In today’s digital age, the landscape of cyber threats is constantly evolving, becoming increasingly sophisticated and dangerous. Organizations of all sizes are facing a growing number of attacks, from ransomware and phishing scams to data breaches and DDoS attacks. With the ever-increasing volume and complexity of cyber threats, it’s more important than ever for organizations to have a robust and comprehensive cyber threat detection strategy in place.
A strong cyber threat detection strategy is essential for staying ahead of the curve and protecting your organization from costly cyberattacks. By implementing the right tools and techniques, you can identify potential threats early on, reduce the risk of a successful attack, and minimize the impact of any incidents that do occur. This article will delve into the most effective cyber threat detection strategies, providing insights on how to proactively safeguard your organization in this rapidly evolving digital landscape.
Understanding the Evolving Landscape of Cyber Threats
The landscape of cyber threats is constantly evolving, becoming more sophisticated and complex every day. Attackers are continuously innovating their methods, utilizing new technologies and exploiting vulnerabilities to compromise systems and steal sensitive information. Understanding this dynamic threat landscape is crucial for organizations to implement effective security measures and stay ahead of the curve.
One of the most significant shifts in the cyber threat landscape is the rise of advanced persistent threats (APTs). These are highly organized and well-funded groups that often target specific organizations or individuals with long-term, stealthy attacks. APTs employ advanced techniques like zero-day exploits and social engineering to gain access to systems and maintain persistent presence for extended periods, often undetected.
Another key development is the increasing use of artificial intelligence (AI) and machine learning (ML) by attackers. AI-powered malware can adapt to security measures, evade detection, and target vulnerabilities more effectively. Additionally, attackers are using AI for automating phishing campaigns and crafting more convincing social engineering attacks.
The rise of ransomware is another concerning trend. Attackers use ransomware to encrypt victims’ data and demand payment for its release. This threat has become increasingly prevalent and devastating, impacting individuals and organizations alike. The use of cryptocurrency has made it easier for ransomware operators to collect payments anonymously and make their attacks harder to trace.
Furthermore, the proliferation of Internet of Things (IoT) devices has introduced new attack vectors. These devices often lack robust security measures and can be easily compromised, becoming entry points for attackers to access networks and sensitive data. The increasing reliance on cloud services also presents new challenges, as attackers target cloud infrastructure and data breaches.
Key Elements of a Robust Cyber Threat Detection System
In the ever-evolving landscape of cyber threats, staying ahead of the curve requires a comprehensive and robust threat detection system. A robust system encompasses a multifaceted approach, encompassing several key elements that work together to identify and mitigate potential risks. These elements are essential for organizations of all sizes to ensure the security and integrity of their data and systems.
1. Network Security Monitoring (NSM): This element involves constantly monitoring network traffic for suspicious activities and anomalies. Advanced NSM solutions utilize sophisticated analytics and machine learning algorithms to detect patterns and deviations from normal behavior. Real-time insights are crucial for identifying potential threats and responding promptly.
2. Endpoint Detection and Response (EDR): EDR solutions focus on monitoring individual devices, including workstations, servers, and mobile devices. They provide visibility into user actions, file access, and system behavior, allowing for the detection of malware, unauthorized access, and other malicious activities. EDR solutions are vital for identifying threats that may bypass network security measures.
3. Security Information and Event Management (SIEM): A SIEM system acts as a central hub for collecting and analyzing security data from various sources, including firewalls, intrusion detection systems (IDS), and logs. It provides a comprehensive overview of security events, enabling organizations to correlate incidents, identify patterns, and gain valuable insights into potential threats.
4. Threat Intelligence: Keeping abreast of the latest threat intelligence is crucial for proactive threat detection. By leveraging threat feeds, reports, and industry best practices, organizations can stay informed about emerging threats, tactics, and vulnerabilities. Threat intelligence allows for the development of tailored security measures and the timely identification of potential threats.
5. Incident Response Plan: Having a well-defined incident response plan is essential for effectively handling security incidents. The plan outlines roles, responsibilities, and procedures for responding to threats, including containment, investigation, remediation, and recovery. A robust incident response plan ensures a coordinated and efficient response to minimize damage and disruption.
6. Regular Security Assessments: Regular security assessments, including vulnerability scans and penetration testing, play a vital role in identifying weaknesses and vulnerabilities in an organization’s security posture. These assessments help uncover potential entry points for attackers and provide insights into areas that require improvement.
By implementing and maintaining these key elements, organizations can establish a robust cyber threat detection system that empowers them to proactively identify, respond to, and mitigate potential risks. A comprehensive approach, combined with ongoing monitoring, analysis, and threat intelligence, is crucial for staying ahead of the curve in the ever-changing landscape of cyber threats.
Proactive Measures: Threat Hunting and Intelligence Gathering
In today’s dynamic cyber threat landscape, reactive security measures are no longer sufficient. Organizations must embrace a proactive approach to stay ahead of the curve and mitigate potential threats. This is where threat hunting and intelligence gathering come into play.
Threat hunting is a proactive security practice that involves actively searching for malicious activity within an organization’s network and systems. It goes beyond traditional security tools and utilizes a combination of techniques, such as:
- Analyzing network traffic for anomalies
- Investigating suspicious user activity
- Examining endpoint logs for malware indicators
Intelligence gathering complements threat hunting by providing valuable insights into emerging threats and attacker tactics. This involves:
- Monitoring industry news and threat intelligence feeds
- Analyzing attack trends and threat actor profiles
- Collaborating with security communities and sharing information
By implementing these proactive measures, organizations can achieve several benefits, including:
- Early detection and response to emerging threats
- Improved threat awareness and understanding of attacker motivations
- Enhanced security posture through proactive risk mitigation
- Reduced attack surface by identifying and addressing vulnerabilities
In conclusion, proactive threat hunting and intelligence gathering are essential components of a comprehensive cybersecurity strategy. By investing in these practices, organizations can gain a significant advantage in the fight against cyber threats and safeguard their critical assets.
Leveraging Technology: Intrusion Detection Systems (IDS) and SIEM Tools
In today’s digital landscape, organizations face a constant barrage of cyber threats. From sophisticated malware to targeted attacks, the threat landscape is constantly evolving. To stay ahead of the curve, businesses must adopt effective cyber threat detection strategies. One crucial aspect of this is leveraging technology to identify and respond to potential threats. Two key technologies in this regard are Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools.
Intrusion Detection Systems (IDS) act as the first line of defense against cyberattacks. They monitor network traffic for suspicious activity, identifying potential threats that may have bypassed other security measures. By analyzing network patterns and comparing them to known attack signatures, IDS can detect a wide range of malicious activities, including unauthorized access, data exfiltration, and denial-of-service attacks. They can then alert security personnel or automatically take actions to mitigate the threat, such as blocking suspicious connections.
Security Information and Event Management (SIEM) tools play a crucial role in consolidating and analyzing security data from various sources within an organization. They gather logs from firewalls, IDS, servers, and other security devices, providing a centralized platform for monitoring and analyzing security events. SIEM tools use sophisticated correlation engines to identify patterns and anomalies that may indicate a security breach. By aggregating and analyzing data from diverse sources, SIEMs provide a comprehensive view of the security posture of an organization and facilitate proactive threat detection and response.
By implementing IDS and SIEM tools, organizations can significantly enhance their cyber threat detection capabilities. These technologies provide real-time visibility into network activity, allowing security teams to identify and respond to threats quickly and effectively. By leveraging these tools, businesses can strengthen their security posture, protect their critical assets, and mitigate the risks associated with cyberattacks.
The Role of Human Expertise in Threat Detection
In the ever-evolving landscape of cybersecurity, technology plays a crucial role in threat detection. However, human expertise remains an indispensable component of a robust defense strategy. While automated systems can analyze vast amounts of data and identify patterns, they often struggle with the nuances and complexities of human behavior, which are key indicators of malicious activity.
Human analysts bring a unique perspective to threat detection. Their ability to critically evaluate data, understand the context of events, and interpret subtle signs of compromise is invaluable. They can recognize when an automated system may be misinterpreting data or missing critical details. Moreover, human expertise is essential for developing and refining threat detection strategies, adapting to emerging threats, and providing valuable insights into attacker motivations and techniques.
The synergy between human intelligence and technology is paramount in staying ahead of the curve. By leveraging the strengths of both, organizations can build a comprehensive and effective cyber threat detection system. Human analysts can oversee and fine-tune automated systems, while technology can empower analysts to process information faster and identify threats more efficiently.
In conclusion, the role of human expertise in threat detection is critical. It complements and enhances technology-driven solutions, ensuring a well-rounded and adaptable defense against ever-evolving cyber threats.
Incident Response: Minimizing Damage and Ensuring Business Continuity
A robust incident response plan is crucial for any organization facing cyber threats. It’s not just about reacting to incidents, but about minimizing damage and ensuring business continuity during and after a cyberattack. This involves a structured approach to identify, contain, eradicate, and recover from security incidents.
Here’s how a well-defined incident response plan can help:
- Rapid Detection: A key element is early detection. This requires continuous monitoring, advanced threat intelligence, and automated security tools to identify suspicious activities promptly.
- Containment: Once an incident is detected, swift containment is essential to prevent further spread of the attack. This may involve isolating infected systems, blocking network access, and taking other immediate actions.
- Eradication: Eradication focuses on removing the threat completely from the environment. This may involve restoring affected systems, patching vulnerabilities, and implementing additional security measures.
- Recovery: The final phase involves restoring normal operations and ensuring business continuity. This includes data recovery, system restoration, and operational procedures to minimize downtime and disruption.
A comprehensive incident response plan should be regularly tested and updated to reflect evolving threats and organizational changes. It’s also important to have a clear communication strategy for informing stakeholders, including employees, customers, and regulatory bodies, about the incident and its impact.
By focusing on incident response, organizations can proactively mitigate the impact of cyberattacks, protect their assets, and maintain business continuity.
Best Practices for Effective Cyber Threat Detection

In today’s digital landscape, cyber threats are becoming increasingly sophisticated and relentless. To stay ahead of the curve and protect your organization, implementing robust cyber threat detection strategies is crucial. This article will explore best practices for effective cyber threat detection, equipping you with the knowledge and tools to bolster your defenses.
1. Proactive Threat Hunting: Instead of passively waiting for attacks to occur, proactive threat hunting involves actively searching for potential threats within your network. This includes analyzing system logs, network traffic, and user behavior to identify suspicious activities that may have been missed by traditional security tools.
2. Implement a Multi-Layered Security Approach: A multi-layered security approach encompasses various security controls that work together to create a robust defense. These layers include firewalls, intrusion detection systems (IDS), antivirus software, and endpoint security solutions. This strategy ensures that even if one layer is breached, other layers are in place to mitigate the impact.
3. Conduct Regular Security Assessments: Regular security assessments help identify vulnerabilities and weaknesses in your systems and networks. These assessments should be conducted by qualified professionals who can provide comprehensive insights and recommendations for improvement. Penetration testing, vulnerability scanning, and security audits are essential components of these assessments.
4. Embrace Automation and Artificial Intelligence (AI): Utilizing automation and AI in cyber threat detection can significantly improve efficiency and effectiveness. AI-powered tools can analyze vast amounts of data, identify anomalies, and provide real-time threat alerts. Automation can streamline repetitive tasks, freeing up security teams to focus on more strategic initiatives.
5. Foster a Culture of Security Awareness: Educating employees about cyber threats and best practices is paramount. A strong security awareness culture encourages employees to be vigilant and report suspicious activities. Regular security training, phishing simulations, and communication campaigns are essential for building a culture of security awareness.
6. Embrace a Collaborative Approach: Collaborating with industry peers, security experts, and information sharing platforms can provide valuable insights and intelligence. Sharing threat information, best practices, and incident response strategies enhances collective security and helps organizations learn from each other’s experiences.
By implementing these best practices, organizations can build a comprehensive and robust cyber threat detection strategy. Proactive threat hunting, a multi-layered approach, regular security assessments, automation, AI, and a culture of security awareness are crucial elements in staying ahead of the curve and mitigating cyber risks.
Common Pitfalls to Avoid in Threat Detection

In the constantly evolving landscape of cyber threats, having robust threat detection strategies is crucial for safeguarding your organization. While many tools and techniques are available, it’s vital to avoid common pitfalls that can hinder your efforts.
One common pitfall is overreliance on signature-based detection. These methods rely on identifying known threats, leaving you vulnerable to zero-day attacks and variants of existing threats. Another critical pitfall is ignoring human factors. Social engineering attacks often exploit human vulnerabilities, making it essential to train employees on security awareness and phishing detection.
Failing to prioritize threats is another pitfall. It’s crucial to categorize threats based on likelihood and impact, focusing resources on the most critical risks. Additionally, neglecting incident response planning is a significant error. Having a detailed plan in place for handling cyber incidents allows for a swift and effective response, minimizing damage.
Ignoring threat intelligence is also a serious pitfall. Staying informed about the latest threats and attack trends is essential for proactively identifying potential risks. Lastly, failing to adapt your strategies to the evolving threat landscape is a common mistake. Regularly evaluate your threat detection tools and techniques to ensure they remain effective against the latest threats.
By avoiding these common pitfalls, organizations can significantly enhance their ability to detect and respond to cyber threats effectively. Proactive measures, continuous learning, and a robust incident response plan are crucial for staying ahead of the curve in the ever-changing world of cybersecurity.
Emerging Trends Shaping the Future of Cyber Threat Detection

The cyber threat landscape is constantly evolving, with attackers becoming more sophisticated and innovative in their methods. To stay ahead of the curve, organizations need to embrace emerging trends in cyber threat detection. These trends are transforming how we approach security, enabling more proactive and effective defense strategies.
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing threat detection. AI/ML algorithms can analyze massive datasets, identify patterns, and predict potential threats in real-time. This allows security teams to prioritize alerts, focus on the most critical issues, and automate tasks for faster response times.
Threat Intelligence Sharing is becoming increasingly crucial. By sharing threat data and insights with other organizations, businesses can gain a more comprehensive understanding of evolving threats and develop better defenses. This collaboration is particularly essential for addressing complex and targeted attacks.
Behavioral Analytics focuses on understanding user and device behavior. By monitoring deviations from normal patterns, security teams can detect suspicious activities that may indicate a compromise. Behavioral analytics is particularly useful for identifying insider threats and detecting malware that has bypassed traditional security measures.
Cloud Security Posture Management (CSPM) is essential for securing cloud environments. CSPM tools provide visibility into cloud configurations, identify vulnerabilities, and ensure compliance with security best practices. With the increasing adoption of cloud services, CSPM is becoming a critical aspect of effective cyber threat detection.
Extended Detection and Response (XDR) is a holistic approach that combines threat detection and response capabilities across various security solutions. XDR platforms provide a centralized view of security events, enabling faster threat analysis and remediation. This integrated approach simplifies threat management and improves overall security posture.
As cyber threats continue to evolve, organizations must adapt their security strategies accordingly. Embracing emerging trends in cyber threat detection is essential for staying ahead of the curve and protecting against the ever-growing array of threats.
Case Studies: Successful Cyber Threat Detection in Action
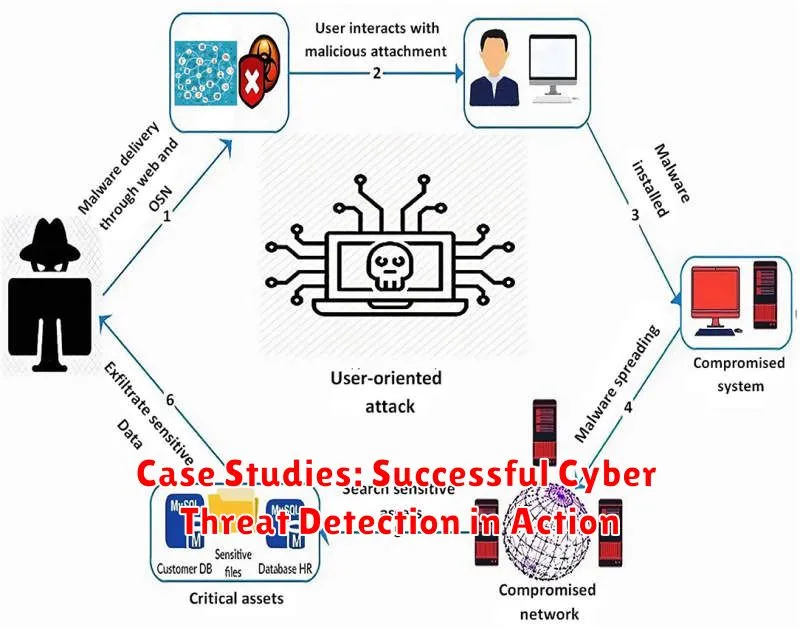
Cybersecurity is a constantly evolving landscape, with new threats emerging all the time. It’s essential to have effective strategies in place to detect and respond to these threats before they cause significant damage.
To understand the power of effective cyber threat detection, let’s examine some real-world case studies:
Case Study 1: Early Detection Prevents Data Breach
A large financial institution implemented a comprehensive security information and event management (SIEM) system. This system was instrumental in detecting a sophisticated phishing campaign targeting employees. The SIEM system identified unusual login attempts and flagged suspicious activity. The security team was able to quickly isolate the compromised accounts and prevent a widespread data breach. This timely intervention saved the company millions in potential losses.
Case Study 2: Real-time Threat Intelligence Stops Attack
An online retailer leveraged real-time threat intelligence feeds to identify a zero-day vulnerability in their web application. By quickly patching the vulnerability and deploying security updates, the retailer effectively blocked a large-scale distributed denial-of-service (DDoS) attack that would have brought their website down.
Case Study 3: Behavioral Analytics Exposes Insider Threat
A technology company utilized user behavioral analytics to detect unusual activity from an employee. The analytics system flagged an employee’s access to sensitive data outside of their normal work hours. Further investigation revealed the employee was attempting to exfiltrate confidential information. This incident highlights the importance of monitoring user behavior to identify potential insider threats.
These case studies demonstrate the critical role of proactive cyber threat detection in mitigating potential damage. By investing in the right tools and strategies, organizations can significantly improve their security posture and stay ahead of the curve in the fight against cybercrime.
Building a Cyber-Resilient Organization: A Continuous Process
In today’s digital landscape, cyber threats are becoming increasingly sophisticated and prevalent. Organizations of all sizes are vulnerable to attacks, and the consequences can be devastating, ranging from data breaches and financial losses to reputational damage and operational disruptions. To mitigate these risks, organizations must adopt a proactive approach to cybersecurity, focusing on building a strong cyber-resilient foundation. This involves implementing a comprehensive strategy that goes beyond traditional security measures and embraces a continuous process of improvement.
A cyber-resilient organization is one that can withstand and recover from cyberattacks effectively. It possesses the ability to detect threats, respond swiftly, and minimize the impact on its operations. Building such an organization requires a holistic approach that encompasses several key elements:
1. Strong Cybersecurity Culture
A strong cybersecurity culture is fundamental to building a cyber-resilient organization. It involves fostering a shared understanding of cybersecurity risks and responsibilities among all employees, from top management to frontline staff. This culture should emphasize proactive measures, such as regular security awareness training, clear communication channels, and a culture of reporting suspicious activities.
2. Robust Security Controls
Organizations must implement robust security controls to protect their systems and data from unauthorized access. This includes measures like firewalls, intrusion detection systems (IDS), antivirus software, and multi-factor authentication. These controls should be regularly updated and tested to ensure their effectiveness against evolving threats.
3. Incident Response Plan
A well-defined incident response plan is crucial for effective threat detection and response. This plan should outline the steps to be taken in case of a cyberattack, including procedures for detection, containment, recovery, and post-incident analysis. Regular drills and simulations can help ensure the plan is effective and that employees are familiar with their roles and responsibilities.
4. Continuous Monitoring and Improvement
Cybersecurity is not a one-time effort; it’s a continuous process. Organizations must actively monitor their systems for suspicious activity and regularly review their security controls to identify gaps and vulnerabilities. This involves utilizing threat intelligence feeds, vulnerability scanning tools, and security information and event management (SIEM) systems.
5. Collaboration and Partnerships
Collaboration with external partners, such as security vendors, cybersecurity experts, and law enforcement agencies, can enhance an organization’s cyber resilience. Sharing threat information, best practices, and incident response resources can help organizations stay ahead of emerging threats and improve their overall security posture.
Building a cyber-resilient organization is an ongoing journey, not a destination. By embracing a continuous improvement mindset, organizations can adapt to evolving threats and protect their assets from the ever-growing cyber landscape. This requires a commitment to proactive security measures, effective incident response, and a strong cybersecurity culture that prioritizes the protection of sensitive information.

