The Internet of Things (IoT) has revolutionized the way we live, work, and interact with the world around us. From smart homes and connected cars to industrial automation and healthcare monitoring, IoT devices are seamlessly woven into our daily lives. However, with this unprecedented connectivity comes a new set of security challenges. As the number of connected devices explodes, so too do the vulnerabilities that hackers can exploit. Navigating the labyrinth of IoT security is crucial to protecting our privacy, safety, and data.
The increasing sophistication of cyberattacks targeting IoT devices demands a comprehensive approach to security. IoT security encompasses a wide range of considerations, including device authentication, data encryption, secure firmware updates, and robust access controls. This article delves into the pressing challenges facing IoT security and explores innovative solutions that can help us navigate this complex landscape. Discover the latest advancements in IoT security technologies, understand the importance of proactive threat mitigation, and learn how to safeguard your connected world.
The Rise of IoT: Opportunities and Challenges
The Internet of Things (IoT) is rapidly transforming the world around us, connecting billions of devices and creating a vast network of data exchange. This interconnectedness unlocks a myriad of opportunities across various industries, from smart homes and cities to healthcare and manufacturing.
Opportunities abound in the realm of IoT. It promises enhanced efficiency, productivity, and convenience. Smart homes, for instance, enable remote control of appliances and security systems, providing comfort and peace of mind. In healthcare, wearable devices can monitor vital signs and alert medical professionals to potential issues, leading to proactive care and improved patient outcomes. The possibilities are endless, with IoT poised to revolutionize how we live, work, and interact with our surroundings.
However, the exponential growth of IoT comes with its share of challenges, especially in the realm of security. As more devices are interconnected, the attack surface expands, making it easier for malicious actors to exploit vulnerabilities. Data breaches and cyberattacks pose a significant threat to both individuals and organizations, compromising sensitive information and disrupting critical operations.
Understanding the IoT Threat Landscape
The Internet of Things (IoT) promises a future of connected devices, enhancing our lives and revolutionizing industries. However, this interconnected world comes with a growing security risk. As the number of IoT devices proliferates, the threat landscape expands, posing significant challenges to individuals and organizations alike.
One of the most concerning aspects of the IoT threat landscape is the vulnerability of these devices. Many IoT devices are designed with weak security measures, lacking robust authentication mechanisms, encryption, and software updates. This leaves them susceptible to a range of attacks, including:
- Data breaches: Hackers can gain access to sensitive information stored on IoT devices, such as personal data, financial information, and proprietary business data.
- Denial of service attacks: Attackers can disrupt the functionality of IoT devices, rendering them unusable or causing significant downtime.
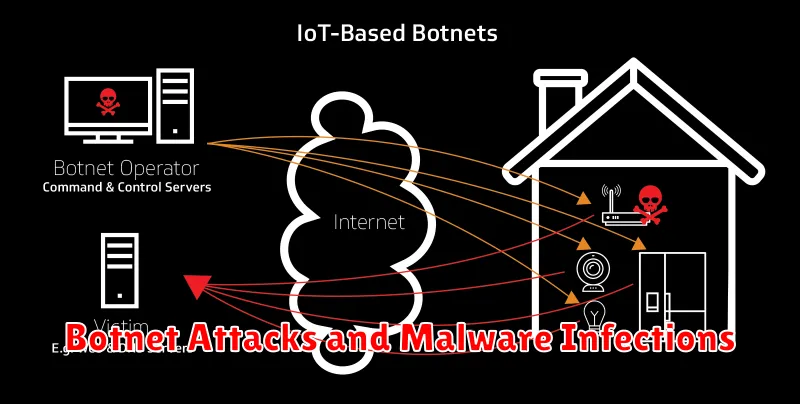
- Botnet creation: IoT devices can be compromised and used as part of botnets, enabling large-scale distributed attacks.
- Physical security threats: Hackers can exploit vulnerabilities in IoT devices to control physical systems, such as smart home appliances or industrial machinery.
Furthermore, the fragmentation of the IoT ecosystem presents another challenge. The lack of standardized security protocols and the diverse range of devices and operating systems make it difficult to implement comprehensive security measures.
Understanding the nature of threats and their potential impact is crucial for navigating the IoT security landscape effectively. By recognizing the vulnerabilities and risks, organizations and individuals can take proactive steps to mitigate these challenges and ensure the secure and responsible deployment of IoT technologies.
Common IoT Security Vulnerabilities
The Internet of Things (IoT) is rapidly changing our lives, but its rapid growth comes with inherent security risks. These connected devices, often with limited resources and security features, present a significant target for attackers. Understanding common vulnerabilities is crucial for protecting your IoT ecosystem.
Weak or Default Credentials: Many IoT devices ship with default usernames and passwords that are easily guessable. Attackers can exploit this to gain unauthorized access and control.
Lack of Secure Software Updates: Outdated software can contain vulnerabilities that attackers can exploit. Many IoT devices lack mechanisms for receiving timely updates, leaving them vulnerable.
Insecure Communication Channels: Data transmitted between IoT devices and the internet is often sent unencrypted, making it easily intercepted by attackers.
Insufficient Data Encryption: Sensitive data stored on IoT devices, such as personal information or financial details, may not be adequately encrypted, making it susceptible to theft.
Lack of Authentication: Some IoT devices lack proper authentication mechanisms, allowing anyone to connect and control them.
Unsecured Networks: Many IoT devices connect to home or office networks without proper security measures, creating entry points for attackers to access the entire network.
These vulnerabilities highlight the need for a multi-layered approach to IoT security. Device manufacturers, network providers, and users must work together to address these risks and ensure a secure and trustworthy IoT environment.
Data Breaches and Privacy Concerns
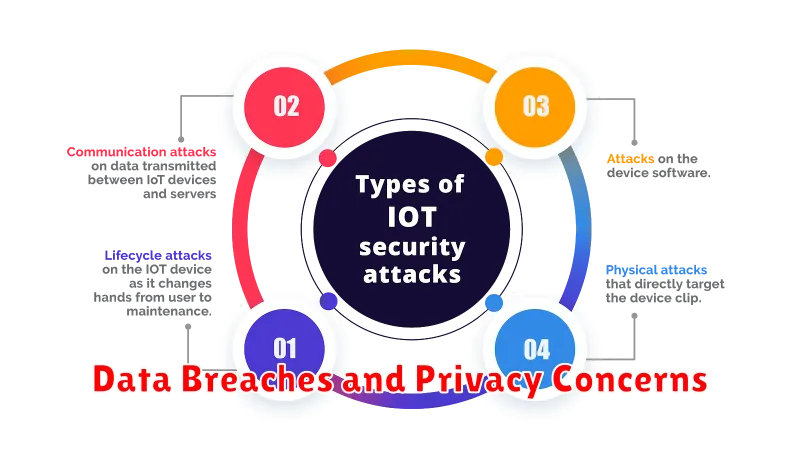
The burgeoning Internet of Things (IoT) landscape, while promising increased convenience and efficiency, brings with it a complex web of security challenges, especially concerning data breaches and privacy concerns. The interconnected nature of IoT devices means a single vulnerability can cascade across the network, exposing sensitive user data and compromising overall system security.
One major concern is the potential for data breaches. With a vast number of devices collecting and transmitting data, the attack surface expands significantly. Hackers can exploit weak security protocols, default passwords, or outdated firmware to gain unauthorized access to sensitive information like personal details, financial data, or even medical records. These breaches can have devastating consequences, leading to identity theft, financial losses, and even physical harm.
Equally alarming are privacy concerns. The constant data collection by IoT devices raises questions about the collection, storage, and use of personal data. Without proper safeguards, user information can be misused for targeted advertising, profiling, or even surveillance purposes. Moreover, the lack of transparency and control over data collection practices can lead to feelings of invasion and distrust.
Addressing these challenges requires a multi-pronged approach. Manufacturers need to prioritize robust security features in their devices, including encryption, authentication protocols, and regular software updates. Users must also be educated about security best practices, such as choosing strong passwords, updating firmware regularly, and being aware of phishing attempts. Moreover, governments and regulatory bodies need to establish clear guidelines for data privacy and security in the IoT ecosystem.
Insecure Authentication and Authorization
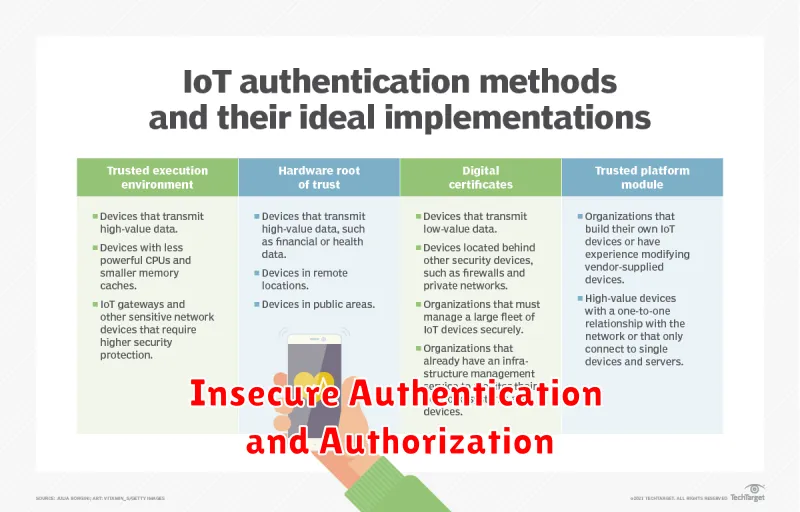
In the realm of the Internet of Things (IoT), where devices seamlessly connect and interact, security stands as a paramount concern. Among the numerous vulnerabilities that plague this interconnected ecosystem, insecure authentication and authorization stand out as significant challenges.
Authentication, the process of verifying a user’s identity, and authorization, the process of granting access based on verified identity, are foundational pillars of secure systems. However, in the IoT landscape, these mechanisms are often implemented with inadequate security measures, creating avenues for malicious actors to exploit.
One prevalent issue is the use of weak or default credentials. Many IoT devices ship with pre-configured passwords that are easily guessable, enabling unauthorized access. The absence of multi-factor authentication further exacerbates the vulnerability, as a single password compromise can grant access to sensitive data and functionalities.
Another critical concern is the lack of robust authorization mechanisms. Devices may fail to properly control access to specific resources or functionalities, allowing unauthorized users to manipulate data or trigger unintended actions. This can lead to data breaches, system malfunctions, and even physical harm.
Addressing these security shortcomings is crucial for ensuring the safety and reliability of IoT deployments. Implementations must prioritize strong authentication protocols, such as two-factor authentication, and utilize secure password management practices. Robust authorization mechanisms, based on granular access control policies, should be implemented to prevent unauthorized actions. Regular security audits and updates are also essential to mitigate emerging vulnerabilities.
Lack of Encryption and Data Protection
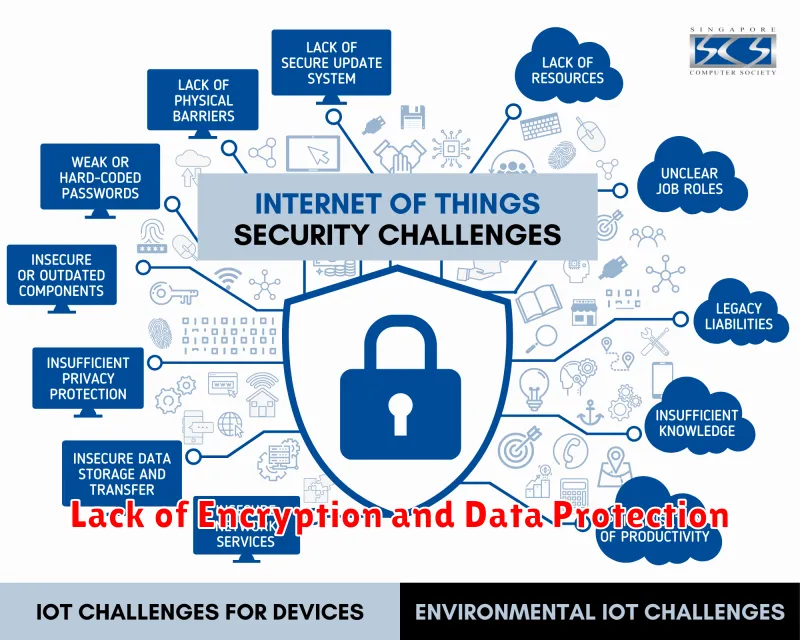
One of the most pressing issues in IoT security is the lack of widespread encryption and robust data protection measures. Many IoT devices are manufactured with minimal security features, leaving sensitive data vulnerable to unauthorized access and exploitation. This lack of encryption creates a gaping hole in the security fabric, allowing attackers to intercept and manipulate data transmitted between devices and the cloud.
The absence of proper data protection mechanisms also exposes user information to risks. Without effective authentication and authorization, attackers can potentially gain control of IoT devices, compromising user privacy and potentially causing harm. This lack of security can lead to various consequences, including data breaches, device hijacking, and even physical harm.
The widespread adoption of strong encryption protocols, such as TLS/SSL, is crucial for protecting data in transit. Additionally, implementing robust data protection measures, such as access controls, data masking, and secure storage solutions, is essential to safeguard sensitive information from unauthorized access.
[object Object]
Physical Security Risks to IoT Devices
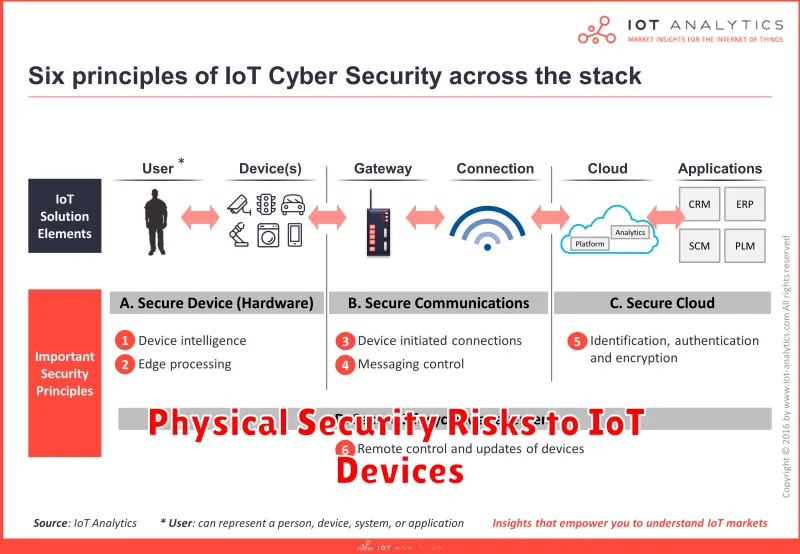
The Internet of Things (IoT) promises a future where everyday objects are seamlessly connected, automating tasks and enhancing our lives. However, this connectivity also opens up new vulnerabilities, particularly in the realm of physical security. As IoT devices become increasingly integrated into critical infrastructure and our personal lives, understanding and mitigating these risks is paramount.
Tampering and Malicious Modification: IoT devices, often deployed in remote or unattended locations, are susceptible to physical manipulation. Attackers can gain unauthorized access by physically tampering with the device, modifying its firmware, or injecting malicious code. This could lead to data theft, system disruptions, or even physical harm.
Data Theft and Espionage: Sensitive data stored on IoT devices can be compromised through physical access. Attackers might steal devices or gain access to their storage to extract confidential information. This risk is heightened in scenarios where IoT devices collect personal data, financial information, or proprietary business intelligence.
Denial of Service (DoS) Attacks: Physical attacks can disrupt the functionality of IoT devices, effectively rendering them unusable. Attackers might disable sensors, damage communication modules, or physically block access to the device, causing significant operational downtime.
Hijacking and Control: Physical access allows attackers to take complete control of IoT devices. This could involve hijacking the device’s communication channels, reprogramming its functionality, or even using it to launch further attacks on connected networks.
Mitigating physical security risks requires a multi-layered approach. This includes robust device authentication mechanisms, secure boot procedures, and tamper-resistant hardware designs. Additionally, implementing physical security measures like secure storage, access control systems, and regular device inspections can help reduce the likelihood of physical attacks.
Best Practices for Securing Your IoT Ecosystem
The Internet of Things (IoT) is rapidly transforming the way we live and work. From smart homes and connected cars to industrial automation and healthcare monitoring, IoT devices are becoming increasingly ubiquitous. However, this proliferation of connected devices also presents significant security challenges. As your IoT ecosystem expands, safeguarding your data and devices becomes paramount. Here are some best practices for securing your IoT ecosystem.
1. Secure by Design: Start with a strong foundation by incorporating security considerations from the very beginning of the design process. Choose devices with robust security features, such as encryption, secure boot processes, and regular security updates. Implement secure development practices to minimize vulnerabilities in your IoT applications.
2. Secure Communication: Protect data in transit by employing encryption protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL). Ensure that all communications between your IoT devices, gateways, and cloud platforms are encrypted. Use strong authentication mechanisms like certificates and digital signatures to verify the identity of devices and users.
3. Secure Access Control: Limit access to your IoT ecosystem and its data to authorized users and devices. Implement granular access control policies that allow specific users to perform specific actions. Regularly audit access permissions and revoke access for any compromised or unused accounts.
4. Patch Regularly: Software vulnerabilities are a constant threat. Regularly update your IoT devices with the latest security patches and firmware updates to address known vulnerabilities. Set up automatic updates whenever possible to ensure timely patching.
5. Implement a Secure Network: Secure your network infrastructure with firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). Segment your network to isolate sensitive IoT devices and prevent lateral movement of attacks. Use strong passwords and multi-factor authentication to protect network access.
6. Continuous Monitoring and Threat Detection: Implement monitoring and security analytics solutions to detect anomalies and potential threats in your IoT ecosystem. Regularly analyze network traffic, device behavior, and security logs to identify suspicious activities. Consider using a dedicated security information and event management (SIEM) system to aggregate and analyze security data from multiple sources.
7. Data Privacy and Security: Comply with data privacy regulations like GDPR and CCPA. Implement encryption, anonymization, and other data protection measures to safeguard sensitive data. Be transparent with users about how you collect, store, and use their data.
Securing your IoT ecosystem requires a multi-layered approach. By adopting these best practices, you can significantly enhance the security of your connected devices and data, mitigating the risks of cyberattacks and data breaches.
Implementing Strong Authentication and Access Control
In the labyrinthine world of the Internet of Things (IoT), security stands as a paramount concern. With interconnected devices exchanging sensitive data, implementing robust authentication and access control mechanisms becomes a critical endeavor. This ensures that only authorized entities can access and manipulate the system, mitigating the risk of unauthorized access, data breaches, and malicious activities.
Multi-Factor Authentication (MFA) is a cornerstone of strong authentication. By requiring multiple forms of authentication, such as a password, a one-time code, or a biometric scan, MFA significantly enhances security. This layered approach makes it significantly harder for unauthorized individuals to gain access to sensitive data or control over devices.
Access Control Lists (ACLs) play a crucial role in limiting access to specific resources based on user roles and privileges. By defining granular permissions, ACLs effectively control who can read, write, or execute specific functions within the IoT ecosystem. This prevents unauthorized users from accessing data or performing actions beyond their allotted scope.
Secure Boot and Device Provisioning are vital for establishing a secure foundation for IoT devices. Secure boot ensures that only trusted software can be loaded during startup, preventing malicious code from hijacking the device. Secure provisioning involves securely configuring devices with necessary certificates and keys, establishing a trusted communication channel from the outset.
Continuous Monitoring and Logging are essential for maintaining situational awareness and detecting potential security threats. By continuously monitoring device behavior and logging critical events, security teams can identify anomalies and react promptly to potential breaches. Regular security audits and vulnerability assessments further strengthen the defense against emerging threats.
Encrypting Data at Rest and in Transit
The Internet of Things (IoT) has revolutionized how we live and work, connecting everything from our homes to our factories. However, this interconnectedness comes with inherent security risks. Data, the lifeblood of IoT systems, is vulnerable to unauthorized access, theft, and manipulation. To address these challenges, strong security measures are crucial, and encryption plays a vital role in protecting data at rest and in transit.
Encryption at Rest refers to protecting data while it’s stored on devices, servers, or other storage mediums. This is achieved using algorithms that transform data into an unreadable format, rendering it inaccessible to unauthorized individuals. Encryption at rest is essential for safeguarding sensitive data like customer information, financial records, and intellectual property.
Encryption in Transit, on the other hand, focuses on securing data as it travels between devices and systems. This is particularly important for IoT devices that communicate over networks, which are susceptible to interception and eavesdropping. Encrypting data in transit ensures that only authorized parties can access it during transmission.
Here are some common encryption methods used in IoT:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s faster than asymmetric encryption but requires secure key management.
- Asymmetric Encryption: Uses separate keys for encryption and decryption. It’s more secure but computationally demanding.
- Homomorphic Encryption: Allows computations on encrypted data without decryption. It’s a promising technology for privacy-preserving data analysis.
By implementing encryption at rest and in transit, organizations can significantly enhance the security of their IoT systems. This involves choosing robust encryption algorithms, securely managing keys, and integrating encryption protocols into their communication infrastructure.
Regularly Updating Firmware and Software
In the ever-evolving landscape of the Internet of Things (IoT), maintaining robust security is paramount. One of the most crucial aspects of securing your IoT devices is ensuring that their firmware and software are regularly updated. These updates often contain critical security patches that address vulnerabilities discovered in previous versions, making it essential for safeguarding your devices and the data they collect.
Firmware updates, specifically, are crucial as they directly impact the device’s core functionality and security. These updates often address vulnerabilities in the device’s operating system, network protocols, and communication mechanisms. Neglecting firmware updates leaves your devices vulnerable to various attacks, including malware infections, unauthorized access, and data breaches.
Similarly, software updates for applications running on IoT devices play a critical role in maintaining security. These updates often incorporate bug fixes, security patches, and improvements to enhance the application’s resilience against attacks. By keeping software up-to-date, you can mitigate the risk of vulnerabilities being exploited by malicious actors.
Regularly updating firmware and software is not a one-time task; it requires a consistent and proactive approach. Establishing a schedule for updates and ensuring that your devices are configured to automatically download and install updates whenever available is a best practice. Implementing robust security measures, such as strong passwords and multi-factor authentication, further strengthens the overall security posture of your IoT ecosystem.
By staying vigilant and embracing a culture of continuous updates, you can effectively navigate the labyrinth of IoT security challenges and protect your connected devices and valuable data.
Conducting Security Audits and Penetration Testing
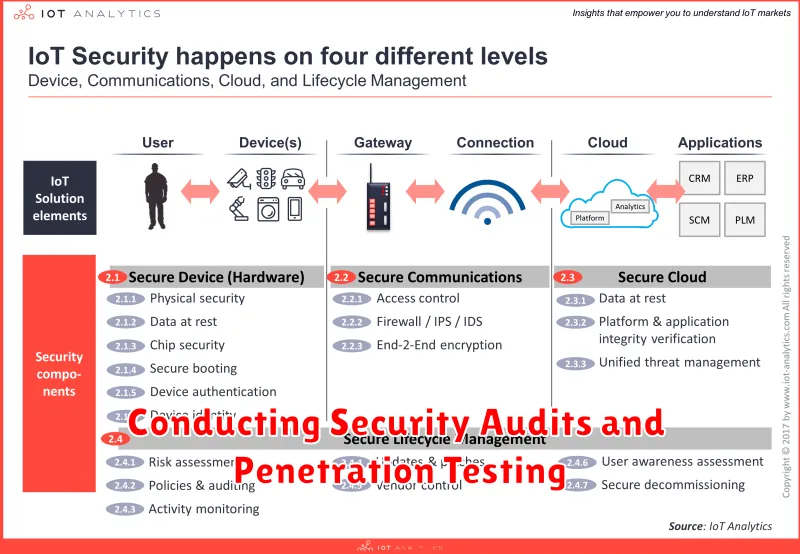
As the Internet of Things (IoT) expands, securing these interconnected devices becomes increasingly critical. To ensure the safety and integrity of your IoT ecosystem, it’s crucial to conduct regular security audits and penetration testing.
Security Audits provide a comprehensive assessment of your IoT infrastructure, identifying vulnerabilities and potential security risks. These audits delve into the design, implementation, and configuration of your devices, networks, and applications. They involve examining code, analyzing network traffic, and identifying weaknesses that could be exploited by attackers.
Penetration Testing, on the other hand, simulates real-world attacks to uncover exploitable vulnerabilities. By attempting to breach your systems, penetration testers can identify weaknesses that might be overlooked during a security audit. These tests help organizations understand their security posture and prioritize remediation efforts.
Conducting security audits and penetration testing for IoT systems presents unique challenges. The diversity of devices, communication protocols, and operating systems necessitates specialized expertise and tools. Moreover, the decentralized nature of IoT environments can make it difficult to gain comprehensive visibility and control.
To effectively conduct security audits and penetration testing in the IoT landscape, consider the following:
- Engage experienced security professionals specializing in IoT security.
- Develop a clear scope and methodology, tailored to the specific characteristics of your IoT environment.
- Utilize specialized tools designed for IoT security testing, such as vulnerability scanners and network traffic analyzers.
- Collaborate with device manufacturers to obtain insights into device security and firmware updates.
- Prioritize remediation of identified vulnerabilities in a timely manner.
By embracing a robust approach to security audits and penetration testing, organizations can enhance the security of their IoT infrastructure, mitigate risks, and protect their data and systems from malicious attacks.
Leveraging AI and Machine Learning for Threat Detection
In the vast and intricate landscape of the Internet of Things (IoT), security stands as a paramount concern. With the ever-increasing number of interconnected devices, vulnerabilities emerge, creating a labyrinth of potential threats. To navigate this complex terrain, artificial intelligence (AI) and machine learning (ML) are emerging as powerful allies in threat detection.
AI and ML algorithms excel at analyzing vast datasets and identifying patterns that might elude human observation. By learning from past attacks and network behavior, these technologies can detect anomalies and suspicious activities in real time. This proactive approach enables organizations to identify and mitigate threats before they escalate into major incidents.
One crucial application of AI and ML is in intrusion detection. By monitoring network traffic and device behavior, these technologies can identify suspicious connections, malicious code execution, and unauthorized access attempts. Furthermore, AI-powered security solutions can analyze data from various sources, including sensors, cameras, and logs, to provide a comprehensive view of potential threats.
Another area where AI and ML shine is in botnet detection. These technologies can identify and isolate botnets by analyzing network traffic patterns, communication protocols, and command-and-control structures. By disrupting botnet activity, organizations can prevent distributed denial-of-service (DDoS) attacks and other forms of malicious activity.
In conclusion, AI and ML are instrumental in bolstering IoT security. By leveraging their capabilities for threat detection, organizations can navigate the labyrinth of vulnerabilities and safeguard their interconnected devices and data. As the IoT ecosystem continues to evolve, the role of AI and ML in securing this critical infrastructure will only become more significant.
The Future of IoT Security: Emerging Trends and Technologies
The Internet of Things (IoT) is rapidly evolving, connecting billions of devices and creating a vast network of interconnected systems. However, this interconnectedness also presents significant security challenges. As the IoT landscape expands, so does the need for robust security measures to protect against emerging threats.
The future of IoT security lies in embracing emerging trends and technologies that can bolster defenses against cyberattacks. Here are some key advancements shaping the future of IoT security:
Zero Trust Security:
Traditional security models often rely on a “trust but verify” approach, assuming devices inside a network are trustworthy. Zero trust security, on the other hand, assumes no device can be inherently trusted and implements strict access controls, authentication, and continuous monitoring for all devices and users. This approach is essential for IoT environments where devices may be vulnerable to attack or compromise.
Artificial Intelligence (AI) and Machine Learning (ML):
AI and ML are playing an increasingly important role in IoT security. These technologies can analyze massive datasets, detect anomalies, and identify potential threats in real-time. AI-powered security solutions can automate threat detection and response, allowing for proactive security measures and swift remediation.
Blockchain Technology:
Blockchain technology offers a secure and transparent platform for managing and verifying data. Its decentralized nature makes it resistant to tampering and manipulation, providing a reliable foundation for secure IoT communications and data storage. Blockchain can be used for secure device authentication, data encryption, and immutable record keeping.
Secure Hardware Design:
Building security into the hardware itself is crucial for protecting IoT devices. Secure hardware design involves incorporating robust security features like secure boot, tamper-resistant processors, and hardware-based encryption. This approach makes it much harder for attackers to exploit vulnerabilities in the device’s hardware.
Edge Computing:
Edge computing brings data processing and analysis closer to the source, reducing latency and improving response times. This decentralized approach can enhance security by minimizing the reliance on centralized servers that may be vulnerable to attack. Secure edge computing environments can process data locally, reducing the risk of data breaches and improving real-time threat detection.
The future of IoT security will require a multifaceted approach that combines these emerging trends and technologies. By embracing these advancements, we can build a more secure and resilient IoT ecosystem that fosters innovation and enables the full potential of interconnected devices.

