In today’s hyper-connected world, navigating the digital landscape can feel like a constant balancing act. While technology offers unprecedented convenience and access, it also poses unique challenges to our data privacy. With every online interaction, we leave a digital footprint, and the responsibility to protect this sensitive information rests squarely on our shoulders. From social media platforms to online shopping, our personal data is constantly being collected and utilized, raising critical questions about data security and compliance.
This article delves into the crucial aspects of navigating the digital age while safeguarding your data privacy. We’ll explore the latest regulations, best practices, and essential steps to take control of your online presence and ensure your sensitive information remains protected. Join us as we unravel the complexities of data privacy compliance and empower you to confidently navigate the digital realm.
Introduction: The Importance of Data Privacy in the Digital Landscape
In today’s digitally connected world, data is the new currency. From our online shopping habits to our social media interactions, a vast amount of personal information is constantly being collected and shared. While this data can be used to enhance our online experiences and provide personalized services, it also raises significant concerns about data privacy.
Data privacy is paramount in the digital landscape for several crucial reasons. It protects individuals from potential harm such as identity theft, financial fraud, and reputational damage. By safeguarding personal information, we empower individuals to control their digital identities and ensure that their data is used responsibly and ethically.
Furthermore, data privacy fosters trust in the digital ecosystem. When individuals feel confident that their data is protected, they are more likely to engage in online activities, share personal information, and participate in the digital economy. A strong data privacy framework fosters a culture of transparency, accountability, and responsible data handling.
Key Data Privacy Regulations: GDPR, CCPA, and More
The digital age has brought with it a wealth of data, but it has also raised concerns about data privacy and security. As businesses increasingly collect and process personal information, it’s crucial to understand and comply with the growing number of data privacy regulations worldwide. Two of the most prominent regulations are the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), each with its own set of rules and requirements.
GDPR, enacted by the European Union, applies to any organization that processes personal data of individuals within the EU, regardless of the organization’s location. It focuses on giving individuals greater control over their data, with key principles like lawfulness, fairness, and transparency. GDPR also introduces strict requirements for data security, breach notification, and data subject rights, such as the right to access, rectification, and erasure.
CCPA, a California-specific law, provides consumers with greater control over their personal information collected by businesses. It requires businesses to disclose the categories of personal information collected, the purposes for which it is used, and the third parties with whom it is shared. CCPA also grants consumers the right to access, delete, and opt-out of the sale of their personal information.
Beyond GDPR and CCPA, other data privacy regulations are emerging globally, such as the Brazilian General Data Protection Law (LGPD) and the Canadian Personal Information Protection and Electronic Documents Act (PIPEDA). These regulations all share a common goal: to protect individuals’ personal data and ensure its responsible use.
Navigating the complex landscape of data privacy regulations can be challenging. It’s crucial for businesses to understand the scope of these regulations, assess their data collection and processing practices, and implement appropriate compliance measures. Failure to comply with these regulations can result in significant penalties and reputational damage.
Understanding Data Subject Rights
In the digital age, data privacy has become paramount. Individuals are increasingly aware of the importance of controlling their personal information. This has led to the emergence of robust data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). At the heart of these regulations lie data subject rights, which empower individuals to exercise control over their personal data.
Data subject rights are a set of legal rights that individuals have over their personal data. These rights allow individuals to understand how their data is being used, access their data, correct inaccuracies, restrict or delete their data, and even object to its processing. Let’s delve deeper into these essential rights:
- Right to Access: Individuals have the right to request access to their personal data held by an organization. This enables them to understand what information is being stored, for what purpose, and with whom it is being shared.
- Right to Rectification: This right allows individuals to correct any inaccurate or incomplete personal data held by an organization. It ensures that the data being processed is accurate and up-to-date.
- Right to Erasure (Right to Be Forgotten): Individuals have the right to request the deletion of their personal data under certain circumstances. This includes situations where the data is no longer necessary for the original purpose, consent is withdrawn, or the data is processed unlawfully.
- Right to Restriction of Processing: Individuals can request the restriction of processing their data in specific cases. For example, if the accuracy of the data is disputed or the data is being processed unlawfully.
- Right to Data Portability: This right allows individuals to receive their personal data in a portable format and transmit it to another organization without hindrance. It promotes data mobility and empowers individuals to choose service providers.
- Right to Object: Individuals have the right to object to the processing of their personal data on grounds relating to their particular situation or if the processing is for direct marketing purposes.
Understanding and respecting these data subject rights is crucial for organizations operating in the digital age. By adhering to these rights, organizations can build trust with their customers and maintain data privacy compliance.
Data Protection Principles: Lawfulness, Fairness, Transparency
In the digital age, where our personal information is constantly being collected and processed, ensuring data privacy compliance is paramount. At the heart of this compliance lie the fundamental principles of data protection, which guide how organizations should handle our data. Among these principles, lawfulness, fairness, and transparency are particularly crucial, forming the bedrock of responsible data processing.
Lawfulness dictates that the collection and use of personal data must have a legal basis. This means that organizations need to have a legitimate reason for processing data, such as obtaining consent, fulfilling a contract, or complying with legal obligations. Fairness implies that data processing should be conducted in a way that is ethical and respectful of individuals’ rights. This includes avoiding discriminatory practices and ensuring that individuals are treated fairly and equitably. Transparency is essential for empowering individuals to understand how their data is being used. Organizations must be open and clear about their data processing practices, providing individuals with readily accessible information about what data they collect, why they collect it, and how they use it.
These three principles work together to create a framework for responsible data management. By adhering to them, organizations can build trust with individuals, promote data security, and ensure that personal information is handled appropriately. In essence, they serve as guiding lights in the digital landscape, helping navigate the complex world of data protection and safeguard our privacy in the digital age.
Data Security Measures: Protecting Personal Information
In today’s digital age, where information flows freely, ensuring data privacy compliance is paramount. As individuals and organizations alike navigate the vast digital landscape, protecting personal information from unauthorized access and misuse is crucial. Data security measures play a critical role in this endeavor, safeguarding sensitive data and fostering trust in the digital realm.
One cornerstone of data security is the implementation of robust access controls. This involves establishing clear and defined permissions for accessing and manipulating data, ensuring that only authorized individuals have the necessary privileges. Strong passwords and multi-factor authentication are essential components of access control, adding an extra layer of protection against unauthorized entry.
Data encryption, another crucial measure, transforms data into an unreadable format, rendering it incomprehensible to unauthorized parties. Encryption safeguards data during transmission and storage, preventing interception and misuse. Encryption algorithms, such as AES and RSA, are widely employed to ensure data confidentiality.
Regular security audits are essential for identifying and mitigating potential vulnerabilities. These audits involve comprehensive assessments of systems, networks, and applications, uncovering any weaknesses that could compromise data security. By proactively addressing vulnerabilities, organizations can strengthen their defenses against data breaches.
Employee training is vital to fostering a culture of data security within organizations. By educating employees about best practices, such as strong password hygiene and recognizing phishing attempts, organizations can reduce the risk of human error, a common cause of data breaches. Regular training and awareness programs are essential for keeping employees informed and vigilant.
Data Breach Notification and Response
In today’s digital age, data security is paramount. With the increasing prevalence of cyberattacks and data breaches, it’s crucial for organizations to have a robust data breach notification and response plan in place. This plan should outline clear steps for identifying, containing, and mitigating the impact of a breach, as well as informing affected individuals and relevant authorities.
A data breach notification is the process of informing individuals whose personal information has been compromised. This notification should be prompt, transparent, and concise, providing clear details about the breach, the information affected, and steps individuals can take to protect themselves.
The response to a data breach involves a multi-faceted approach:
- Incident Response: Containing the breach, stopping further data exfiltration, and securing affected systems.
- Forensics: Determining the extent of the breach, the data compromised, and the source of the attack.
- Notification: Informing individuals, regulatory bodies, and potentially the media.
- Recovery: Restoring affected systems and data, and implementing measures to prevent future breaches.
A well-defined data breach notification and response plan helps organizations:
- Minimize the impact of a breach by acting swiftly and effectively.
- Comply with legal and regulatory requirements, such as the GDPR and CCPA.
- Maintain trust with customers and stakeholders by being transparent and accountable.
By proactively implementing a robust data breach notification and response plan, organizations can better protect their data, minimize the impact of breaches, and maintain the trust of their customers and stakeholders.
Building a Culture of Data Privacy Compliance
In the digital age, where data is the new currency, ensuring data privacy compliance is paramount. It’s not just about ticking boxes or meeting legal requirements; it’s about cultivating a culture of responsibility within your organization.
Building this culture starts at the top. Leaders need to be vocal advocates for data privacy, demonstrating their commitment through actions and policies. This includes:
- Setting clear expectations for data handling and security.
- Providing robust training to all employees on data privacy laws, policies, and best practices.
- Creating channels for open communication about data privacy concerns.
- Promoting a “privacy-first” mindset across all departments and functions.
Beyond leadership, fostering a culture of data privacy compliance requires employee engagement. This means making data privacy everyone’s responsibility, not just the IT department’s. Encourage employees to:
- Think critically about data collection and usage, asking questions like “Why do we need this data?” and “Is this data truly necessary?”
- Be mindful of data security, implementing strong passwords and avoiding phishing scams.
- Report any potential privacy violations promptly, ensuring quick action and remediation.
Building a culture of data privacy compliance is an ongoing journey. It requires constant vigilance, education, and a commitment to ethical data handling. By prioritizing data privacy, you not only protect your organization from legal and financial risks, but also build trust and loyalty with your customers, employees, and partners. This is essential for success in the digital age.
The Role of Technology in Data Privacy
In today’s digital age, where data is constantly being collected and analyzed, ensuring data privacy has become paramount. Technology plays a crucial role in navigating this complex landscape, providing tools and solutions that empower individuals and organizations to protect sensitive information.
One of the key roles of technology in data privacy is the implementation of encryption. Encryption transforms data into an unreadable format, making it inaccessible to unauthorized individuals. This is essential for safeguarding sensitive information such as financial records, medical data, and personal details.
Data masking is another technology that plays a vital role in data privacy. This technique involves replacing sensitive data with non-sensitive substitutes, ensuring that real data remains protected while still allowing for testing and analysis.
Furthermore, access control mechanisms, such as role-based access control (RBAC), allow organizations to restrict access to specific data based on user roles and permissions. This ensures that only authorized personnel can view and manipulate sensitive information.
Technology also empowers individuals to control their data privacy. Privacy-enhancing technologies (PETs), such as differential privacy and homomorphic encryption, enable individuals to share their data while maintaining their privacy.
In conclusion, technology plays a multifaceted role in data privacy, providing tools and solutions that safeguard sensitive information and empower individuals and organizations to navigate the digital age responsibly.
Future Challenges and Trends in Data Privacy
The digital age has brought unparalleled convenience and opportunity, but it has also ushered in a new era of data privacy concerns. As technology continues to evolve at an unprecedented pace, so too do the challenges and trends shaping the future of data privacy.
One of the most significant challenges is the growing volume and complexity of data. With the rise of Internet of Things (IoT) devices, artificial intelligence (AI), and big data analytics, organizations are collecting and processing more data than ever before. This poses a significant challenge for data privacy compliance, as it becomes increasingly difficult to ensure the security and confidentiality of sensitive information.
Another challenge is the emergence of new technologies that blur the lines of data ownership and control. For example, blockchain technology has the potential to revolutionize data management, but it also raises questions about who owns and controls data stored on a decentralized ledger.
Looking ahead, there are several key trends that will shape the future of data privacy. One is the increasing importance of privacy-enhancing technologies (PETs). PETs are designed to protect data privacy while still allowing for data analysis and sharing. These technologies include differential privacy, homomorphic encryption, and federated learning.
Another trend is the growing focus on data governance and compliance. As regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) become more stringent, organizations will need to invest in robust data governance frameworks to ensure compliance. This includes implementing strong data security measures, providing transparent data privacy policies, and establishing clear data retention policies.
Finally, there is an increasing emphasis on user education and empowerment. Individuals are becoming more aware of their data privacy rights and demanding greater control over their personal information. This trend will drive the development of new tools and resources that empower users to manage their privacy preferences and protect their data.
Navigating the digital age requires a proactive approach to data privacy. By understanding the challenges and trends, organizations and individuals can take steps to ensure the security and confidentiality of sensitive information. As technology continues to evolve, it is crucial to remain vigilant and adapt to the changing landscape of data privacy.
Data Privacy Regulations

The digital age has brought about an unprecedented amount of data collection and sharing. With the rise of online platforms, social media, and the Internet of Things, our personal information is constantly being gathered and processed. This has led to growing concerns about data privacy and the need for robust regulations to protect individuals.
Data privacy regulations aim to establish rules and guidelines for the collection, processing, and storage of personal data. These regulations vary across jurisdictions, but they generally share common principles such as:
- Transparency: Individuals should be informed about how their data is being collected, used, and shared.
- Consent: Individuals should have the right to give their explicit consent before their data is processed.
- Access and Rectification: Individuals should be able to access and rectify their personal data.
- Security: Organizations should implement appropriate security measures to protect personal data from unauthorized access, use, or disclosure.
- Data Minimization: Organizations should only collect and process the data that is necessary for their legitimate purposes.
Some of the prominent data privacy regulations worldwide include:
- General Data Protection Regulation (GDPR): This regulation applies to all organizations that process personal data of individuals in the European Union. It is considered one of the most comprehensive data privacy regulations globally.
- California Consumer Privacy Act (CCPA): This law provides Californians with enhanced data privacy rights, including the right to know, delete, and opt-out of the sale of their personal data.
- Canadian Personal Information Protection and Electronic Documents Act (PIPEDA): This federal law governs the collection, use, and disclosure of personal information by organizations in Canada.
Compliance with data privacy regulations is crucial for organizations operating in the digital age. Failure to comply can result in significant penalties, legal challenges, and reputational damage. It is essential for organizations to implement robust data privacy programs, train their employees on data protection best practices, and stay informed about evolving regulatory landscapes.
Data Protection Principles
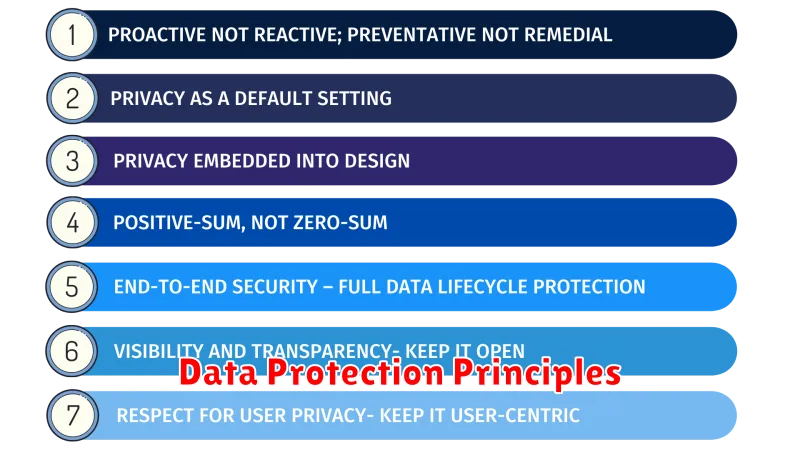
In the digital age, where data is the new currency, ensuring data privacy compliance is crucial for individuals and organizations alike. Data protection principles serve as the foundational guidelines for safeguarding personal information and fostering trust in digital interactions. These principles, often enshrined in laws and regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), provide a framework for responsible data handling practices.
Fairness and lawfulness: Data processing must be fair, transparent, and legal, respecting individual rights and avoiding discriminatory practices. This principle emphasizes the importance of clear and understandable information about data processing activities.
Purpose limitation: Data should be collected for specific, explicit, and legitimate purposes, and not used for purposes beyond those initially stated. This principle promotes transparency and prevents the misuse of data for unintended purposes.
Data minimization: Only the necessary data should be collected and processed. This principle advocates for responsible data collection and storage, minimizing the potential for unauthorized access or breaches.
Accuracy: Personal data should be accurate and kept up to date. This principle emphasizes the importance of data quality and the need to correct inaccuracies promptly.
Storage limitation: Data should be stored only for as long as necessary to fulfill the purposes for which it was collected. This principle promotes data retention policies that strike a balance between data preservation and privacy.
Integrity and confidentiality: Data must be protected from unauthorized access, use, disclosure, alteration, or destruction. This principle emphasizes the importance of robust security measures to safeguard sensitive information.
Accountability: Organizations are responsible for demonstrating compliance with data protection principles. This principle emphasizes transparency and accountability in data handling practices, enabling individuals to exercise their rights and seek redress if necessary.
Adhering to these data protection principles is essential for building trust and fostering a secure digital environment. Individuals can empower themselves by understanding their rights and engaging with organizations that prioritize data privacy. By upholding these principles, we can navigate the digital age responsibly, ensuring that data is used ethically and that individual rights are protected.
Data Privacy Compliance Checklist

In today’s digital age, data privacy is a critical concern for businesses of all sizes. With increasing regulations and growing consumer awareness, it’s more important than ever to ensure that your organization is compliant with data privacy laws. This checklist provides a starting point for your journey towards data privacy compliance.
1. Identify and Assess Data:
- What types of personal data does your organization collect?
- Where is this data stored?
- How long do you retain it?
- What are the risks associated with this data?
2. Implement Strong Security Measures:
- Use robust access controls to restrict data access to authorized personnel only.
- Encrypt sensitive data both in transit and at rest.
- Implement regular security assessments and vulnerability scans.
- Maintain a strong security awareness program for all employees.
3. Establish Clear Privacy Policies and Procedures:
- Develop comprehensive privacy policies that clearly explain how you collect, use, and protect personal data.
- Establish clear procedures for data subject requests, including access, correction, and deletion.
- Ensure that your policies are easily accessible and understandable to all stakeholders.
4. Obtain Consent:
- Obtain explicit consent from individuals before collecting, using, or disclosing their personal data.
- Ensure that consent is freely given, specific, informed, and unambiguous.
- Document consent and provide individuals with the ability to withdraw it at any time.
5. Appoint a Data Protection Officer (DPO):
- Consider appointing a dedicated Data Protection Officer (DPO) to oversee data privacy compliance efforts.
- The DPO should have a deep understanding of data privacy laws and best practices.
6. Regularly Review and Update Policies:
- Stay informed about the latest data privacy regulations and best practices.
- Review and update your policies, procedures, and security measures accordingly.
7. Prepare for Data Breaches:
- Develop a comprehensive data breach response plan that outlines steps to take in the event of a breach.
- Ensure that you have the necessary resources and expertise to respond effectively and promptly to data breaches.
This checklist is just a starting point, and specific requirements may vary depending on your industry, location, and the types of data you collect. It is essential to consult with legal counsel to ensure that you are meeting all applicable data privacy requirements. By implementing these steps, you can build a strong foundation for data privacy compliance and protect your organization and your customers.
Data Breach Response
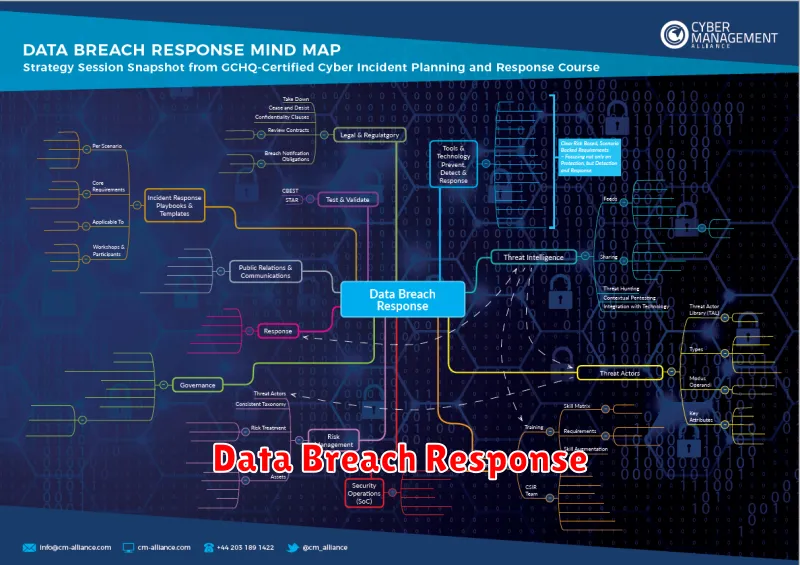
In the digital age, safeguarding sensitive data is paramount. Data breaches can have severe consequences, impacting individuals, organizations, and the broader economy. Effective data breach response is crucial for mitigating damage, restoring trust, and ensuring compliance with regulations. A comprehensive approach involves:
Prompt Detection and Containment: Swift identification of a breach is essential to minimize the extent of data compromise. Organizations must employ robust security monitoring tools and practices to detect anomalies and suspicious activity.
Incident Response Plan: Having a well-defined incident response plan is paramount. This plan should outline clear steps for investigation, containment, remediation, and communication. It should also involve key stakeholders, including legal counsel, IT experts, and communication specialists.
Notification and Transparency: In the event of a breach, organizations must promptly notify affected individuals and relevant authorities. Transparency is crucial for building trust and mitigating potential reputational damage. Clear and concise communication regarding the breach, its impact, and steps taken to address it is essential.
Remediation and Recovery: After a breach, organizations must take steps to remediate the vulnerabilities that led to the compromise. This involves patching systems, strengthening security measures, and implementing new controls to prevent future incidents.
Data Recovery and Backup: Regular data backups are crucial for business continuity and data recovery. In the event of a breach, organizations can restore critical data and minimize disruptions.
Legal and Regulatory Compliance: Organizations must comply with data privacy regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations require specific actions following a data breach, including reporting and notification requirements.
Post-Breach Review and Lessons Learned: Following a breach, a thorough review of the incident is crucial to identify weaknesses in security practices. This analysis helps organizations improve their defenses, enhance their incident response capabilities, and prevent future breaches.
Data Privacy Best Practices

In today’s digital age, data privacy is paramount. Organizations must prioritize protecting sensitive information to maintain trust with customers and comply with regulations. Implementing robust data privacy best practices is essential to safeguard data and ensure a secure digital environment. Here’s a comprehensive guide to navigating the digital landscape and upholding data privacy standards.
Implement Strong Data Security Measures
Data security forms the cornerstone of data privacy. Implement robust measures to protect sensitive information from unauthorized access, use, disclosure, alteration, or destruction. This includes:
- Encryption: Encrypt data both at rest and in transit using strong encryption algorithms.
- Access Control: Implement granular access controls, granting only authorized individuals access to specific data.
- Multi-factor Authentication (MFA): Enhance account security by requiring multiple forms of verification before granting access.
- Regular Security Audits: Conduct regular security assessments to identify and mitigate potential vulnerabilities.
- Employee Training: Educate employees on data security best practices and their responsibilities in protecting sensitive information.
Adopt a Privacy-by-Design Approach
Integrate data privacy considerations into every stage of the software development lifecycle. This “privacy-by-design” approach ensures that data protection is built into systems from the outset:
- Data Minimization: Collect only the data necessary for specific purposes and avoid excessive collection.
- Purpose Limitation: Clearly define the purposes for which data is collected and use it only for those designated purposes.
- Data Retention Policies: Establish clear data retention policies to delete or anonymize data when it is no longer needed.
Transparency and Accountability
Be transparent with individuals about how their data is collected, used, and shared. Provide clear and concise privacy notices that are easy to understand. Establish mechanisms for individuals to exercise their data rights, including:
- Access: Allow individuals to access their personal data.
- Rectification: Enable individuals to correct inaccurate data.
- Erasure: Provide individuals with the ability to delete their data.
- Restriction: Allow individuals to restrict the processing of their data.
- Data Portability: Enable individuals to receive their data in a portable format.
Compliance with Data Privacy Regulations
Stay informed about and comply with relevant data privacy regulations, such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and other regional or national privacy laws. This includes:
- Appointing a Data Protection Officer (DPO): Designate a responsible individual to oversee data privacy compliance.
- Maintaining Records: Document data processing activities and maintain comprehensive records for audits.
- Data Breach Notification: Implement procedures for promptly notifying individuals and authorities in case of data breaches.
By implementing these data privacy best practices, organizations can foster trust, protect sensitive information, and navigate the digital age with confidence.

