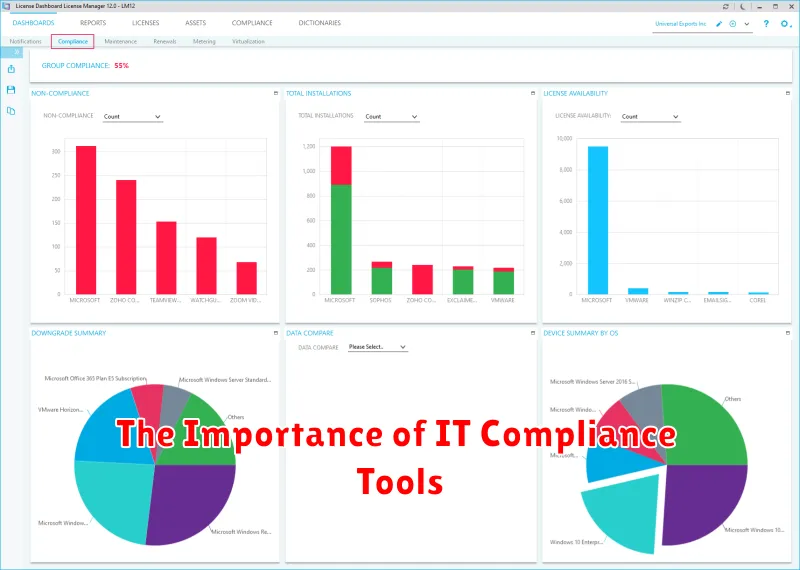
In today’s digital world, safeguarding sensitive data and ensuring compliance with regulations is paramount. This is where IT compliance tools play a crucial role. These tools are designed to automate and streamline compliance processes, reducing the risk of costly breaches and penalties.
Why are IT compliance tools important?
- Reduced Risk of Non-Compliance: By automating compliance tasks and providing real-time monitoring, these tools help organizations identify and address potential vulnerabilities before they become major issues.
- Streamlined Compliance Processes: IT compliance tools centralize and simplify compliance procedures, eliminating manual processes and reducing the burden on IT staff.
- Enhanced Data Security: These tools help organizations implement robust security measures, including encryption, access control, and data loss prevention, to protect sensitive data from unauthorized access.
- Improved Audit Readiness: By providing comprehensive documentation and reporting capabilities, IT compliance tools make it easier for organizations to prepare for audits and demonstrate compliance to regulators.
- Cost Savings: Investing in IT compliance tools can actually save organizations money by reducing the risk of fines, legal fees, and reputational damage.
In conclusion, IT compliance tools are essential for organizations of all sizes to navigate the complex compliance landscape. They provide a comprehensive approach to data security, risk mitigation, and regulatory compliance, ensuring the protection of sensitive information and the overall success of the business.
Types of IT Security Compliance Tools
Navigating the complex world of IT security compliance can be a daunting task. With numerous regulations and standards to adhere to, it’s crucial to have the right tools to ensure your organization is meeting the requirements. IT security compliance tools provide the necessary mechanisms to streamline the process and help you achieve compliance goals.
The types of IT security compliance tools fall into several key categories, each serving a specific function:
- Vulnerability Scanners: These tools identify security weaknesses in systems and applications, such as open ports, outdated software, and misconfigurations. Examples include Nessus, OpenVAS, and Qualys.
- Security Information and Event Management (SIEM) Tools: SIEM systems collect, analyze, and correlate security data from various sources, providing real-time insights into potential threats and security incidents. Popular SIEM solutions include Splunk, IBM QRadar, and LogRhythm.
- Data Loss Prevention (DLP) Tools: DLP software helps organizations prevent sensitive data from leaving the organization’s control. They monitor data transfers and block unauthorized access, ensuring compliance with regulations like GDPR and HIPAA. Common DLP solutions include Symantec Data Loss Prevention, McAfee DLP, and Microsoft Information Protection.
- Endpoint Security Tools: These tools protect individual devices, such as laptops, desktops, and mobile phones, from malware, unauthorized access, and data breaches. Endpoint security solutions include CrowdStrike Falcon, Symantec Endpoint Protection, and McAfee Endpoint Security.
- Compliance Management Platforms: These platforms provide a central hub for managing compliance requirements, automating tasks, and tracking progress. They often include features such as policy management, risk assessment, and reporting. Some popular compliance management platforms include LogicManager, MetricStream, and SailPoint.
The choice of IT security compliance tools depends on the specific needs and requirements of your organization, the regulations you need to comply with, and your existing security infrastructure. It is essential to conduct a thorough assessment of your security needs and choose tools that provide the necessary capabilities to achieve your compliance goals. Remember, investing in the right IT security compliance tools is crucial to protecting your organization from cyber threats and ensuring compliance with applicable regulations.
Risk Assessment and Management Tools
Risk assessment and management tools are crucial for organizations to identify, analyze, and mitigate potential security threats. These tools help in understanding the risks associated with various vulnerabilities and provide actionable insights to improve security posture.
Here are some essential risk assessment and management tools:
- Vulnerability Scanners: These tools scan systems and networks for known vulnerabilities and provide detailed reports on potential weaknesses. Examples include Nessus, OpenVAS, and Qualys.
- Threat Intelligence Platforms: These platforms collect and analyze data from various sources to provide insights into emerging threats and vulnerabilities. Examples include AlienVault OSSIM, ThreatConnect, and Recorded Future.
- Security Information and Event Management (SIEM) Systems: SIEM tools collect and analyze security events from various sources to identify and respond to potential threats. Examples include Splunk, Elastic Stack, and LogRhythm.
- Risk Management Software: These tools help organizations to prioritize risks, develop mitigation plans, and track compliance efforts. Examples include Riskonnect, LogicManager, and Protiviti.
By leveraging these tools, organizations can effectively manage risks, improve their security posture, and enhance compliance with relevant regulations and standards.
Vulnerability Scanning and Management Tools
Vulnerability scanning and management tools are essential for organizations looking to maintain a strong security posture and ensure compliance with regulations. These tools automate the process of identifying and assessing vulnerabilities in systems, applications, and networks.
Vulnerability scanners analyze systems and applications for known weaknesses or exploits. They utilize databases of known vulnerabilities and security best practices to identify potential risks. Scanners can be used for both internal and external assessments, providing insights into the security of an organization’s assets from various angles.
Vulnerability management tools go beyond just identifying vulnerabilities. They provide a centralized platform for managing the entire vulnerability lifecycle. This includes tasks such as:
- Prioritizing vulnerabilities based on severity and risk
- Tracking remediation efforts
- Reporting on security posture
- Integrating with other security tools
By using vulnerability scanning and management tools, organizations can:
- Reduce the risk of security breaches
- Improve compliance with industry standards and regulations
- Gain a better understanding of their security posture
- Optimize their security resources
Some popular vulnerability scanning and management tools include:
- Nessus
- Qualys
- Rapid7 Nexpose
- Tenable.io
- OpenVAS
Choosing the right vulnerability scanning and management tools depends on the specific needs of an organization. Factors to consider include the size of the organization, the complexity of its IT infrastructure, and its budget. It’s important to select tools that are compatible with existing security systems and provide comprehensive reporting capabilities.
Security Information and Event Management (SIEM)
A Security Information and Event Management (SIEM) system is a crucial tool for achieving compliance with various security regulations. SIEM solutions collect, analyze, and correlate security data from different sources across your IT infrastructure. This consolidated view provides a comprehensive understanding of security events, enabling you to detect threats, investigate incidents, and respond quickly.
SIEM solutions offer numerous benefits for compliance efforts:
- Centralized Logging and Monitoring: SIEM systems aggregate logs from diverse sources, facilitating centralized monitoring and analysis of security events. This centralized approach simplifies compliance auditing by providing a single point of access for security data.
- Threat Detection and Response: SIEM solutions employ advanced analytics to identify suspicious activities and potential threats. By correlating events across different systems, SIEM can detect patterns indicative of malicious behavior, enabling proactive threat response.
- Compliance Reporting: SIEM systems generate comprehensive reports on security events, incidents, and compliance status. These reports provide valuable evidence for audits and demonstrate your organization’s commitment to security best practices.
- Incident Response Automation: Some SIEM solutions offer automated incident response capabilities. These features can automatically trigger actions based on predefined rules, such as blocking malicious IP addresses or isolating compromised systems, streamlining the incident response process and minimizing downtime.
By implementing a robust SIEM solution, organizations can significantly enhance their security posture, streamline compliance efforts, and demonstrate their commitment to data protection.
Data Loss Prevention (DLP) Solutions
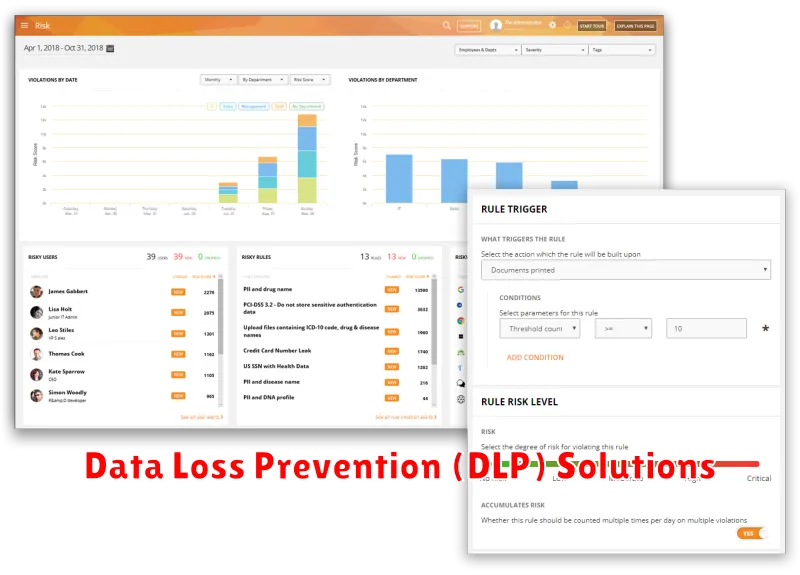
Data loss prevention (DLP) solutions are a critical component of any comprehensive cybersecurity strategy. They are designed to identify, monitor, and prevent sensitive data from leaving your organization’s control. DLP solutions can be implemented in a variety of ways, including through software, hardware, and cloud-based services.
DLP solutions use various methods to detect and prevent data loss, including:
- Content analysis: Analyzing data content to identify sensitive information such as credit card numbers, social security numbers, and intellectual property.
- Contextual analysis: Examining the context of data access and transfer to identify suspicious patterns, such as an employee attempting to download large amounts of data just before leaving the company.
- Network monitoring: Monitoring network traffic for unauthorized data transfers, such as attempts to send sensitive information to external email addresses or cloud storage services.
Benefits of DLP Solutions
Implementing DLP solutions offers numerous benefits, including:
- Protection against data breaches: DLP solutions help prevent sensitive data from falling into the wrong hands, safeguarding your organization from costly data breaches.
- Compliance with regulations: Many regulations, such as HIPAA, PCI DSS, and GDPR, require organizations to implement data loss prevention measures. DLP solutions can help you meet these requirements.
- Improved data security: By identifying and preventing data loss, DLP solutions improve the overall security of your organization’s data.
- Reduced risk of legal liability: In the event of a data breach, having DLP solutions in place can demonstrate your organization’s commitment to data security, potentially reducing legal liability.
Identity and Access Management (IAM) Systems
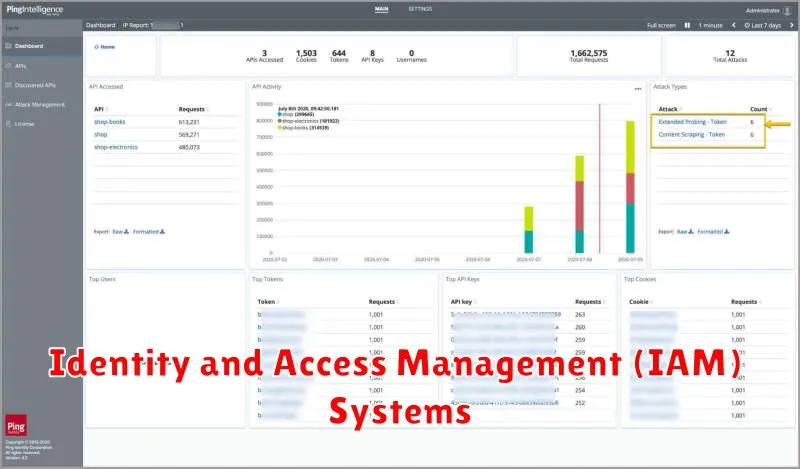
In the realm of IT security compliance, Identity and Access Management (IAM) systems stand as crucial tools for safeguarding sensitive data and maintaining operational integrity. These systems govern user access to digital resources, ensuring that only authorized individuals can interact with specific data and applications. This control over access is paramount for achieving compliance with industry regulations such as GDPR, HIPAA, and PCI DSS.
IAM systems encompass several key components, each playing a vital role in enforcing access control:
- Authentication: Verifies the identity of users attempting to access resources, typically through usernames and passwords, multi-factor authentication, or biometrics.
- Authorization: Defines the level of access granted to authenticated users based on their roles and permissions within the organization.
- Provisioning and De-provisioning: Automatically assigns and revokes user access as needed, simplifying the process of managing user accounts and permissions.
- Auditing and Monitoring: Records user activities and access attempts, providing valuable insights for compliance reporting and security incident investigation.
By implementing robust IAM solutions, organizations can:
- Minimize security risks: Restricting access to sensitive information reduces the likelihood of unauthorized access and data breaches.
- Improve compliance efforts: Provide comprehensive audit trails and reporting capabilities to demonstrate compliance with regulations.
- Enhance operational efficiency: Automate user management processes, freeing up IT staff to focus on other critical tasks.
- Strengthen governance and accountability: Establish clear policies and procedures for user access, promoting transparency and accountability within the organization.
Choosing the right IAM solution depends on several factors, including the size of the organization, the types of resources being protected, and specific compliance requirements. Whether opting for a cloud-based or on-premise solution, a comprehensive IAM strategy is essential for navigating the ever-evolving compliance landscape and safeguarding organizational assets.
Compliance Reporting and Auditing Tools
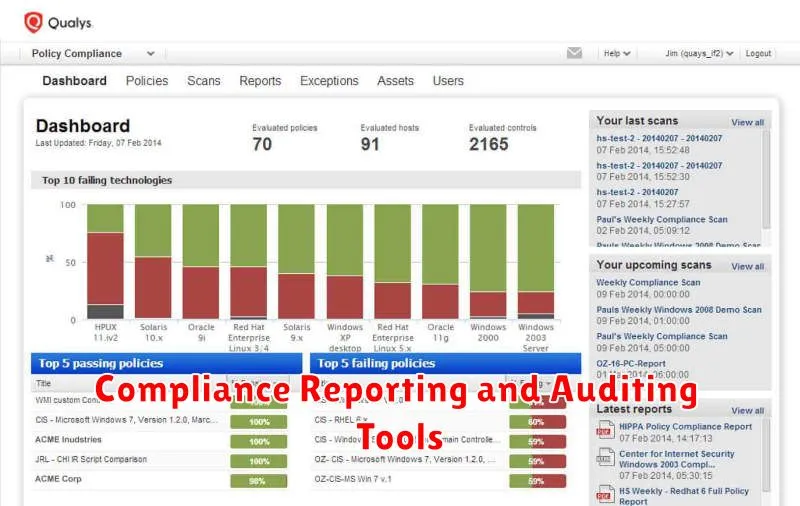
Compliance reporting and auditing tools are essential for any organization seeking to demonstrate its commitment to security standards and regulations. These tools help automate the process of collecting, analyzing, and reporting on security data, streamlining compliance efforts and reducing the risk of non-compliance.
Key features of compliance reporting and auditing tools:
- Automated data collection: These tools can gather data from various sources, including firewalls, intrusion detection systems, and security logs, eliminating the need for manual data gathering.
- Real-time monitoring and reporting: Provide up-to-date insights into security posture and potential vulnerabilities, enabling prompt action to address issues.
- Policy and standard enforcement: Tools can enforce security policies and ensure compliance with relevant regulations like GDPR, HIPAA, and PCI DSS.
- Audit trail and evidence generation: Provide a detailed history of security events and actions, crucial for demonstrating compliance during audits.
- Customizable reporting: Generate reports tailored to specific compliance requirements, simplifying reporting to auditors and regulators.
Benefits of using compliance reporting and auditing tools:
- Reduced risk of non-compliance: By automating compliance tasks and providing real-time insights, these tools minimize the chance of overlooking critical security issues.
- Improved security posture: Proactive monitoring and reporting helps identify and address vulnerabilities before they can be exploited.
- Streamlined audits: Tools generate comprehensive reports, simplifying the auditing process and reducing audit time and costs.
- Enhanced transparency and accountability: Provides a clear and auditable record of security practices and compliance efforts.
Choosing the right compliance reporting and auditing tool depends on the specific needs and requirements of your organization. Consider factors such as the types of regulations you need to comply with, the size and complexity of your IT infrastructure, and your budget.
By leveraging these powerful tools, organizations can effectively navigate the compliance landscape, ensuring robust security practices and minimizing the risk of breaches and penalties.
Choosing the Right Compliance Tools for Your Organization
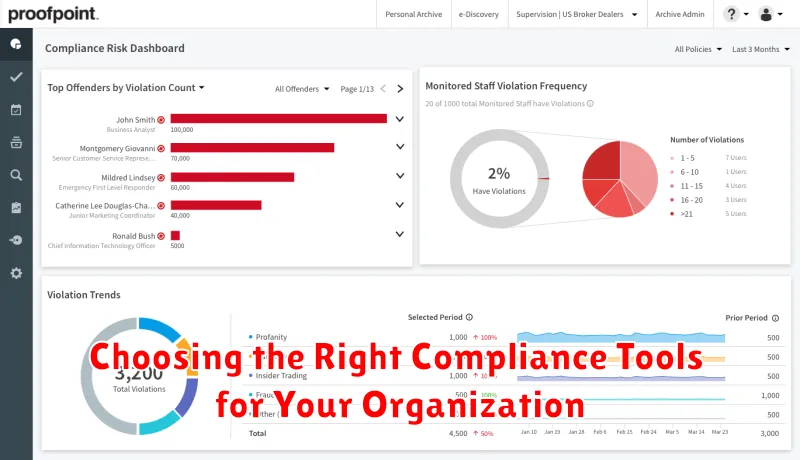
In today’s digital landscape, organizations face a complex and ever-evolving compliance landscape. From data privacy regulations like GDPR and CCPA to industry-specific standards like HIPAA and PCI DSS, staying compliant can be a daunting task. This is where the right compliance tools become essential.
Choosing the right tools can make all the difference in simplifying compliance efforts, reducing risks, and ensuring your organization’s security posture is robust. But with so many options available, how do you determine which tools are best for your specific needs?
Here are some key factors to consider when selecting compliance tools:
1. Understand Your Compliance Requirements
Start by clearly defining your organization’s compliance obligations. Identify the specific regulations and standards that apply to your industry, business operations, and data handling practices. This will help you narrow down the tools that address your specific needs.
2. Evaluate Your Existing Security Infrastructure
Assess the capabilities of your existing security tools and infrastructure. Determine whether you have the necessary controls in place to meet compliance requirements or if there are gaps that need to be addressed. This evaluation will help you identify the areas where compliance tools can provide the most value.
3. Consider Your Budget and Resources
Compliance tools come in a wide range of pricing and complexity. Evaluate your budget constraints and available resources. Look for solutions that offer the right balance of features, functionality, and affordability for your organization.
4. Assess Scalability and Integration
Choose tools that can scale with your organization’s growth and evolving needs. Consider how well the tools integrate with your existing systems and workflows. Seamless integration will minimize disruption and streamline compliance processes.
5. Focus on User-Friendliness and Ease of Use
Compliance tools should be easy to use and understand for your team. Look for solutions with intuitive interfaces, clear documentation, and adequate training resources. User-friendly tools enhance adoption and promote compliance within your organization.
6. Consider Automation and Reporting
Automation features can significantly reduce the time and effort required for compliance tasks. Look for tools that offer automated tasks, reports, and dashboards to simplify compliance management and provide valuable insights into your security posture.
By carefully considering these factors, you can choose compliance tools that effectively address your specific needs, enhance your organization’s security, and simplify the journey towards regulatory compliance.