In today’s digital landscape, where cyberattacks are becoming increasingly sophisticated and relentless, organizations are constantly seeking innovative ways to protect their valuable assets. AI-powered cybersecurity tools are emerging as a game-changer, revolutionizing the way we detect and respond to threats. By leveraging the power of artificial intelligence, these tools can analyze vast amounts of data, identify anomalies, and predict potential attacks with unprecedented accuracy. This transformative technology empowers security teams to stay ahead of the curve, proactively mitigate risks, and minimize the impact of cyber incidents.
From intrusion detection systems that learn to distinguish between legitimate and malicious traffic to endpoint security solutions that can detect and block zero-day exploits, AI-driven cybersecurity is transforming every aspect of threat management. With its ability to automate complex tasks, enhance threat intelligence, and provide real-time insights, AI is not only bolstering defenses but also enabling security teams to focus on strategic initiatives and more effectively address emerging threats. This article delves into the exciting world of AI-powered cybersecurity, exploring the key tools, benefits, and challenges associated with this revolutionary technology.
The Rise of AI in Cybersecurity: Addressing Evolving Threats
In the ever-evolving landscape of cybersecurity, the emergence of artificial intelligence (AI) has ushered in a new era of threat detection and response. The relentless sophistication of cyberattacks, coupled with the increasing volume and complexity of data, has created an overwhelming challenge for traditional security methods. AI, with its ability to process massive datasets, identify patterns, and make predictions, is proving to be a game-changer in fortifying our digital defenses.
AI-powered cybersecurity tools are rapidly transforming the way we approach security. They can analyze vast amounts of data from various sources, including network traffic, system logs, and user behavior, to identify suspicious activities and potential threats. These tools leverage machine learning algorithms to learn from past attacks and adapt to new threats, providing a proactive and dynamic defense mechanism.
One of the most significant advantages of AI in cybersecurity is its ability to automate routine tasks. AI-powered systems can automatically detect and respond to threats, freeing up human analysts to focus on more complex and strategic security initiatives. This automation not only enhances efficiency but also reduces the risk of human error, which is a common factor in cybersecurity incidents.
As cyberattacks become increasingly sophisticated, AI is essential for staying ahead of the curve. By leveraging AI, organizations can gain a significant advantage in detecting and responding to threats, mitigating risks, and protecting their critical assets. The future of cybersecurity is undeniably intertwined with AI, and embracing this transformative technology is crucial for building a more secure digital world.
How AI Enhances Threat Detection and Response Capabilities
Artificial intelligence (AI) is revolutionizing cybersecurity by enhancing threat detection and response capabilities. AI-powered tools are transforming how organizations identify, analyze, and respond to cyber threats. Here are some key ways AI is making a significant impact:
Automated Threat Detection: AI algorithms can analyze vast amounts of data, including network traffic, system logs, and user behavior, to identify anomalies and potential threats that might go unnoticed by human analysts. This allows for faster detection and prevents threats from escalating.
Real-time Threat Intelligence: AI can continuously gather and analyze threat intelligence from various sources, including open-source data, security feeds, and dark web activities. This provides organizations with up-to-the-minute insights into emerging threats and vulnerabilities.
Advanced Threat Analytics: AI algorithms can leverage machine learning techniques to identify complex attack patterns and correlations, which may not be easily discernible by traditional security tools. This allows for more accurate threat assessment and proactive defense.
Improved Incident Response: AI can automate tasks like incident prioritization, threat containment, and remediation actions. By automating these processes, security teams can respond to threats more efficiently and effectively.
Enhanced Security Posture: AI can help organizations identify security gaps and vulnerabilities in their infrastructure and applications. This allows for proactive security improvements and a more robust defense against attacks.
Overall, AI is playing a critical role in enhancing cybersecurity by automating threat detection, providing real-time intelligence, improving threat analytics, streamlining incident response, and strengthening security postures. Organizations are increasingly relying on AI-powered tools to stay ahead of evolving cyber threats and protect their valuable assets.
Exploring Different Types of AI-Powered Cybersecurity Tools
In the rapidly evolving landscape of cybersecurity, Artificial Intelligence (AI) is playing a crucial role in transforming how organizations detect, prevent, and respond to threats. AI-powered cybersecurity tools are being deployed across a wide range of applications, offering significant advantages in terms of efficiency, accuracy, and speed. This article delves into the different types of AI-powered cybersecurity tools that are shaping the future of threat detection and response.
1. Threat Intelligence and Analysis Tools: These tools leverage AI algorithms to gather and analyze vast amounts of data from various sources, including threat feeds, malware repositories, and social media. By identifying patterns and anomalies, AI-powered threat intelligence tools can help organizations proactively detect emerging threats and understand the tactics, techniques, and procedures (TTPs) used by attackers.
2. Endpoint Security Solutions: AI-powered endpoint security solutions are designed to protect individual devices, such as laptops, desktops, and mobile phones, from malicious attacks. These tools use machine learning to detect suspicious activities and malware, blocking threats before they can cause harm. They can also monitor for signs of compromise, such as unauthorized access or data exfiltration.
3. Network Security Monitoring and Intrusion Detection Systems (IDS): AI is being integrated into network security monitoring and IDS systems to enhance threat detection capabilities. These tools analyze network traffic in real-time, identifying anomalies and potential attacks. By leveraging machine learning, AI-powered network security solutions can automatically adapt to evolving threats and provide faster, more accurate alerts.
4. Security Information and Event Management (SIEM): SIEM tools play a crucial role in centralizing security data from multiple sources and providing a comprehensive view of security events. AI is being used to enhance SIEM capabilities by automating log analysis, detecting complex threats, and prioritizing alerts based on severity and potential impact.
5. Security Orchestration, Automation, and Response (SOAR): SOAR platforms streamline incident response by automating repetitive tasks and orchestrating actions across different security tools. AI is being integrated into SOAR solutions to enhance threat analysis, incident prioritization, and the development of automated response playbooks.
The adoption of AI-powered cybersecurity tools is rapidly accelerating, as organizations strive to stay ahead of the ever-evolving threat landscape. By leveraging the power of AI, businesses can significantly improve their threat detection, prevention, and response capabilities, ensuring the security and resilience of their systems and data.
AI-Driven Security Information and Event Management (SIEM)
AI is revolutionizing cybersecurity by empowering tools like Security Information and Event Management (SIEM) systems. Traditionally, SIEMs relied heavily on human analysts to sift through massive volumes of security data, identifying threats and responding to incidents. However, the sheer scale of modern data streams, combined with increasingly sophisticated attacks, has made human-driven analysis increasingly challenging.
AI-driven SIEMs address this challenge by automating threat detection and response. These systems leverage machine learning algorithms to analyze security data, identify patterns, and flag potential threats. AI-powered SIEMs can detect anomalies, correlate events, and prioritize alerts based on severity and likelihood of attack. This enables security teams to focus on the most critical threats, significantly reducing alert fatigue and response times.
Moreover, AI-driven SIEMs offer several key benefits:
- Improved Threat Detection: AI algorithms can identify subtle patterns and anomalies that might escape human detection, leading to earlier identification of threats.
- Faster Response Times: AI-powered automation streamlines incident response, enabling security teams to respond to threats quicker and more efficiently.
- Enhanced Accuracy: AI algorithms reduce the likelihood of false positives and false negatives, improving the accuracy of threat assessments.
- Proactive Threat Prevention: AI can analyze historical data to predict future threats and implement proactive security measures.
As AI technology continues to evolve, we can expect AI-driven SIEMs to become even more sophisticated, offering a powerful defense against the ever-growing cybersecurity threats.
User and Entity Behavior Analytics (UEBA) with AI
User and Entity Behavior Analytics (UEBA) is a powerful cybersecurity tool that leverages artificial intelligence (AI) to analyze user and entity behavior patterns and detect potential threats. By monitoring and analyzing data from various sources, such as network traffic, system logs, and user activities, UEBA systems can identify anomalies and suspicious activities that might indicate a security breach. AI algorithms play a crucial role in UEBA by enabling the system to learn normal behavior patterns and identify deviations that could signal malicious intent.
UEBA with AI offers several advantages for cybersecurity teams:
- Proactive threat detection: UEBA systems can identify threats before they cause significant damage by detecting unusual activities and potential attacks in real time.
- Improved threat visibility: UEBA provides a comprehensive view of user and entity behavior, allowing security teams to understand the entire attack landscape and identify potential vulnerabilities.
- Reduced false positives: By using AI algorithms to learn normal behavior patterns, UEBA systems can distinguish between legitimate and malicious activities, reducing the number of false alarms.
- Automated incident response: Some UEBA systems can automatically respond to detected threats by isolating compromised systems or blocking malicious activity.
UEBA with AI is a valuable addition to any cybersecurity arsenal, providing a proactive and intelligent approach to threat detection and response. By leveraging the power of AI, organizations can enhance their security posture and protect their sensitive data from emerging threats.
AI-Powered Threat Intelligence Platforms
AI-powered threat intelligence platforms are essential tools for modern cybersecurity. These platforms leverage the power of artificial intelligence to analyze vast amounts of data, identify emerging threats, and provide actionable insights to security teams. They automate threat detection and response processes, enabling faster and more effective threat mitigation.
These platforms gather data from various sources, including internal systems, external threat feeds, open-source intelligence, and social media. They use advanced algorithms to analyze this data, identify patterns, and detect anomalies that could indicate malicious activity. By correlating different data points, they can uncover hidden connections and create a comprehensive view of the threat landscape.
Key Features of AI-Powered Threat Intelligence Platforms:
- Automated Threat Detection: AI algorithms analyze data streams in real-time, identifying suspicious activities and potential threats.
- Threat Intelligence Enrichment: Platforms enrich threat intelligence data by cross-referencing it with various sources, providing a more comprehensive understanding of threats.
- Vulnerability Assessment: AI can assess the organization’s vulnerabilities and prioritize mitigation efforts based on risk levels.
- Threat Hunting: These platforms can actively search for hidden threats within the organization’s network, proactively identifying and responding to attacks.
- Incident Response Automation: AI can automate incident response processes, such as containment, isolation, and remediation, reducing the time it takes to recover from attacks.
Benefits of AI-Powered Threat Intelligence Platforms:
- Enhanced Threat Visibility: Gaining a comprehensive understanding of the threat landscape, including known and emerging threats.
- Faster Threat Detection and Response: Automating threat detection and response processes, reducing the time it takes to identify and mitigate threats.
- Improved Security Posture: Proactively identifying and addressing vulnerabilities, strengthening the organization’s overall security posture.
- Reduced Security Costs: Automating tasks and improving efficiency, reducing the cost of security operations.
In conclusion, AI-powered threat intelligence platforms are essential tools for modern cybersecurity, enabling organizations to proactively identify, analyze, and respond to threats. By leveraging the power of AI, these platforms provide a significant advantage in today’s increasingly complex threat landscape.
Benefits of Implementing AI in Cybersecurity Strategies
Artificial intelligence (AI) is rapidly transforming the cybersecurity landscape, offering a powerful arsenal of tools to enhance threat detection, response, and overall security posture.
Here are some key benefits of implementing AI in cybersecurity strategies:
1. Enhanced Threat Detection: AI algorithms can analyze vast amounts of data from various sources, including network traffic, user behavior, and security logs. By identifying patterns and anomalies that may go unnoticed by human analysts, AI significantly improves the ability to detect threats in real-time.
2. Automated Threat Response: AI-powered security tools can automate threat response actions, such as blocking malicious IP addresses, quarantining infected files, and notifying security personnel. This automation reduces the time it takes to respond to threats, minimizing potential damage and mitigating risks.
3. Improved Security Posture: AI can continuously analyze security data to identify vulnerabilities and weaknesses in systems and applications. By proactively identifying and addressing these vulnerabilities, AI helps organizations enhance their overall security posture and prevent attacks.
4. Reduced Costs: While initial investments in AI cybersecurity solutions may seem costly, they can lead to significant cost savings in the long run. By automating tasks and reducing the need for manual security efforts, AI can help organizations optimize resource allocation and lower operational costs.
5. Proactive Security: AI enables organizations to move from a reactive to a proactive security stance. By analyzing data and predicting potential threats, AI empowers organizations to take preventative measures and mitigate risks before they escalate.
Challenges and Considerations for Adopting AI-Powered Tools
While AI-powered cybersecurity tools offer a powerful advantage in threat detection and response, organizations must carefully consider the challenges and considerations involved in their adoption.
One key challenge is data quality and availability. AI algorithms rely on vast amounts of high-quality data to train effectively. Organizations need to ensure they have sufficient data, and that it is accurate, relevant, and representative of real-world threats.
Another challenge is interpretability. AI models can be complex “black boxes,” making it difficult to understand how they reach their conclusions. This lack of transparency can be problematic when investigating security incidents or explaining decisions to stakeholders.
Integration with existing security infrastructure is also crucial. Organizations need to ensure that AI tools can seamlessly integrate with their existing systems and processes.
Cost can be a significant consideration, as AI tools often require specialized hardware and software, as well as ongoing maintenance and support.
Finally, organizations must address security risks associated with AI tools themselves. These tools could be targeted by attackers, potentially leading to data breaches or other security incidents.
By carefully considering these challenges and implementing effective strategies for addressing them, organizations can maximize the benefits of AI-powered cybersecurity tools while mitigating potential risks.
Ensuring Transparency and Ethical Use of AI in Security
The rapid advancements in Artificial Intelligence (AI) are revolutionizing the cybersecurity landscape, empowering organizations with powerful tools to detect and respond to threats more effectively. AI-powered cybersecurity tools offer numerous benefits, including automated threat detection, improved threat intelligence, and faster incident response. However, as AI systems become increasingly sophisticated, ensuring their transparency and ethical use becomes paramount. This article delves into the critical considerations for responsible AI implementation in security.
Transparency is fundamental to building trust in AI systems. Organizations must clearly understand how AI algorithms make decisions, especially when they impact critical security functions. Explainability is crucial, allowing security professionals to interpret the reasoning behind AI-driven actions, identify biases, and ensure accountability.
Ethical considerations are equally important. AI systems must be developed and deployed in a way that aligns with ethical principles, such as fairness, non-discrimination, and privacy. Bias detection and mitigation should be a key focus, as AI algorithms can inherit biases from the data they are trained on, potentially leading to discriminatory outcomes.
The ethical use of AI in security also requires addressing concerns around algorithmic transparency and explainability. Organizations need to implement mechanisms that allow security professionals to understand how AI systems make decisions, identify potential biases, and hold developers accountable.
In conclusion, while AI-powered cybersecurity tools offer significant benefits, their transparency and ethical use must be prioritized. Organizations must embrace explainability, bias detection and mitigation, and ethical frameworks to ensure that these powerful tools are deployed responsibly and enhance security without compromising human values.
Future Trends: AI and the Evolving Cybersecurity Landscape
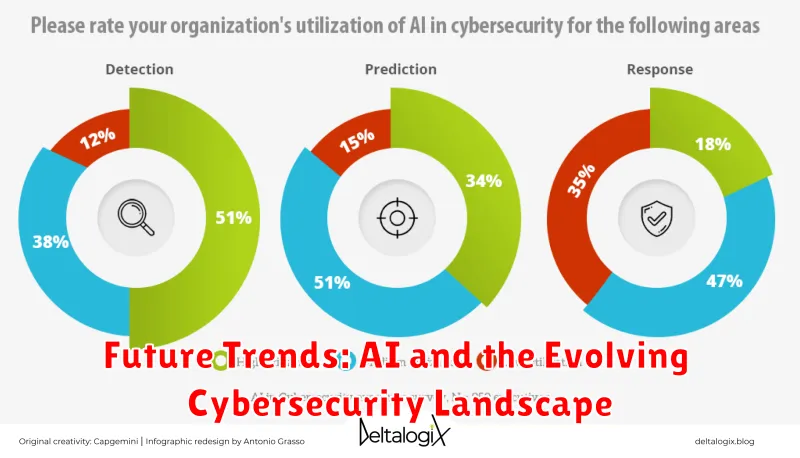
The cybersecurity landscape is constantly evolving, with new threats emerging daily. To stay ahead of the curve, organizations must embrace innovative solutions, and artificial intelligence (AI) is proving to be a game-changer. AI-powered cybersecurity tools are rapidly transforming threat detection and response, offering unprecedented levels of protection.
One of the most significant trends is the increasing use of AI for threat detection. AI algorithms can analyze massive amounts of data, identifying patterns and anomalies that traditional security systems might miss. This proactive approach allows security teams to detect threats early, preventing potential breaches before they cause significant damage.
Another key trend is the rise of AI-driven security automation. AI can automate repetitive tasks, such as vulnerability scanning and incident response, freeing up security professionals to focus on more strategic initiatives. This automation significantly improves efficiency and reduces the time it takes to respond to threats.
Looking ahead, we can expect even more advanced AI applications in cybersecurity. AI-powered threat intelligence will become increasingly sophisticated, providing real-time insights into emerging threats. AI-driven security orchestration and automation will streamline security operations, enabling organizations to respond to threats more effectively.
The future of cybersecurity is undeniably AI-driven. By leveraging the power of AI, organizations can stay ahead of evolving threats, improve their security posture, and protect their valuable assets. The rapid advancements in AI technology will continue to shape the cybersecurity landscape, demanding a proactive and adaptive approach from security professionals.
Choosing the Right AI-Powered Tools for Your Organization

In today’s complex and evolving threat landscape, cybersecurity teams need every advantage they can get. This is where AI-powered cybersecurity tools come in, offering a powerful solution for transforming threat detection and response. With the ability to analyze massive datasets, identify patterns, and predict threats, AI tools can significantly enhance your organization’s security posture. However, selecting the right tools for your specific needs is crucial. This article will guide you through the key considerations for choosing AI-powered cybersecurity tools that effectively address your organization’s unique challenges.
The first step in selecting AI-powered tools is to define your organization’s specific requirements. What are your biggest security vulnerabilities? What are your key goals for improving your cybersecurity posture? Are you looking to enhance threat detection, automate incident response, or improve your overall security posture? Once you have a clear understanding of your requirements, you can begin evaluating different AI-powered tools.
Consider the following factors when evaluating different tools:
- Integration with existing systems: A seamless integration with your existing security infrastructure is essential for optimal performance.
- Scalability: Ensure the tool can adapt to your organization’s growth and changing security needs.
- Ease of use: Look for tools with intuitive interfaces and user-friendly dashboards that allow your security team to easily interpret data and take action.
- Data privacy and security: Assess the tool’s data handling practices to ensure compliance with relevant regulations and protect sensitive information.
- Cost and ROI: Consider the cost of the tool and the potential return on investment in terms of improved security, reduced risk, and cost savings.
Before committing to a specific AI-powered cybersecurity tool, it is recommended to conduct a pilot program to evaluate its effectiveness in your environment. This will allow you to assess the tool’s performance, identify any potential issues, and make informed decisions about its suitability for your organization’s long-term cybersecurity needs.
By carefully considering these factors and conducting thorough due diligence, you can choose the right AI-powered cybersecurity tools that will significantly enhance your organization’s threat detection and response capabilities. These tools can help you stay ahead of the curve in today’s evolving threat landscape, safeguarding your organization’s valuable assets and protecting your reputation.
Integrating AI with Existing Security Infrastructure

The integration of AI into existing security infrastructure is essential for maximizing the benefits of AI-powered cybersecurity tools. Integrating AI with existing systems allows for the creation of a comprehensive and robust security posture that leverages the strengths of both traditional and modern security approaches. This integration involves connecting AI-powered tools to existing security information and event management (SIEM) systems, network security appliances, endpoint security platforms, and other critical infrastructure components.
By integrating AI into existing security infrastructure, organizations can achieve several key benefits:
- Enhanced threat detection and response: AI can analyze vast amounts of security data and identify subtle patterns that may indicate malicious activity, which can help organizations detect threats more quickly and effectively.
- Automated incident response: AI-powered tools can automate many of the tasks involved in incident response, such as threat containment and remediation, which can significantly reduce the time and resources required to respond to security incidents.
- Improved security posture: Integrating AI into existing systems can help organizations identify and address security vulnerabilities more effectively, improving their overall security posture.
- Reduced false positives: AI can help to reduce the number of false positives generated by security tools, which can free up security teams to focus on real threats.
To effectively integrate AI with existing security infrastructure, organizations should follow a phased approach:
- Identify key security needs: Organizations should first identify their most critical security needs and how AI can be used to address those needs.
- Select the right AI-powered tools: There are many different AI-powered cybersecurity tools available, and it’s important to select the right tools for the organization’s specific needs.
- Develop a clear integration strategy: Organizations should develop a clear strategy for integrating AI-powered tools with existing systems, including how data will be shared and how security policies will be enforced.
- Pilot and test: Before deploying AI-powered tools across the entire organization, it’s important to pilot and test them in a controlled environment to ensure that they are working as expected.
- Monitor and adapt: Organizations should continuously monitor the performance of their AI-powered tools and adapt their integration strategy as needed to ensure that they are meeting the organization’s changing security needs.
By taking a strategic approach to integrating AI with existing security infrastructure, organizations can unlock the full potential of AI-powered cybersecurity tools and significantly enhance their ability to detect, respond to, and prevent cyber threats.

