In today’s rapidly evolving digital landscape, staying ahead of the curve is paramount for businesses of all sizes. As technology advances and cyber threats become increasingly sophisticated, ensuring robust IT security and compliance is no longer a luxury but a necessity. IT audits and compliance are critical components of a comprehensive security strategy, providing valuable insights into your organization’s vulnerabilities and helping you to identify potential risks before they materialize.
But navigating the complex world of IT audit and compliance can be daunting. With an ever-growing array of tools and technologies available, selecting the right solutions for your specific needs can feel overwhelming. This article will explore some of the essential IT audit and compliance tools that can empower your organization to achieve its security goals, minimize risk, and maintain regulatory compliance.
The Importance of IT Audit and Compliance
In today’s digital age, organizations are more reliant on technology than ever before. This reliance brings with it a number of risks, including security breaches, data loss, and compliance violations. To mitigate these risks, organizations must invest in robust IT audit and compliance programs.
IT audits provide a comprehensive assessment of an organization’s IT infrastructure, processes, and controls. They help identify weaknesses and vulnerabilities that could be exploited by attackers or lead to non-compliance. Compliance, on the other hand, ensures that an organization adheres to industry regulations and standards. This includes laws like HIPAA, GDPR, and PCI DSS, which protect sensitive information and ensure ethical data handling.
Why are IT audit and compliance so important?
- Protecting sensitive data: Data breaches can be costly and damaging to an organization’s reputation. IT audits and compliance help ensure that sensitive data is protected from unauthorized access and misuse.
- Ensuring compliance with regulations: Failure to comply with regulations can result in fines, penalties, and legal action. IT audits and compliance help organizations stay up-to-date with changing regulations and avoid costly violations.
- Improving security posture: By identifying vulnerabilities and implementing security controls, IT audits and compliance help organizations strengthen their security posture and reduce the risk of attacks.
- Boosting operational efficiency: IT audits and compliance can help identify opportunities to improve operational efficiency and reduce costs.
- Building trust with stakeholders: Customers, investors, and other stakeholders have a greater level of trust in organizations that demonstrate strong IT audit and compliance practices.
In conclusion, IT audit and compliance are essential for any organization that relies on technology. By investing in these practices, organizations can protect their data, comply with regulations, improve security, enhance efficiency, and build trust with stakeholders.
Types of IT Audits
IT audits are a critical component of any organization’s risk management strategy. They help organizations identify and mitigate potential vulnerabilities, ensure compliance with regulations, and optimize IT performance.
There are various types of IT audits, each focusing on different aspects of an organization’s IT infrastructure and operations. Here are some common types:
Financial Statement Audits
These audits focus on the accuracy and reliability of financial data processed and stored by IT systems. They ensure that financial information is properly recorded, processed, and presented in accordance with Generally Accepted Accounting Principles (GAAP) or International Financial Reporting Standards (IFRS).
Security Audits
Security audits examine an organization’s IT systems and processes to identify potential vulnerabilities and weaknesses that could be exploited by attackers. These audits cover areas such as access control, network security, data encryption, and system hardening.
Compliance Audits
Compliance audits ensure that an organization’s IT systems and practices comply with relevant regulations, standards, and legal requirements. This can include laws like the General Data Protection Regulation (GDPR) or industry-specific standards like PCI DSS (Payment Card Industry Data Security Standard).
Performance Audits
Performance audits assess the efficiency and effectiveness of an organization’s IT systems and processes. They look at factors like system performance, resource utilization, and operational costs to identify areas for improvement.
Operational Audits
Operational audits examine the effectiveness of an organization’s IT operations. They evaluate processes, controls, and procedures to ensure that IT services are delivered efficiently and effectively.
The specific types of IT audits conducted by an organization will depend on its size, industry, and specific risk profile. It’s important to choose the right type of audit to address your organization’s unique needs and objectives.
Key IT Compliance Regulations
Navigating the complex world of IT compliance can be daunting, but it’s essential for any organization looking to protect sensitive data, maintain customer trust, and avoid hefty fines. Understanding the key regulations is the first step towards achieving effective IT compliance.
Here are some of the most prominent regulations that organizations need to be aware of:
- General Data Protection Regulation (GDPR): This EU regulation focuses on protecting personal data of individuals within the EU. It mandates stringent data processing principles, including consent, purpose limitation, and data minimization.
- California Consumer Privacy Act (CCPA): This California law grants consumers more control over their personal data. Organizations handling the data of California residents must comply with requirements for data collection, disclosure, and deletion.
- Health Insurance Portability and Accountability Act (HIPAA): This US law protects sensitive health information (PHI) of individuals. HIPAA compliance requires organizations to implement safeguards to prevent unauthorized access, use, or disclosure of PHI.
- Payment Card Industry Data Security Standard (PCI DSS): This standard applies to organizations that store, process, or transmit credit card information. PCI DSS mandates security controls to protect cardholder data and prevent fraud.
- Sarbanes-Oxley Act (SOX): While not strictly an IT compliance regulation, SOX has a significant impact on IT. It mandates robust internal controls over financial reporting, including IT systems.
These are just a few examples of the many IT compliance regulations that organizations need to be aware of. Staying informed and proactive is crucial for mitigating risks, ensuring data security, and maintaining a competitive advantage.
Essential IT Audit and Compliance Tools
In today’s digital landscape, businesses of all sizes face the daunting task of ensuring their IT systems are secure, compliant, and efficient. This necessitates a robust audit and compliance program, which can be greatly enhanced by leveraging the right tools. These tools streamline the process, automate tasks, and provide valuable insights, allowing organizations to stay ahead of the curve and maintain a strong security posture.
Here are some essential IT audit and compliance tools that every organization should consider:
Vulnerability Scanners
Vulnerability scanners are crucial for identifying security weaknesses in your network, applications, and systems. These tools actively probe your IT infrastructure to discover potential vulnerabilities that could be exploited by attackers. They help you prioritize remediation efforts and proactively address vulnerabilities before they become a major security threat.
Security Information and Event Management (SIEM) Systems
SIEM systems act as a central hub for collecting, analyzing, and correlating security data from various sources within your organization. They provide real-time visibility into your IT environment, detecting anomalies, suspicious activity, and potential security breaches. By consolidating security data, SIEM systems enable you to respond quickly and effectively to incidents, minimizing downtime and potential damage.
Configuration Management Tools
Configuration management tools help you establish and maintain a secure baseline configuration for your systems and applications. They automate the process of configuring, deploying, and managing changes to your IT environment, ensuring consistency and reducing the risk of misconfigurations that can lead to vulnerabilities. These tools also provide detailed documentation of your configurations, making it easier to track changes and audit your security posture.
Data Loss Prevention (DLP) Solutions
DLP solutions are essential for protecting sensitive data from unauthorized access, use, or disclosure. These tools monitor data movement across your network and endpoints, detecting and blocking any attempt to transfer sensitive information outside of your organization. DLP solutions help you comply with data privacy regulations and prevent data breaches that could result in significant financial and reputational damage.
Identity and Access Management (IAM) Solutions
IAM solutions play a critical role in managing user identities and controlling access to your IT resources. They ensure that only authorized users have access to the information and systems they need to perform their jobs. IAM tools automate the provisioning, deprovisioning, and management of user accounts, reducing manual errors and improving security. They also provide detailed audit logs, allowing you to track user activity and identify any suspicious behavior.
Implementing the right IT audit and compliance tools can significantly enhance your organization’s security posture and ensure compliance with relevant regulations. By leveraging these tools, businesses can stay ahead of the curve, mitigate risks, and protect their valuable assets in today’s increasingly complex and threat-filled digital landscape.
Data Security and Privacy Tools

In today’s digital age, data security and privacy are paramount. With the ever-increasing threat of cyberattacks and data breaches, it’s crucial for organizations to have robust tools and processes in place to safeguard sensitive information.
Data Loss Prevention (DLP) tools are essential for identifying and blocking attempts to exfiltrate sensitive data from the organization’s network. These tools can monitor data in real-time and flag any suspicious activity, such as attempts to copy confidential documents to unauthorized devices or share them via email.
Encryption tools play a critical role in protecting data at rest and in transit. Encryption transforms data into an unreadable format, making it inaccessible to unauthorized individuals. Organizations can use encryption for data stored on servers, laptops, mobile devices, and even during data transmission over the internet.
Security Information and Event Management (SIEM) tools provide a centralized platform for monitoring security events and generating alerts. They collect data from various sources, such as firewalls, intrusion detection systems, and antivirus software, and use analytics to identify potential security threats.
Identity and Access Management (IAM) tools are crucial for managing user identities and access privileges. By implementing strong authentication methods and granular access controls, IAM tools can help prevent unauthorized access to sensitive data.
Data Masking tools are used to replace sensitive data with non-sensitive substitutes, enabling secure data sharing and testing without compromising privacy. This is particularly useful for organizations that handle sensitive personal data, such as healthcare providers or financial institutions.
Organizations need to invest in these data security and privacy tools to protect their valuable assets. By staying ahead of the curve, they can mitigate risks and ensure the safety of their sensitive data.
Vulnerability Scanning and Management
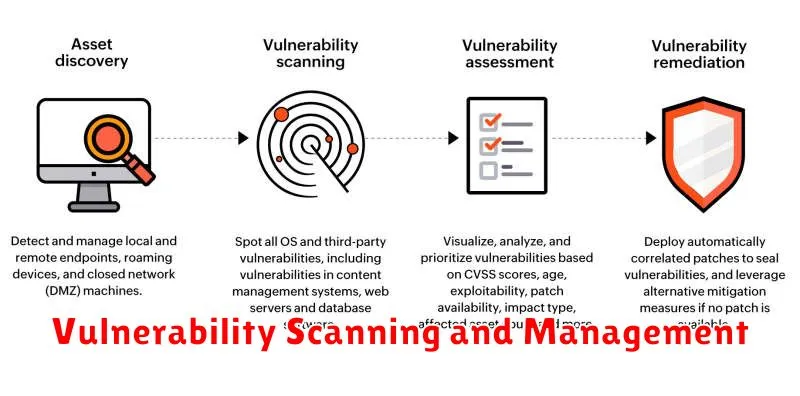
In today’s digitally interconnected world, safeguarding your organization’s data and systems from cyber threats is paramount. Vulnerability scanning and management play a critical role in achieving this goal. Vulnerability scanning involves systematically identifying security flaws and weaknesses within your IT infrastructure. This process helps uncover potential entry points for malicious actors, enabling you to prioritize and address vulnerabilities before they can be exploited.
Effective vulnerability scanning tools go beyond simply identifying weaknesses. They provide actionable insights, enabling you to assess the severity of vulnerabilities and prioritize remediation efforts. Regular vulnerability scanning is crucial for staying ahead of the curve. By scanning frequently, you can detect new vulnerabilities as they emerge, reducing the risk of falling victim to zero-day exploits. Moreover, integrating vulnerability scanning into your regular security practices helps you build a proactive security posture.
Beyond detection, vulnerability management encompasses the entire lifecycle of addressing vulnerabilities. This includes planning, prioritizing, and implementing remediation strategies. It also involves ongoing monitoring and reporting to ensure that vulnerabilities are addressed effectively and that your security posture remains robust. A comprehensive vulnerability management program helps organizations achieve compliance with industry regulations and standards, strengthening their overall security posture and reducing their risk exposure.
Security Information and Event Management (SIEM)
In the ever-evolving landscape of cyber threats, maintaining robust security is paramount for any organization. A crucial tool in this endeavor is Security Information and Event Management (SIEM). SIEM solutions play a pivotal role in detecting, analyzing, and responding to security incidents by aggregating and correlating security data from various sources within your IT infrastructure.
SIEM systems act as a centralized hub, collecting logs, security alerts, and events from firewalls, intrusion detection systems (IDS), antivirus software, and other security tools. This consolidated view provides a comprehensive understanding of potential security threats and anomalies, enabling faster identification and response. By correlating events across different systems, SIEM can uncover hidden patterns and malicious activities that might otherwise go unnoticed.
Key benefits of implementing a SIEM solution include:
- Enhanced Threat Detection: SIEM’s ability to analyze and correlate security data significantly improves the detection of both known and unknown threats.
- Faster Incident Response: By providing real-time visibility into security events, SIEM enables faster incident response times, minimizing potential damage.
- Improved Security Posture: SIEM provides valuable insights into security vulnerabilities and weaknesses, helping organizations strengthen their overall security posture.
- Compliance Reporting: SIEM facilitates compliance reporting by providing audit trails and logs that are crucial for meeting regulatory requirements.
SIEM solutions are a valuable asset for organizations of all sizes looking to bolster their security posture and stay ahead of the ever-evolving threat landscape. By investing in a robust SIEM system, you can gain real-time visibility into your security environment, detect threats more effectively, and respond to incidents with greater agility.
Governance, Risk, and Compliance (GRC) Platforms

In today’s dynamic business environment, organizations face a myriad of challenges in managing governance, risk, and compliance (GRC). From evolving regulatory landscapes to cybersecurity threats, navigating these complexities effectively is crucial for sustainable success. This is where GRC platforms come into play, offering a comprehensive solution to streamline and centralize these critical functions.
GRC platforms provide a central repository for managing policies, procedures, and risk assessments. They empower organizations to:
- Identify and assess risks across various business units and operations.
- Establish clear governance frameworks to ensure accountability and transparency.
- Implement robust compliance programs to adhere to industry standards and regulations.
- Monitor and report on GRC activities to track progress and identify areas for improvement.
By leveraging these features, GRC platforms enable organizations to proactively manage risks, optimize compliance efforts, and enhance overall operational efficiency. They offer a holistic view of GRC processes, fostering collaboration among teams and providing valuable insights for informed decision-making.
Benefits of Using IT Audit and Compliance Tools

In today’s digital landscape, organizations are increasingly reliant on technology. This reliance creates a need for robust IT audit and compliance programs to ensure data security, privacy, and regulatory compliance. Implementing IT audit and compliance tools can significantly improve an organization’s security posture, reduce risk, and optimize operational efficiency.
Here are some of the key benefits of using IT audit and compliance tools:
Enhanced Security Posture
These tools help organizations identify and mitigate security vulnerabilities by automating tasks such as vulnerability scanning, penetration testing, and security monitoring. They provide real-time insights into potential threats, allowing for proactive security measures to be taken. This, in turn, helps organizations reduce the risk of data breaches and other security incidents.
Improved Compliance
Organizations must comply with various regulations such as GDPR, HIPAA, and PCI DSS. IT audit and compliance tools help streamline the compliance process by automating audits, providing evidence for regulatory requirements, and ensuring continuous monitoring of compliance activities. This reduces the risk of non-compliance penalties and reputational damage.
Increased Efficiency
IT audit and compliance tools automate many manual tasks, such as data collection, report generation, and risk assessment. This allows IT professionals to focus on more strategic initiatives, increasing overall operational efficiency.
Cost Savings
By improving security and compliance, IT audit and compliance tools help organizations reduce the costs associated with security incidents, non-compliance penalties, and remediation efforts. Additionally, the automation of tasks can lead to significant cost savings in the long run.
Better Risk Management
These tools provide comprehensive risk assessment capabilities, allowing organizations to identify and prioritize risks, develop mitigation strategies, and track the effectiveness of their risk management program. This helps organizations make informed decisions about their security investments and resource allocation.
In conclusion, using IT audit and compliance tools offers numerous benefits, including enhanced security, improved compliance, increased efficiency, cost savings, and better risk management. Organizations that invest in these tools can significantly strengthen their security posture, improve their operational efficiency, and achieve greater peace of mind in today’s complex and ever-evolving threat landscape.