In the ever-evolving digital landscape, safeguarding your data and systems from cyber threats is more critical than ever. As technology advances and cybercriminals become more sophisticated, staying ahead of the curve with robust cybersecurity practices is paramount. This Ultimate Guide to Cybersecurity Best Practices for 2024 equips you with the essential knowledge and strategies to protect your organization or personal data from the latest threats.
From implementing multi-factor authentication and strong passwords to embracing cloud security and data encryption, this guide delves into a comprehensive range of cybersecurity best practices. We’ll explore the latest attack vectors, mitigation techniques, and essential tools to navigate the digital world with confidence. Whether you’re a business owner, IT professional, or simply concerned about your online privacy, this guide provides actionable steps to bolster your cybersecurity posture and ensure a safe and secure digital experience in 2024 and beyond.
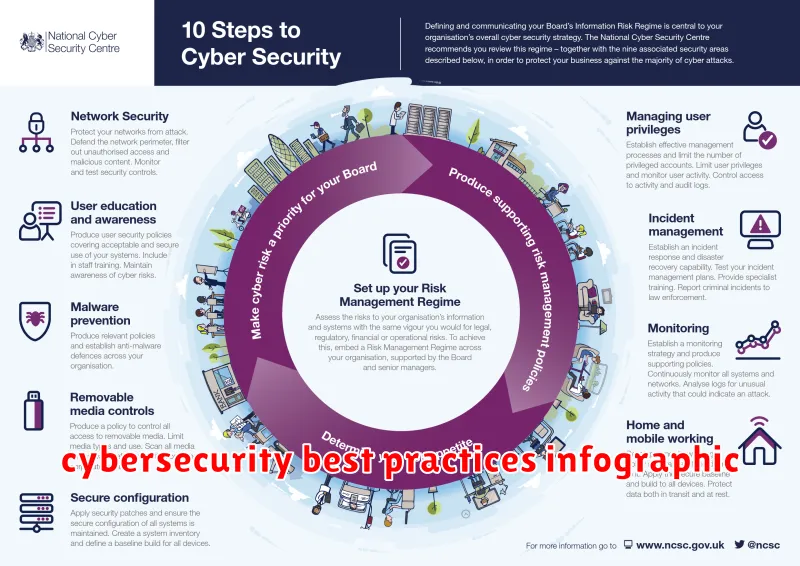
Understanding the Importance of Cybersecurity Best Practices
In today’s digitally driven world, where data is the new currency, protecting sensitive information has become paramount. Cybersecurity best practices are not just a suggestion; they are a necessity. They provide a robust defense against the ever-evolving threat landscape, safeguarding your personal data, business operations, and financial stability.
Failing to prioritize cybersecurity can lead to devastating consequences. Data breaches, financial losses, reputational damage, and even legal repercussions are just some of the risks you face when neglecting proper security measures. The impact of such incidents can be long-lasting, impacting your business and personal life for years to come.
Implementing robust cybersecurity practices is an investment in your future. It ensures that your sensitive information is secure, builds trust with your customers and partners, and helps maintain your organization’s reputation. Moreover, it empowers you to operate with confidence, knowing that your data is protected from unauthorized access and malicious threats.
In the following sections, we’ll delve deeper into the importance of specific cybersecurity best practices, outlining practical steps you can take to enhance your online security. Stay tuned for a comprehensive guide that will equip you with the knowledge and tools to navigate the digital world safely and confidently.
Implementing Strong Passwords and Multi-Factor Authentication
In today’s digital landscape, securing your data is paramount. Implementing strong passwords and multi-factor authentication (MFA) are fundamental steps towards safeguarding your online presence.
Strong passwords are the first line of defense. They should be at least 12 characters long, include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using common words or personal information. Consider using a password manager to generate and store strong passwords securely.
Multi-factor authentication adds an extra layer of security by requiring more than just a password to access accounts. It typically involves a second factor, such as a one-time code sent to your phone or email, or a biometric scan. By using MFA, you make it significantly harder for unauthorized individuals to gain access to your accounts, even if they have your password.
Here are some practical tips for implementing strong passwords and MFA:
- Enable MFA wherever possible. Most online services now offer this feature.
- Use different passwords for different accounts. This minimizes the risk of compromised accounts impacting others.
- Avoid using the same password for personal and work accounts.
- Regularly review and update your passwords.
- Be cautious of phishing attempts. Never provide your password or personal information through suspicious links or emails.
By adopting these best practices, you can significantly enhance your online security and protect your valuable data from unauthorized access.
Recognizing and Responding to Phishing Attacks
Phishing attacks are a common cybersecurity threat that can have serious consequences for individuals and organizations. Phishing attacks involve tricking users into giving up sensitive information, such as passwords, credit card numbers, or personal data, by disguising themselves as legitimate sources. They often use deceptive emails, websites, or text messages to lure victims into clicking on malicious links or downloading harmful files.
To effectively recognize and respond to phishing attacks, it is crucial to understand the common tactics used by attackers. Some red flags to watch out for include:
- Suspicious email addresses: Check the sender’s email address carefully, as it may be misspelled or have an unusual domain name.
- Urgent requests for action: Phishing emails often create a sense of urgency, urging you to click on a link or provide information immediately.
- Generic greetings and salutations: Legitimate emails typically use your name or a specific title. Phishing emails often use generic greetings like “Dear User” or “Dear Customer.”
- Grammar and spelling errors: Phishing emails often contain grammatical errors or poor spelling, indicating that they are not from a legitimate source.
- Suspicious links: Hover your mouse over any links before clicking to see the actual URL, as it may redirect you to a malicious website.
- Attachments from unknown senders: Avoid opening attachments from unknown senders, as they may contain malware.
If you suspect you have received a phishing email, do not click on any links or open any attachments. Instead, report the email to your IT department or the appropriate authorities. You should also change your passwords for any accounts that may have been compromised.
In addition to recognizing phishing attacks, it is equally important to adopt proactive measures to protect yourself. These include:
- Use strong passwords: Create unique and complex passwords for all your online accounts. Avoid using the same password for multiple accounts.
- Enable two-factor authentication: This adds an extra layer of security by requiring you to enter a code sent to your phone in addition to your password.
- Be cautious about clicking on links: Only click on links from trusted sources. Avoid clicking on links in emails or text messages from unknown senders.
- Keep your software up to date: Regularly update your operating system and applications to patch vulnerabilities that could be exploited by attackers.
- Be aware of social engineering: Phishing attacks often rely on social engineering tactics to manipulate victims into giving up information. Be cautious about providing personal information to unsolicited requests.
By understanding the common phishing tactics and implementing effective prevention measures, you can significantly reduce your risk of falling victim to these attacks.
Keeping Software and Systems Up-to-Date
In the ever-evolving landscape of cybersecurity, staying ahead of the curve is paramount. One of the most crucial aspects of safeguarding your digital assets is ensuring that your software and systems are consistently up-to-date. This practice is often referred to as patch management and plays a vital role in mitigating vulnerabilities that attackers exploit.
Regular updates deliver essential security patches that address known vulnerabilities, such as bugs and flaws, that cybercriminals often target. By installing these patches promptly, you effectively plug security loopholes and prevent malicious actors from gaining unauthorized access to your systems.
Beyond security, keeping software and systems up-to-date also brings numerous other benefits. Updates often introduce new features, enhance performance, and improve compatibility with newer technologies. Staying current allows your organization to leverage the latest innovations and optimize your operational efficiency.
To ensure effective patch management, it’s essential to establish a comprehensive strategy. This includes:
- Implementing a centralized patch management system: This system should automate the process of identifying, downloading, and deploying patches across your network.
- Scheduling regular update cycles: Implement a consistent schedule for applying updates to minimize downtime and ensure continuous security.
- Prioritizing critical patches: Focus on installing patches that address high-severity vulnerabilities first.
- Testing updates before deployment: Conduct thorough testing in a controlled environment to prevent unintended consequences.
- Maintaining detailed records: Keep meticulous records of all updates applied, including dates, versions, and any encountered issues.
In today’s digital world, staying vigilant about software and system updates is non-negotiable. By embracing a proactive approach to patch management, you equip your organization with a robust defense against evolving cyber threats and ensure a secure digital environment.
Securing Your Network with Firewalls and Intrusion Detection Systems
In today’s digital landscape, cybersecurity is paramount. Firewalls and Intrusion Detection Systems (IDS) are essential tools in protecting your network from malicious threats.
Firewalls act as a barrier between your network and the outside world, filtering incoming and outgoing traffic based on predefined rules. They block unauthorized access, preventing hackers from infiltrating your system.
Intrusion Detection Systems (IDS) go a step further. They monitor network traffic for suspicious activity, identifying potential attacks in real-time. They don’t block traffic directly but alert administrators to potential threats, allowing for timely intervention.
Here’s how these technologies work together to enhance your network security:
- Firewalls provide the first line of defense, acting as a gatekeeper to your network.
- IDS constantly monitor for suspicious activity within the network, even after traffic has passed through the firewall.
By combining these tools, you create a robust security system capable of detecting and preventing a wide range of cyber threats.
Remember, a layered approach to security is crucial. Firewalls and IDS are essential components of a comprehensive cybersecurity strategy.
Protecting Sensitive Data with Encryption
In the ever-evolving landscape of cybersecurity, safeguarding sensitive data has become paramount. Encryption serves as a robust shield, transforming data into an unreadable format, rendering it inaccessible to unauthorized individuals. This article delves into the crucial role of encryption in securing sensitive data, providing a comprehensive guide to best practices for 2024.
Encryption is the process of converting data into an unreadable format, known as ciphertext, using an algorithm and a secret key. Only individuals possessing the corresponding decryption key can access the original data, effectively preventing unauthorized access and data breaches.
Types of Encryption:
- Symmetric Encryption: Uses the same key for both encryption and decryption. This approach is faster but requires secure key management.
- Asymmetric Encryption: Uses separate keys for encryption and decryption, providing improved security for key management.
Best Practices for Encryption in 2024:
- Utilize Strong Encryption Algorithms: Opt for robust encryption algorithms like AES-256 or RSA-4096.
- Implement End-to-End Encryption: Secure data transmission and storage by encrypting data at its origin and decrypting it only at its destination.
- Adopt Multi-Factor Authentication (MFA): Enhance security by requiring multiple verification factors for user authentication, mitigating the risk of unauthorized access.
- Regularly Update Encryption Keys: Periodically update encryption keys to minimize the impact of potential key compromise.
- Employ Secure Key Management Practices: Store encryption keys in secure locations and use robust key management solutions to prevent unauthorized access or manipulation.
Benefits of Data Encryption:
- Confidentiality: Protects sensitive data from unauthorized access and disclosure.
- Integrity: Ensures the authenticity and completeness of data, preventing unauthorized modifications or tampering.
- Compliance: Adheres to regulatory requirements and industry standards for data protection.
- Risk Mitigation: Reduces the risk of data breaches and financial losses.
In conclusion, encryption is an indispensable tool for safeguarding sensitive data in today’s digital landscape. By adopting robust encryption practices and adhering to best practices for 2024, organizations can effectively protect their valuable assets and mitigate cybersecurity risks. It is essential to prioritize encryption as a fundamental security measure to ensure data confidentiality, integrity, and compliance.
Educating Employees on Cybersecurity Awareness
In today’s digital world, where businesses rely heavily on technology, cybersecurity awareness is crucial. Educating employees on cybersecurity best practices is essential to protect your organization from cyber threats. Employees are often the weakest link in the cybersecurity chain, as they can inadvertently open doors to malicious actors. By equipping your workforce with the knowledge and skills necessary to identify and mitigate risks, you can significantly reduce your company’s vulnerability.
Effective cybersecurity awareness training should cover a range of topics, including:
- Recognizing and reporting phishing scams
- Understanding the importance of strong passwords and multi-factor authentication
- Safeguarding sensitive data
- Being cautious about suspicious emails and attachments
- Understanding the consequences of cybersecurity breaches
Training methods can include online modules, interactive workshops, and regular communication through email or company intranet. The key is to make the training engaging and relevant to employees’ daily tasks. Regular refreshers and simulations can help reinforce good practices and keep employees vigilant.
A comprehensive cybersecurity awareness program is an ongoing process. It requires continuous evaluation and adaptation to address evolving threats. By prioritizing employee education and empowering them to become proactive cybersecurity advocates, you can significantly strengthen your organization’s security posture.
Creating a Comprehensive Incident Response Plan
In today’s digital landscape, cybersecurity threats are more sophisticated and prevalent than ever. A robust incident response plan is crucial for mitigating the impact of security breaches and ensuring business continuity. This plan should outline a clear and well-defined process for responding to incidents, from initial detection to recovery.
The first step in creating a comprehensive incident response plan is to identify and prioritize potential threats. This involves assessing the organization’s assets, vulnerabilities, and potential attack vectors. Once threats are identified, you can develop specific strategies for mitigating their impact.
The plan should also outline a clear chain of command for responding to incidents. This includes defining roles and responsibilities, establishing communication channels, and designating a dedicated incident response team. This team should be trained to handle incidents effectively and have access to the necessary resources.
Another crucial element is a well-defined incident response process. This process should include steps for:
- Detection: Identifying and confirming the occurrence of an incident.
- Analysis: Investigating the incident to determine its scope and impact.
- Containment: Limiting the spread of the incident and preventing further damage.
- Eradication: Removing the threat from the system.
- Recovery: Restoring affected systems and data to their original state.
- Lessons Learned: Analyzing the incident to identify areas for improvement and updating the plan accordingly.
Regularly testing and updating the incident response plan is essential for ensuring its effectiveness. Conduct tabletop exercises and simulations to evaluate the plan’s effectiveness and identify areas for improvement. As the threat landscape evolves, your incident response plan should adapt to address new and emerging threats.
By creating a comprehensive incident response plan, organizations can significantly reduce the impact of security breaches and enhance their resilience against cyberattacks. A well-defined plan provides a framework for responding effectively, minimizing downtime, and safeguarding critical data.
Regularly Backing Up Critical Data
Regularly backing up critical data is an essential component of a robust cybersecurity strategy. It acts as a safety net, safeguarding your valuable information against various threats, including hardware failures, software malfunctions, cyberattacks, and human errors. By creating copies of your data and storing them in a secure location, you ensure that even if your primary data sources become compromised, you can recover your information quickly and efficiently.
To ensure your backups are effective, consider the following key points:
- Data Identification: Define the critical data that needs to be backed up, prioritizing information essential for your business operations.
- Backup Frequency: Determine the frequency of backups based on the rate of data changes and the importance of the data. Frequent backups are crucial for dynamic data, while less frequent backups may suffice for static data.
- Backup Strategy: Implement a comprehensive backup strategy that includes both full backups (copying all data) and incremental backups (copying only changes since the last full backup). This approach optimizes backup time and storage space.
- Backup Location: Choose a secure, off-site location for storing backups. This could include a cloud storage service, a separate physical location, or a combination of both.
- Backup Testing: Regularly test your backup process to ensure it functions as intended. This involves restoring data from backups to verify their integrity and recoverability.
By consistently implementing these best practices, you can establish a reliable and secure backup system that mitigates the risks associated with data loss and ensures business continuity in the face of unforeseen events.
Conducting Security Audits and Penetration Testing
Security audits and penetration testing are crucial components of a comprehensive cybersecurity strategy. They help identify vulnerabilities and weaknesses in your systems and applications, allowing you to proactively mitigate risks before they can be exploited by attackers.
Security Audits
A security audit is a systematic examination of your organization’s security controls, policies, and procedures. It involves assessing the effectiveness of your existing security measures and identifying potential areas for improvement. Audits can be conducted internally by your security team or externally by a third-party security firm.
Penetration Testing
Penetration testing, also known as “pen testing,” simulates a real-world attack on your systems and applications. This involves using the same techniques and tools that malicious actors might use to identify and exploit vulnerabilities. Penetration testing can help you understand the real-world impact of vulnerabilities and assess the effectiveness of your security defenses.
Types of Penetration Testing
There are several types of penetration testing, including:
- Black box testing: The tester has no prior knowledge of the target system.
- White box testing: The tester has access to source code and internal documentation.
- Gray box testing: The tester has limited knowledge of the target system.
Benefits of Security Audits and Penetration Testing
Conducting security audits and penetration testing offers numerous benefits, including:
- Improved security posture: Identify and mitigate vulnerabilities before they can be exploited.
- Reduced risk: Proactively address security risks and minimize the likelihood of breaches.
- Compliance: Meet industry regulations and compliance requirements.
- Enhanced reputation: Demonstrate a commitment to security and build trust with customers and stakeholders.
Best Practices for Conducting Security Audits and Penetration Testing
To maximize the effectiveness of your security audits and penetration testing efforts, consider these best practices:
- Define clear objectives: Establish specific goals and scope for your audit or pen test.
- Choose the right methodology: Select the appropriate type of testing based on your organization’s needs and risk profile.
- Engage experienced professionals: Partner with reputable security experts who have the necessary skills and experience.
- Document findings and recommendations: Create a detailed report outlining vulnerabilities, risks, and remediation steps.
- Implement remediation plans: Take prompt action to address identified vulnerabilities.
- Conduct regular testing: Schedule periodic audits and penetration tests to ensure ongoing security effectiveness.
Security audits and penetration testing are essential elements of a robust cybersecurity program. By proactively identifying and mitigating vulnerabilities, you can significantly reduce your organization’s risk of cyberattacks and protect your sensitive data.
Staying Informed About Emerging Threats
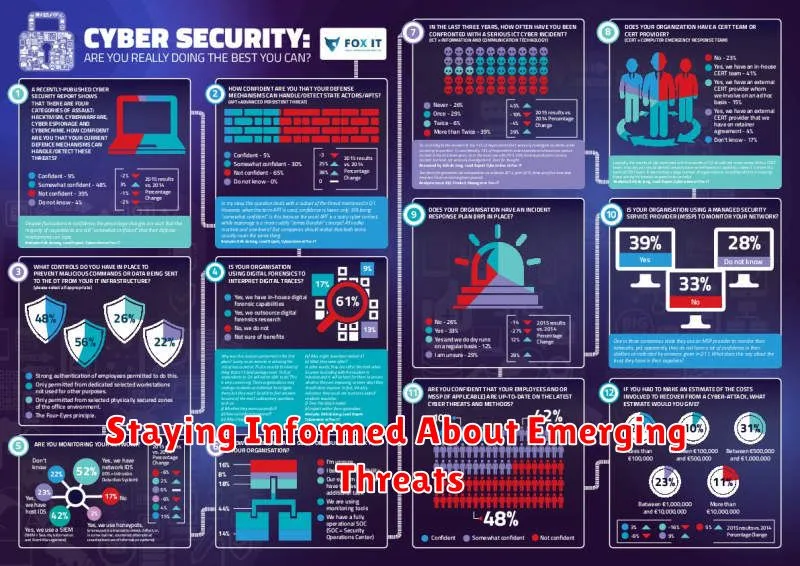
Staying ahead of the curve when it comes to cybersecurity threats is crucial. The threat landscape is constantly evolving, with new vulnerabilities and attack methods emerging all the time. To effectively protect your organization, you need to be aware of the latest threats and how to mitigate them. This involves actively seeking out information from trusted sources and staying informed about current trends and emerging technologies.
One of the best ways to stay informed is to follow reputable cybersecurity blogs, news websites, and research organizations. These sources provide valuable insights into the latest threats, vulnerabilities, and attack techniques. They often publish reports, analysis, and expert opinions on emerging cybersecurity trends. In addition, consider subscribing to industry newsletters and attending cybersecurity conferences and webinars to stay up-to-date on the latest threats and best practices.
By staying informed about emerging threats, you can proactively identify and address potential vulnerabilities within your organization. This allows you to implement the appropriate security measures and keep your data safe. Remember, continuous learning and adaptation are key to maintaining effective cybersecurity.
Leveraging Security Information and Event Management (SIEM) Tools
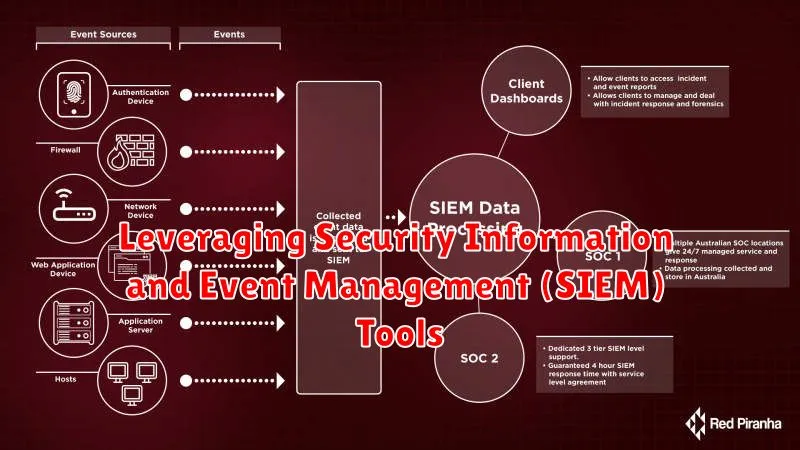
In today’s digital landscape, safeguarding your organization’s data and systems is paramount. Security Information and Event Management (SIEM) tools play a crucial role in achieving this goal. These powerful platforms aggregate and analyze security data from various sources, providing a comprehensive view of your security posture and enabling proactive threat detection and response.
Here’s how SIEM tools can be leveraged to enhance your cybersecurity in 2024:
- Real-time threat detection: SIEMs analyze security logs and events in real-time, identifying suspicious activities and potential breaches. This allows for immediate action to mitigate threats before significant damage occurs.
- Incident response automation: By automating incident response processes, SIEMs streamline the investigation and remediation phases, reducing the time it takes to contain and resolve security incidents.
- Security analytics and reporting: SIEMs provide valuable insights into security trends, identifying patterns and vulnerabilities. This data can be used to improve security policies, strengthen defenses, and proactively address emerging threats.
- Compliance and audit support: SIEM tools help organizations meet regulatory compliance requirements by providing auditable logs and reporting capabilities, demonstrating adherence to industry standards.
- Centralized security management: SIEMs offer a single console to manage security events, simplifying security operations and improving visibility across your entire IT infrastructure.
Choosing the right SIEM tool is crucial. Consider factors like your organization’s size, security needs, budget, and technical expertise. Implementing a SIEM effectively requires skilled personnel and ongoing maintenance to ensure optimal performance and threat detection capabilities.
By leveraging SIEM tools effectively, organizations can significantly enhance their cybersecurity posture, protect sensitive data, and mitigate the risks of cyberattacks in the ever-evolving digital landscape.
Implementing Zero Trust Security Model
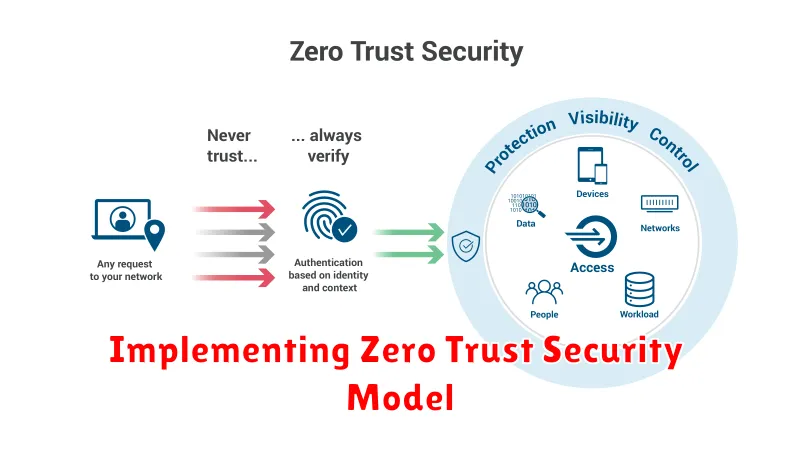
In today’s increasingly complex and interconnected digital landscape, traditional security perimeters are becoming less effective. Organizations are embracing a new security paradigm known as Zero Trust, which fundamentally shifts the way security is approached.
The Zero Trust model assumes that no user, device, or application can be trusted by default. Every request for access to resources, regardless of its origin, must be verified and authorized explicitly. This approach eliminates the implicit trust inherent in traditional security models, significantly strengthening an organization’s security posture.
Key Principles of Zero Trust
The Zero Trust model is based on several key principles, including:
- Least Privilege: Users and applications are granted only the minimum access required to perform their tasks.
- Explicit Verification: Every request for access is verified and authenticated before granting access.
- Continuous Monitoring: Ongoing monitoring and analysis of user behavior and system activity are essential for detecting and responding to threats.
- Micro-Segmentation: Networks and resources are segmented to limit the impact of breaches and prevent lateral movement.
Implementing Zero Trust
Implementing a Zero Trust model involves a multi-faceted approach that encompasses:
- Identity and Access Management (IAM): Establish a robust IAM system to control access to resources based on user identities and roles.
- Network Segmentation: Segment networks and applications to isolate sensitive resources and prevent lateral movement.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization.
- Endpoint Security: Secure all endpoints (devices, laptops, etc.) with endpoint detection and response (EDR) solutions.
- Security Awareness Training: Educate employees about Zero Trust principles and best practices to minimize the risk of phishing attacks and social engineering.
Benefits of Zero Trust
Adopting a Zero Trust security model offers numerous benefits, including:
- Enhanced Security: Reduces the attack surface and mitigates the risk of breaches.
- Improved Compliance: Helps organizations meet regulatory requirements and industry standards.
- Increased Agility: Enables rapid adaptation to evolving threats and security landscape.
- Reduced Costs: Minimizes downtime and recovery costs associated with security incidents.
Conclusion
Implementing a Zero Trust security model is crucial for organizations of all sizes in today’s threat-filled environment. By embracing the principles of Zero Trust, organizations can significantly enhance their security posture and protect their valuable assets from cyberattacks.
Understanding and Complying with Relevant Regulations

Navigating the complex landscape of cybersecurity regulations can seem daunting. However, understanding and adhering to these regulations is crucial for protecting your organization and its data. They provide a framework for implementing robust security measures and minimizing risk. To ensure compliance, it’s essential to identify the specific regulations applicable to your industry and geographic location. Some key regulations include:
- General Data Protection Regulation (GDPR): This European Union law focuses on protecting the personal data of individuals within the EU.
- California Consumer Privacy Act (CCPA): This California law grants consumers more control over their personal information.
- Payment Card Industry Data Security Standard (PCI DSS): This standard mandates security measures for organizations that handle credit card information.
- Health Insurance Portability and Accountability Act (HIPAA): This US law protects the privacy and security of sensitive health information.
Compliance requires more than just awareness. You need to implement specific controls, train employees, conduct regular audits, and maintain documentation. Failure to comply with regulations can lead to significant penalties, reputational damage, and legal liabilities. It’s therefore essential to invest in robust cybersecurity practices that align with these regulations to safeguard your organization and its data in 2024.
Best Practices for Mobile Device Security

In today’s digital age, mobile devices have become indispensable for both personal and professional lives. However, this increased reliance on smartphones and tablets also creates a wider attack surface for cybercriminals. Therefore, it is crucial to adopt robust security measures to protect your mobile devices from threats.
1. Use Strong Passwords and Biometric Authentication
Employing strong passwords and enabling biometric authentication like fingerprint or facial recognition significantly enhances security. Avoid using simple or easily guessable passwords, and consider using a password manager to generate and store complex passwords securely.
2. Keep Your Operating System and Apps Updated
Regularly update your operating system and applications to benefit from the latest security patches and bug fixes. These updates often address vulnerabilities that cybercriminals exploit to gain unauthorized access to your device.
3. Be Cautious with Public Wi-Fi
Public Wi-Fi networks are notorious for being insecure. When using public Wi-Fi, avoid accessing sensitive information, such as banking or personal accounts. Consider using a Virtual Private Network (VPN) to encrypt your internet traffic and enhance privacy.
4. Enable Device Encryption
Device encryption encrypts all data stored on your mobile device, making it inaccessible to unauthorized individuals if your device is lost or stolen. Enable encryption on your device to add an extra layer of protection.
5. Install a Mobile Security App
Consider installing a reputable mobile security app that provides features such as anti-malware protection, anti-theft measures, and data encryption. These apps can help detect and block malicious software and prevent data loss.
6. Be Wary of Phishing Attacks
Phishing attacks are a common tactic used by cybercriminals to steal personal information. Be cautious about clicking on suspicious links or opening attachments from unknown senders, especially if they claim to be from legitimate institutions or organizations.
7. Limit App Permissions
Review the app permissions requested during installation and grant only essential permissions. Avoid granting unnecessary permissions to apps, as this can expose sensitive data to potential threats.
8. Regularly Back Up Your Data
Regularly back up your data to a secure location, such as a cloud storage service, to prevent data loss if your device is lost, damaged, or compromised. Ensure the backup location is secure and protected with strong authentication.
By adhering to these best practices, you can significantly reduce the risk of mobile device security breaches and protect your sensitive data from cyber threats.