In the ever-evolving landscape of technology, cybersecurity is an increasingly critical concern. As we enter 2024, the threat landscape continues to shift, presenting new challenges and opportunities for organizations and individuals alike. To stay ahead of the curve and protect sensitive data, it’s essential to stay informed about the top cybersecurity trends shaping the year ahead. This article will delve into the most critical trends you need to be aware of, providing insights into how to navigate the future of cybersecurity.
From the rise of artificial intelligence (AI) in cyberattacks to the growing importance of zero-trust security, the cybersecurity landscape is constantly evolving. The increasing reliance on cloud computing, the expansion of the Internet of Things (IoT), and the adoption of 5G networks are all creating new vulnerabilities that cybercriminals can exploit. Understanding these trends and adopting proactive measures is essential to safeguarding your organization or personal data in 2024 and beyond.
The Evolving Threat Landscape: Why Cybersecurity Trends Matter
The world of cybersecurity is in a constant state of flux, with new threats emerging and existing ones evolving at an alarming pace. This dynamic landscape means staying informed about the latest trends is not just a good idea – it’s a necessity.
Understanding emerging cybersecurity trends is crucial for several reasons. First, it allows organizations to proactively identify and address potential vulnerabilities before they are exploited. This is particularly important as threat actors constantly refine their tactics and target new vulnerabilities.
Secondly, staying ahead of the curve helps organizations develop more effective security strategies and implement appropriate safeguards. With rapid advancements in technology, traditional security measures may not be sufficient to protect against sophisticated cyberattacks.
Finally, understanding cybersecurity trends enables organizations to make informed decisions about technology investments. Investing in the right tools and solutions can make a significant difference in mitigating risk and protecting sensitive information.
By paying close attention to the ever-changing threat landscape, organizations can effectively protect their assets, minimize damage from cyberattacks, and maintain a strong security posture in the digital age.
Rise of Sophisticated AI-Powered Attacks

As artificial intelligence (AI) continues its rapid evolution, it’s reshaping the cybersecurity landscape in alarming ways. The rise of sophisticated AI-powered attacks poses a significant threat to businesses and individuals alike. These attacks leverage AI’s capabilities, such as machine learning and natural language processing, to circumvent traditional security measures and launch highly targeted, personalized, and automated attacks.
One concerning aspect is the ability of AI-powered malware to adapt and evolve in real-time, making it harder to detect and neutralize. AI algorithms can analyze vast amounts of data to identify vulnerabilities and tailor attacks accordingly. This adaptability makes it difficult for traditional security solutions, which rely on predefined patterns and signatures, to effectively counter these threats.
Furthermore, AI can be used to automate phishing attacks at scale. AI-powered bots can generate realistic-looking emails and messages, mimicking the communication style of legitimate organizations. These attacks are more convincing and difficult to distinguish from authentic communications, leading to a higher success rate in phishing attempts.
The use of AI in cybersecurity is a double-edged sword. While it offers opportunities to enhance security defenses, it also empowers attackers. Organizations must prioritize AI-driven security solutions to stay ahead of the curve. This includes adopting AI-powered threat intelligence platforms, implementing machine learning algorithms for anomaly detection, and training security professionals to understand and mitigate AI-powered attacks.
The Growing Threat of Quantum Computing on Encryption
Quantum computing, a rapidly advancing technology, poses a significant threat to current encryption methods. Unlike classical computers, which process information in bits (0s and 1s), quantum computers utilize qubits, which can exist in multiple states simultaneously. This unique capability allows quantum computers to break currently unbreakable encryption algorithms, particularly those based on public-key cryptography.
The most widely used public-key algorithms, such as RSA and ECC, rely on the difficulty of factoring large numbers or finding discrete logarithms. However, quantum computers equipped with Shor’s algorithm can efficiently solve these problems, rendering these encryption methods vulnerable.
The implications for cybersecurity are substantial. Sensitive information stored and transmitted using these algorithms, including financial data, medical records, and government secrets, could be compromised. As quantum computers advance, the window for exploiting these vulnerabilities is rapidly closing.
To mitigate this risk, the cybersecurity industry is actively exploring post-quantum cryptography (PQC). PQC algorithms are designed to be resistant to attacks from quantum computers. While still under development, PQC offers a promising solution to protect against the threat of quantum computing.
Organizations must proactively prepare for the quantum computing era. This includes:
- Assessing current encryption practices and identifying vulnerable systems
- Implementing PQC solutions where feasible
- Developing strategies to transition to quantum-resistant cryptography
The rise of quantum computing presents a significant challenge to traditional cybersecurity measures. By understanding the threat and adopting appropriate mitigation strategies, organizations can safeguard their data and systems in the face of this evolving technology.
Mobile Device Security: A Prime Target for Cybercriminals

In today’s interconnected world, our mobile devices have become extensions of ourselves. From banking and shopping to communication and entertainment, they hold a wealth of sensitive data, making them prime targets for cybercriminals. Mobile devices are increasingly becoming more vulnerable due to their constant connectivity and the evolving landscape of cyber threats.
Mobile malware is a growing concern, with sophisticated attacks targeting unsuspecting users. Phishing scams, disguised as legitimate messages, can trick users into revealing personal information. Data breaches, where sensitive information is stolen from unsecured devices, are becoming more frequent. These threats highlight the critical need for robust mobile device security measures.
The Internet of Things (IoT) and the Expanding Attack Surface
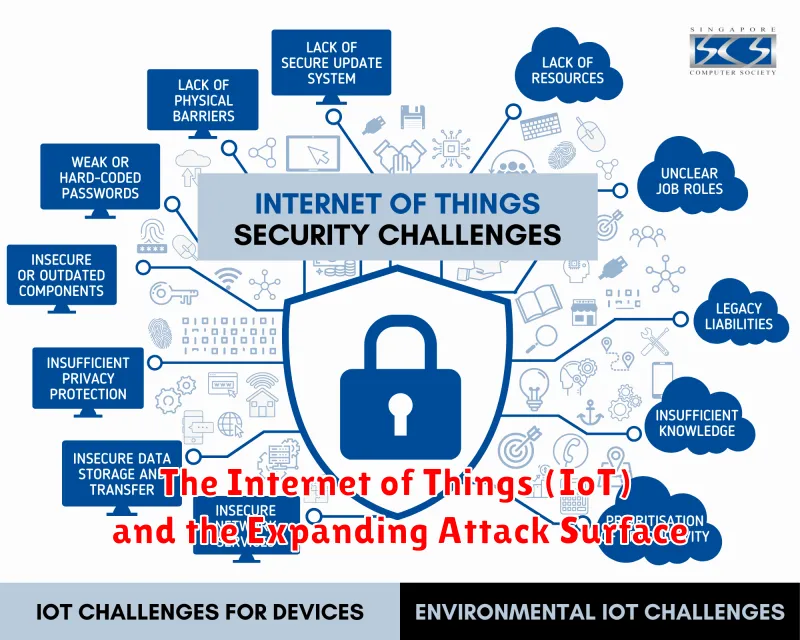
The Internet of Things (IoT) is a rapidly growing sector, with billions of devices connected to the internet. This interconnectedness brings numerous benefits but also presents significant security challenges. As more devices are connected, the attack surface expands, making it easier for malicious actors to gain access to sensitive data and disrupt operations.
The proliferation of IoT devices, particularly in critical infrastructure, healthcare, and industrial environments, increases the risk of cyberattacks. These attacks can range from data breaches to system disruptions, potentially leading to significant financial losses, reputational damage, and even physical harm.
One of the key vulnerabilities of IoT devices is their inherent lack of robust security features. Many devices are designed with minimal security considerations, making them susceptible to attacks like malware infection, denial-of-service attacks, and unauthorized access. The use of default passwords and weak encryption further exacerbates the issue.
To mitigate these risks, organizations must adopt a proactive approach to IoT security. This includes implementing strong authentication and access control mechanisms, regularly updating device firmware, and employing network segmentation to limit the impact of attacks. Furthermore, organizations should consider using security solutions specifically designed for IoT environments, such as intrusion detection and prevention systems (IDS/IPS) and threat intelligence platforms.
As the IoT ecosystem continues to grow, it is crucial to prioritize cybersecurity. By addressing the expanding attack surface and implementing robust security measures, organizations can protect their data, systems, and reputation from the growing threat posed by malicious actors.
Cloud Security Concerns: Navigating Shared Responsibility Models
As we venture deeper into the digital age, cloud computing has become an indispensable part of modern businesses. While the cloud offers numerous benefits, it also presents unique security challenges that necessitate a thorough understanding of shared responsibility models. This model dictates that both cloud providers and cloud users share the burden of securing data and applications within the cloud environment.
Cloud providers typically handle the security of the underlying infrastructure, including physical security of data centers, network security, and operating system patching. However, the responsibility for securing data, applications, and user access falls upon the cloud users. This often means implementing strong access controls, encryption protocols, and regular security audits.
Navigating this shared responsibility model can be tricky. Cloud users must be aware of their specific obligations and ensure they have the necessary expertise and resources to adequately secure their cloud deployments. One significant concern is the lack of visibility into cloud security practices. Many organizations struggle to monitor and manage their cloud security posture due to the complexities of multi-cloud environments and the dynamic nature of cloud services.
To address these challenges, organizations must adopt a comprehensive approach to cloud security, including:
- Strong security policies and procedures: Defining clear security policies and implementing robust security controls can help mitigate risks.
- Regular security assessments: Conducting periodic security assessments and penetration testing can identify vulnerabilities and ensure compliance.
- Effective security monitoring and incident response: Implementing robust monitoring and incident response plans can help detect and respond to security threats in a timely manner.
- Employee training and awareness: Ensuring that employees are trained on cloud security best practices is essential for preventing security breaches.
By understanding the shared responsibility model and taking proactive steps to secure their cloud deployments, organizations can reap the benefits of cloud computing while minimizing security risks.
Ransomware Attacks: Evolving Tactics and Increasing Stakes
Ransomware attacks continue to pose a significant threat to organizations of all sizes. Attackers are constantly evolving their tactics, making it more challenging for organizations to protect themselves. In 2024, we can expect to see even more sophisticated ransomware attacks with higher stakes.
One of the most concerning trends is the increasing use of double extortion. In this type of attack, attackers not only encrypt victims’ data but also steal it. They then threaten to publish the stolen data online unless the victim pays a ransom. This tactic significantly increases the pressure on victims to pay, as the potential reputational damage from a data breach can be devastating.
Another worrying trend is the rise of ransomware-as-a-service (RaaS). This model allows even less-skilled attackers to launch sophisticated ransomware attacks. RaaS platforms provide attackers with everything they need to carry out an attack, including malware, tools, and support. This makes it easier for attackers to target organizations and increases the number of attacks.
The stakes are also getting higher. Attackers are demanding larger ransoms, and they are more likely to target critical infrastructure, such as hospitals and power grids. This can have devastating consequences for both businesses and individuals.
To combat the evolving threat of ransomware, organizations need to take a proactive approach to cybersecurity. This includes implementing strong security measures, such as multi-factor authentication, data encryption, and regular backups. Organizations should also invest in security awareness training for employees to help them identify and avoid phishing attacks and other malicious activities.
Staying informed about the latest trends in ransomware and taking the necessary steps to protect your organization is essential. By understanding the evolving tactics and increasing stakes, you can better prepare your organization to withstand these increasingly sophisticated cyberattacks.
The Importance of Cybersecurity Awareness Training for Employees
In today’s increasingly digital landscape, cybersecurity is paramount. It’s not just the responsibility of IT departments; it’s a collective effort that requires every employee to be vigilant. This is where cybersecurity awareness training comes into play. It’s the cornerstone of a robust cybersecurity strategy, empowering employees to recognize and mitigate potential threats.
Why is it so crucial? Consider this: employees are often the weakest link in the cybersecurity chain. A single click on a malicious link or the disclosure of sensitive information can have devastating consequences. Cybersecurity awareness training equips employees with the knowledge and skills to:
- Recognize phishing attacks and other social engineering attempts.
- Understand the importance of strong passwords and multi-factor authentication.
- Be cautious about sharing information online, especially on social media.
- Report suspicious activity promptly.
The benefits of such training are far-reaching. It not only strengthens the organization’s overall cybersecurity posture but also fosters a culture of responsibility and accountability. This can lead to:
- Reduced risk of data breaches and other cyberattacks.
- Improved employee confidence in their ability to protect company data.
- Enhanced compliance with industry regulations and data privacy laws.
In a world where cyber threats are constantly evolving, cybersecurity awareness training is an essential investment. It empowers employees to be proactive participants in the fight against cybercrime, ultimately safeguarding the organization’s assets, reputation, and future.
Zero Trust Security: A Proactive Approach to Data Protection
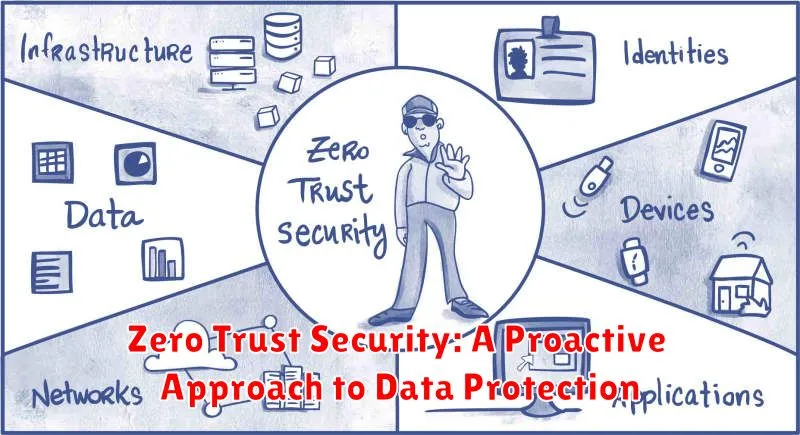
In the ever-evolving landscape of cybersecurity, the traditional perimeter-based security models are becoming increasingly inadequate. This is where Zero Trust security emerges as a revolutionary approach, fundamentally shifting the paradigm towards a more proactive and robust defense mechanism. At its core, Zero Trust operates on the principle of “never trust, always verify,” eliminating implicit trust and demanding rigorous authentication and authorization at every access point.
The Zero Trust framework assumes that any user or device, whether inside or outside the organization’s network, poses a potential threat until explicitly verified. This means that every request for access to data or resources is meticulously scrutinized, regardless of the source. By eliminating blind trust, Zero Trust effectively mitigates the risk of breaches stemming from compromised internal users, malicious insiders, or external attackers.
One of the key pillars of Zero Trust is the implementation of multi-factor authentication (MFA). This process requires users to provide multiple forms of identification before granting access, significantly enhancing security by making it considerably harder for unauthorized individuals to gain entry. Another crucial element is least privilege access control, which ensures that users only have access to the specific data and resources they need to perform their job functions, minimizing the potential damage caused by a compromised account.
Furthermore, Zero Trust leverages continuous monitoring and analytics to detect and respond to suspicious activities in real time. By analyzing user behavior, network traffic, and system logs, organizations can identify potential threats and take immediate action to contain them. This proactive approach significantly reduces the impact of security incidents, as breaches are detected and mitigated before they can cause substantial damage.
In conclusion, Zero Trust security is not merely a trend but a critical shift in cybersecurity strategy. By embracing this proactive approach, organizations can significantly bolster their defenses against evolving threats and protect their valuable data assets. With its emphasis on continuous verification, least privilege access, and real-time threat detection, Zero Trust empowers organizations to navigate the complex cybersecurity landscape with greater confidence and resilience.
The Rise of Cybersecurity Mesh: Decentralized Security for Distributed Networks
As organizations continue to adopt hybrid and multi-cloud strategies, their IT infrastructure becomes increasingly complex and distributed. This presents a significant challenge for traditional, centralized security models. Enter cybersecurity mesh, a revolutionary approach that embraces decentralization to protect distributed networks effectively.
The core concept of cybersecurity mesh is to distribute security controls across the entire network, from the edge to the cloud. Instead of relying on a single, centralized security platform, organizations deploy smaller, independent security agents or “micro-segments” that operate autonomously. These micro-segments communicate and collaborate with each other, forming a cohesive security fabric that adapts to the dynamic nature of modern networks.
This distributed approach offers several advantages. It enhances agility and flexibility, allowing organizations to respond quickly to emerging threats and changing security landscapes. Cybersecurity mesh also improves resilience by eliminating single points of failure. If one security agent is compromised, the rest of the network remains protected. Additionally, it facilitates a zero-trust security model, which verifies every user and device before granting access, further strengthening security posture.
The rise of cybersecurity mesh is driven by several factors, including the growing adoption of cloud computing, the increasing complexity of IT infrastructure, and the evolving threat landscape. As organizations continue to embrace distributed architectures, cybersecurity mesh will become increasingly critical for securing their networks and data.
Cybersecurity Insurance: Mitigating Financial Risks in the Digital Age
In the contemporary digital landscape, where cyber threats are becoming increasingly sophisticated, businesses face unprecedented financial risks. Data breaches, ransomware attacks, and other cyber incidents can inflict significant financial damage, crippling operations and eroding trust. To navigate this evolving threat landscape, cybersecurity insurance has emerged as an indispensable tool for mitigating financial risks.
Cybersecurity insurance provides crucial protection against the financial fallout from cyberattacks. It covers a wide range of expenses, including:
- Data breach response costs: This includes forensic investigations, legal fees, and notification expenses.
- Business interruption costs: This covers lost revenue and expenses incurred while recovering from a cyberattack.
- Ransomware payments: Some policies offer coverage for ransom payments, but this is typically subject to strict conditions.
- Cybercrime liability: This protects businesses from claims arising from data breaches and other cyber incidents.
Furthermore, cybersecurity insurance encourages proactive risk management. By requiring businesses to implement robust cybersecurity measures, insurance providers incentivize organizations to prioritize data protection. This creates a positive feedback loop, enhancing overall cybersecurity posture and reducing the likelihood of attacks.
While cybersecurity insurance offers valuable financial protection, it is important to recognize that it is not a substitute for comprehensive cybersecurity practices. Organizations must prioritize proactive measures such as:
- Regular security assessments and vulnerability scanning
- Employee cybersecurity training
- Multi-factor authentication implementation
- Data encryption and backup strategies
By combining robust cybersecurity measures with the financial protection of insurance, businesses can effectively mitigate financial risks in the digital age. As the threat landscape continues to evolve, cybersecurity insurance is poised to play an even more critical role in safeguarding businesses and ensuring their financial resilience.
Government Regulations and Compliance: GDPR, CCPA, and Beyond
The landscape of data privacy regulations is constantly evolving, with new laws emerging and existing ones being strengthened. In 2024, organizations must navigate a complex web of compliance requirements, with GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) remaining key pillars. Beyond these established regulations, other noteworthy trends are emerging, presenting new challenges and opportunities.
Expansion of Privacy Laws: Beyond the EU and California, more jurisdictions are enacting comprehensive data privacy laws. For example, the Virginia Consumer Data Protection Act (VCDPA) and the Colorado Privacy Act (CPA) are just the tip of the iceberg. This trend signifies a global shift towards stronger data protection measures. Organizations operating in multiple regions must ensure they are compliant with a patchwork of regulations, leading to significant complexities.
Focus on AI and Data Minimization: With the rise of artificial intelligence (AI), new regulations are emerging to address the ethical and privacy concerns associated with data use in AI systems. Regulations are likely to focus on data minimization, requiring organizations to collect and retain only essential data for their purposes. This will necessitate careful consideration of data collection practices and the development of robust AI governance frameworks.
Increased Enforcement and Fines: Data protection authorities worldwide are becoming increasingly proactive in enforcing privacy regulations. Significant fines are being levied on organizations that fail to comply, highlighting the serious consequences of non-compliance. Businesses must prioritize robust data security and compliance programs to minimize their risk of fines and reputational damage.
The Importance of Transparency and Control: Consumers are demanding more transparency and control over their data. Regulations are evolving to give individuals greater access to their personal information and the right to request its deletion. Businesses must proactively implement mechanisms that allow users to understand how their data is used and provide them with meaningful choices about its processing.
Adapting to the Changing Landscape: Navigating the evolving landscape of data privacy regulations requires a proactive approach. Organizations need to stay informed about emerging legislation, assess their current practices against the latest requirements, and invest in the necessary infrastructure and personnel to ensure ongoing compliance. A strong understanding of data privacy principles and a commitment to transparency are essential for building trust with customers and navigating the complex regulatory environment of the future.